How to Install Sqlninja in Kali LinuxSqlninja is a SQL Injection tool. SQL Injections are vulnerable, and Sqlninja exploits online web applications to obtain a remote host's operating shell. The web apps use Microsoft SQL Server as its back-end. Remove access to the vulnerable DB server is provided via Sqlninja. Penetration testers should use the Sqlninja to assist and automate the process of taking over a database server when a SQL Injection vulnerability is detected. In other words, it will automate the exploitation process if it detects a SQL injection. In this tutorial, we will learn how to install Sqlninja in Kali Linux. SqlninjaThe sqlninja tool can help us exploit SQL injection flaws in an application that use Microsoft SQL as the backend database. The main purpose of using the Sqlninja tool is to control the database server through a SQL injection flaw. The Sqlninja tool is a Perl-based database assessment tool that may be found in Kali under Applications | Database Assessments. The Sqlninja tool is designed to exploit an injection flaw to acquire shell access to the database server, not to identify the presence of an injection flaw. Sqlninja RequirementsSqlninja is a Perl script that requires a number of Perl libraries to run properly. So, all we have to do is install Perl and its modules such as:
If we want to utilize the Metasploit attack mode, we must have Metasploit Framework 3 installed on our machine. We'll also need a VNC client to use the VNC payload. We can run the Sqlninja on any Unix-based platform with a Perl interpreter to ensure that all required modules are installed. Sqlninja is available for Unix operating system that has been successfully tested on the following platforms:
Sqlninja does not run-on Windows, so keep that in mind. Sqlninja is released under the terms of the GNU General Public License, version 3.0 (GPLv3). The new version, 0.2.999-alpha1, is released, and data extraction via WAITFOR and DNS tunnel, plus VBscript-based, is added. Also, 0.2.6.r1 is the stable version of Sqlninja, which does not include the data extraction module included in alpha1. Sqlninja FeaturesThe following are the features of Sqlninja:
