Kali Linux Tutorial
Kali Linux tutorial covers both fundamental and advanced hacking and penetration testing concepts. Our Kali Linux tutorial is designed for both beginners and professionals. Kali Linux tutorial covers all the areas associated with hacking and penetration testing. We'll start by learning how to install the required software. After this, we will learn the network configuration, basic commands and tools for hacking, gaining access, post-exploitation, and website hacking. What is Kali Linux?Kali Linux is a Debian-based Linux distribution that is designed for digital forensics and penetration testing. It is funded and maintained by Offensive Security, an information training company. Kali Linux was developed through the rewrite of BackTrack by Mati Aharoni and Devon Kearns of Offensive Security. Kali Linux comes with a large number of tools that are well suited to a variety of information security tasks, including penetration testing, computer forensics, security research, and reverse engineering. It is a Debian-derived distribution of Linux developed for penetration testing and digital forensics. It is funded and maintained by Offensive Security. Approximately, Kali Linux has 600 penetration testing programs, such as OWASP ZAP web application security scanners and Burp Suite, Airxrack-ng (software suite for wireless penetration-testing LANs), sqlmap (database takeover tool and automatic SQL injection), John the Ripper (password cracker), Metasploit (framework for penetration testing), Wireshark (packet analyzer), Nmap (port scanner), Armitage (a tool for graphical cyber-attack management), etc. It was designed by Devon Kearnsand Mati Aharoniof Offensive Security from the BackTrack rewrite, the old information security testing distribution of Linux based on Knoppix. The title was influenced by the Hindu goddess Kali. It is based on the Debian testing branch. Almost every package Kali uses is imported through the Debian repositories. The popularity of Kali Linux grew at the time it was advertised in two or more Mr. Robot TV series episodes. In the show, tools highlighted and given by Kali Linux contain Wget, Shellshock, Nmap, Metasploit framework, John the Ripper, Bluetooth Scanner, and Bluesniff. The BackTrack and tagline of Kali Linux is "the quieter you become, the more you are able to hear", which is shown on a few backgrounds. Version History of Kali LinuxThe first 1.0.0 "moto" version was published in March 2013. The default user interface was changed from GNOME to Xfce, along with a GNOME version still present in November 2019 with the 2019.4 version. The default shell was changed from Bash to ZSH, along with Bash resting as an option in August 2020 with the 2020.3 version. Supported Platforms of Kali LinuxKali Linux is distributed in 64-bit and 32-bit images for utilization on hosts based on the x86 instruction set and the image for the ARM architecture for utilization on the Beagle Board computer and the ARM Chromebook of Samsung. Kali Linux developers plan to make Kali Linux exist for more ARM devices. Kali Linux is available for SS808, Galaxy Note 10.1, Utilite Pro, Samsung Chromebook, Odroid XU3, Odroid XU, Odroid U2, EfikaMX, Raspberry Pi, CuBox-i, CuBox, CubieBoard 2, HP Chromebook, BeagleBone Black, and Asus Chromebook Flip C100P. Also, Kali Linux is officially present on Android devices like OnePlus One, Nexus 10, Nexus 9, Nexus 7, Nexus 6, Nexus 5, and a few Samsung Galaxy models with the Kali NetHunter arrival. Also, it has been made present for other Android devices from unofficial community builds. It is available on Windows 10 on top of WSL (Windows Subsystem for Linux). The official distribution of Kali for Windows can be installed from the Microsoft Store. Kali Linux Logo