SQL Injection AttacksOne of the most dangerous attacks on web applications is SQL injection. In addition, it was listed among the Top 10 Web Application Security Threats. When are SQL injection attacks most likely to occur? SQL injection occurs when application processes user-provided data without validating it. As a result, SQL injection can give hackers access to database content or system remote commands. Businesses or organizations use SQL servers to hold secret data. As a result, it is easy to see why hackers would target. Hackers may gain control of the database server as a result of this. Take a look at the list below to see which factors are effective in SQL injection attacks:
Install Sqlninja on Kali LinuxThe database benefits both users and servers by providing a variety of capabilities such as data input storage, large-data retrieval, etc. Hackers and pentesters are continuously looking for a technique to find a gap in a database's security. As a result, we can utilize Sqlninja to take control of the database server by exploiting a SQL injection issue. Let's look at how to install Sqlninja on Kali Linux Server now that we are familiar with Sqlninja and SQL injection. The following steps are used to install sqlninja on Kali Linux: Step 1: In order to install Sqlninja on Kali Linux, first we have to run the following command: 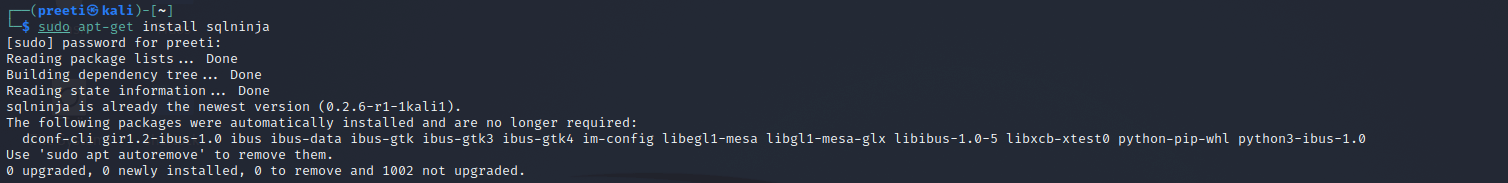
Step 2: We've completed the installation of Sqlninja and all required packages. Use the following command to install all dependencies. 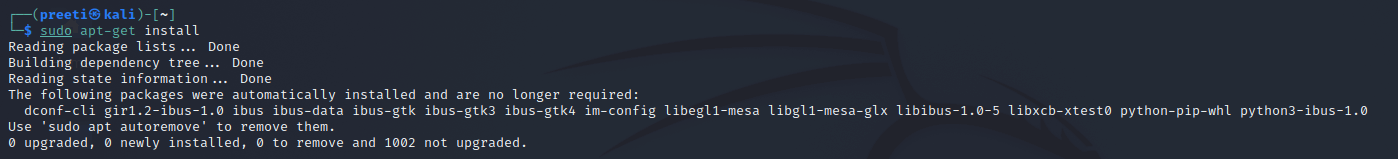
We can find it in Kali by navigating to Applications > Database Assessments. 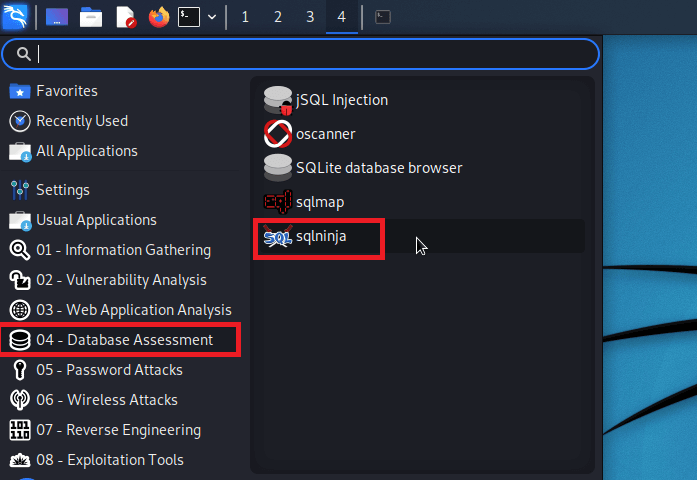
How to Uninstall Sqlninja on Kali LinuxWe can execute the command below to remove Sqlninja at any time. 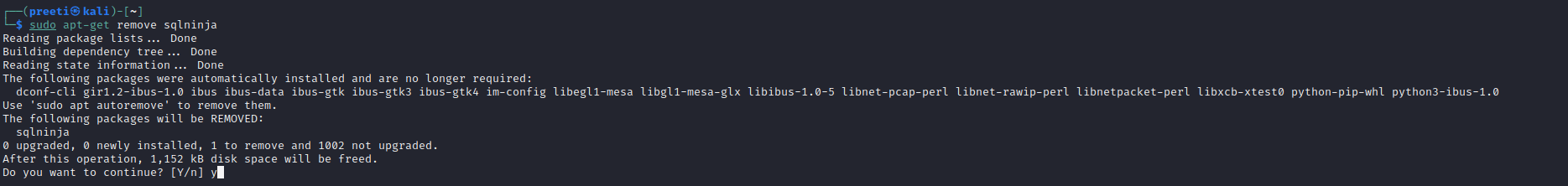
In this manner, we can remove the Sqlninja package itself. We may also uninstall Sqlninja and its dependencies with the command below. 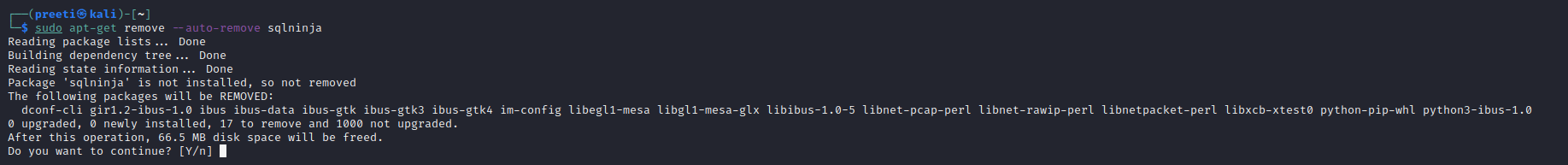
We may also purge our config/data by using the command below: 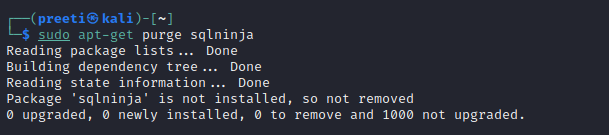
OR 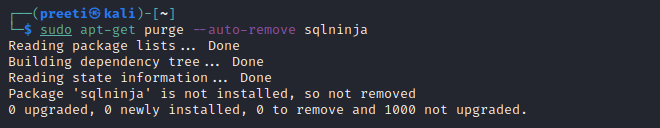
In this manner, we can delete our local/config files for sqlninja.
Next TopicSherlock Tool in Kali Linux
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