BackTrack was their previous information security operating system. Kali Linux's first version, Kali 1.0.0, was released in March 2013. Kali Linux is now funded and supported by Offensive Security. Today, if we went to Kali's website (www.kali.org), we'd notice a giant banner that states, "Our Most Advanced Penetration Testing Distribution, Ever." A very bold statement that ironically has yet to be disproven. There are over 600 penetration-testing applications preconfigured on Kali Linux for us to explore. Each program has its own set of capabilities and applications. Kali Linux performs a fantastic job of categorizing these important tools into the following groups:
Features of Kali LinuxKali Linux has an embedded project set aside for unity and porting to particular Android devices, known as Kali NetHunter. It's the first open-source penetration testing platform of Android for Nexus devices, established as a joint effort among the Offensive Security and Kali community member "BinkyBear". It supports the 802.11 version of wireless frame injection, Bad USB MITM attacks, HID keyboard, and one-click MANA Evil Access Point setups. Kali's predecessor (BackTrack) included a mode called forensic mode, which was renewed to Kali by live boot. It is very popular for several reasons, partly due to several Kali users already containing a bootable Kali CD or USB drive, and it makes it convenient to use Kali for any forensic job. The system does not touch the swap space or internal hard drive, and auto mounting is deactivated if booted in the forensic mode. Although, the developers suggest that users extensively test these aspects before utilizing Kali for actual world forensics. 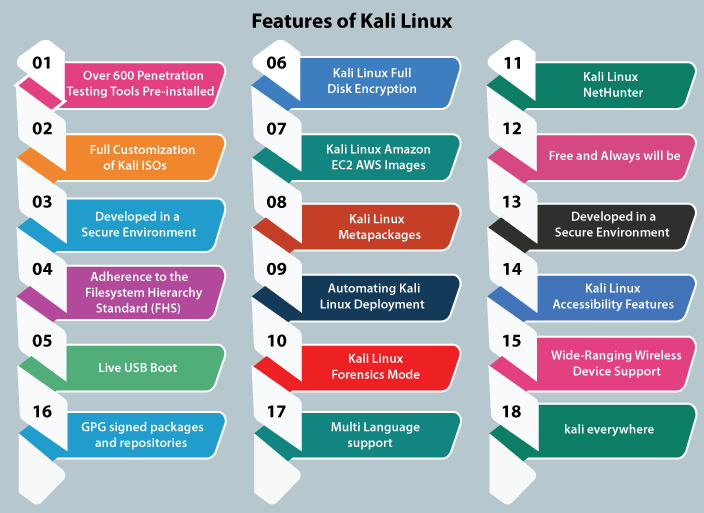
The following are the features of Kali Linux: 1. Over 600 Penetration Testing Tools Pre-installedMore than 600 penetration testing tools come pre-installed in Kali Linux, such as Wireshark, Aircrack-ng, Nmap, and Crunch. 2. Full Customization of Kali ISOsIt is always easy to generate a customized version of Kali for our specific needs using metapackages optimized to the security professional's specific need sets and a highly accessible ISO customization process. Kali Linux is heavily integrated with live-build, giving us a lot of flexibility in customizing and tailoring each aspect of our Kali Linux ISO images. 3. Developed in a Secure EnvironmentThe Kali Linux team consists of a small group of people who are trusted to deliver packages and interact with repositories, all of which is done using a number of secure protocols. 4. Adherence to the Filesystem Hierarchy Standard (FHS)Kali Linux follows FHS (Filesystem Hierarchy Standard) to make it easier to find libraries, support files, etc. 5. Live USB BootThe Live USB boot permits us to place Kali onto a USB device and boot without touching the host operating system (it is also good for forensics work!). Using optional persistence volume(s), we can choose which file system Kali will use when it starts up, permitting for files to be saved in between sessions, generating multiple profiles. Every persistence volume can be encrypted, which is an important feature that our industry requires. If that isn't sufficient, Kali Linux also offers the LUKs nuke option, allowing us to regulate data destruction quickly. 6. Kali Linux Full Disk EncryptionKali Linux LUKS Full Disk Encryption (FDE) can perform full disk encryption of our critical penetration testing computer drive is a must-have tool in the industry. 7. Kali Linux Amazon EC2 AWS ImagesUsing this feature, we can quickly set up a cloud version of the Kali Linux in the Amazon Elastic Compute Cloud, but we will need a lot of bandwidth or disk space for this. 8. Kali Linux MetapackagesKali includes a number of metapackage collections that combine various toolkits. This makes it simple to get custom, minimized environments set up. For example, if we need a few wireless tools for an upcoming assessment, we can apt-get install Kali-Linux-wireless. 9. Automating Kali Linux DeploymentAutomating Kali Linux deployment via Unattended PXE installations- We can automate and customize our Kali Linux installations over the network. We are one PXE boot away from a fresh, custom Kali installation, or 10,000 of them. 10. Kali Linux NetHunterKali Linux NetHunter ROM overlay for Nexus Android devices. Kali Linux is so flexible which creating a "Kali NetHunter" Android was a natural extension of our distribution. NetHunter is a custom Android ROM overlay for ASOP that provides all Kali Linux's toolset to our Nexus or OnePlus phones. 11.Kali Linux Forensics ModeKali's bootable "Forensics" mode is ideal for forensics work because the forensics kali live image option does not mount any drives (including swap) with this option. Kali's forensics tools (metapackage -kali-forensics-tools) make kali an excellent alternative for any forensics task. 12. Free and Always will beLike BackTrack, Kali Linux is free to use and will remain so in the future. Kali Linux is completely free. 13. Kali Linux Accessibility FeaturesKali is one of the few Linux distributions that comprise a working accessibility system for blind or visually impaired users, including voice feedback and braille hardware compatibility. 14. Wide-Ranging Wireless Device SupportA regular sticking point with Linux distributions has been supported for wireless interfaces. Kali Linux is designed to work with as many wireless devices as possible, permitting it to run on a wide range of hardware and make it compatible with numerous USBs and other wireless devices. 15. Custom, Kernel, Patched for InjectionThe development team frequently conducts wireless evaluations as penetration testers, thus our Kernel includes the most recent injection patches. 16. GPG Signed Packages and RepositoriesIn Kali Linux, each package is signed by the developer who built and committed it, and the repositories sign the packages after that. 17. Multi-Language SupportAlthough most penetration tools are written in English, we've ensured that Kali has complete multilingual support, allowing more people to work in their local language and find the tools they require. 18. Kali EverywhereA version of Kali is always close to us, wherever we need it. Mobile devices, ARM, Amazon Web Services, Docker, virtual machines, bare metal, Windows Subsystem for Linux, and more are all available. Kali Linux Comparison with other distributionsKali Linux is designed with an aim toward white-hat hackers, penetration testers, and cyber security experts. There are some other distributions committed to penetration testing, like Wifislax, BlackArch, and Parrot OS. Kali Linux has stood out in opposition to these other distributions for penetration testing and cyber security, as well as having aspects like the default user can be the superuser within the Kali Linux environment. How to Work with Kali Linux GUI?Kali Linux Desktop has some tabs we should remember and become familiar with. These tabs are:
Places Tab: Same as other GUI OSes, like Mac and Windows, easy access to our Pictures, Folders, and My Documents is a necessary component. On Kali Linux, Places gives that accessibility that's essential to any OS. The Places menu contains the below taps by default:
Accessing Places
Applications Tab: It gives a Graphical Dropdown List of every tool and application pre-installed in Kali Linux. Analyzing the Applications Tab is the best way to become known to the featured enriched Kali Linux OS. Accessing Applications
Kali Linux Dock: Same as the Task Bar of Microsoft Windows or Dock of Apple Mac. The Kali Linux Dock gives quick access to favorite/used applications frequently. Applications can be removed or added easily. To delete an element from the dock
To add an element to the dock Adding an element to the dock is very same as deleting an element from the dock. Press the "Show Applications" option at the Dock's bottom.
Who Uses Kali Linux and Why?Kali Linux is a one-of-a-kind operating system since it is one of the few platforms that are freely utilized by both good and bad guys. This operating system is widely used by both Security Administrators and Black Hat Hackers. One is responsible for detecting and preventing security breaches, while the other is responsible for identifying and perhaps exploiting security breaches. The number of tools configured and preinstalled on the operating system makes Kali Linux a Swiss Army Knife in any security professional's toolbox. Professionals that Use Kali Linux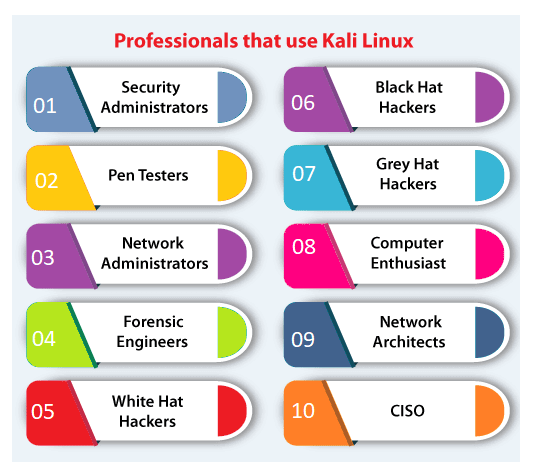
1. Security Administrators Security Administrators are responsible for protecting their institution's information and data. They use Kali Linux to review their environments(s) and ensure there are no easily discoverable vulnerabilities. 2. Pen Testers Pen Testers use Kali Linux to audit environments and perform reconnaissance on corporate environments they've been recruited to examine. 3. Network Administrators Network Administrators are responsible for keeping the network running smoothly and securely. They audit their network with Kali Linux. For example, Kali Linux has the capacity to detect illegitimate access points. 4. Forensic Engineers Kali Linux has a 'Forensic Mode', which permits a forensic engineer to perform data search and recovery in some cases. 5. White Hat Hackers White Hat Hackers, like Pen Testers, utilize Kali Linux to audit and uncover potential vulnerabilities in an environment. 6. Black Hat Hackers Black Hat Hackers use Kali Linux in order to find and exploit vulnerabilities. It contains a number of social engineer applications that a Black Hat Hacker can use to compromise an organization or individual. 7. Grey Hat Hackers Grey Hat Hackers are in the middle of the spectrum between White Hat and Black Hat Hackers. They will use Kali Linux in the same as the two listed above. 8. Computer Enthusiast Computer Enthusiast is a very general term, but anybody interested in learning more about networking or computers can use Kali Linux to better understand IT, networking, and common vulnerabilities. 9. Network Architects Network architects are responsible for designing secure network environments. They use Kali Linux to check their initial designs and make sure nothing was missed or configured incorrectly. 10. CISO CISO (Chief Information Security Officers) utilizes Kali Linux to audit their environment internally and find out if any new applications or rouge configurations have been installed. Why Use Kali Linux?There are a variety of reasons why Kali Linux should be used. Here are some of the reasons why Kali Linux is an intriguing operating system to use: 1. It is FreeKali Linux is free for download. 2. A plethora of tools availableKali Linux includes over 600 tools for penetration testing and security analytics. 3. Completely CustomizableThe developers at offensive security understand that not everyone will agree with their design model, so they've made it as simple as possible for the more exploratory user to customize Kali Linux to their taste, even down to the kernel. 4. Open-SourceKali Linux is available on an open-source platform because it is part of the Linux family. The whole development tree and the code are known to be viewed and modified on Git. 5. Multi-Language SupportDespite the fact that penetration tools are typically written in English, it has been ensured that Kali includes true multilingual support, allowing more users to work in their local language and find the tools they require. System Requirements for Kali LinuxKali is really simple to install. All we have to do is ensure that we have the right hardware. Platforms that support it include i386, amd64, and ARM (both ARMEL and ARMHF). We are ready to run Kali Linux if we have any of the above hardware. Furthermore, the more powerful the hardware, the greater the performance.
PrerequisiteBefore learning Kali Linux, we must have a basic understanding of computer fundamentals. AudienceThis Kali Linux tutorial is designed for people interested in pursuing their career in information security or those who are already working as network security professionals or want to add a new skill to their resume. ProblemWe guarantee that you will not find any difficulties in this Kali Linux tutorial. However if there is any mistake, please post the problem in contact form.
Next TopicKali Linux Installation
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










