Context based Access Control (CBAC)Access-lists (ACL) have recently been used for packet filtering and protection. ACL operates using the administrator's list of rules in order. The regulations include a number of permit and deny requirements. The only drawback of ACL is that it only filters traffic at the transport layer. Therefore, a Cisco router with the appropriate IOS version is used for low-cost firewall functionality. There are two ways to implement an IOS-based firewall:
Context access based control (CBAC) -In contrast to how ACLs protect and filter traffic at the transport layer, CBAC extends that protection to the application layer. The router can function as a firewall with CBAC configuration. Working -While CBAC only functions as a reflexive Access-list, it also keeps a state table where the sessions are stored in memory. A dynamic entry is added to the state table and outbound (going out) traffic is permitted to pass through the router when a session is started by a device within the network (IoS based firewall). As the router (an IoS-based firewall) has an entry for traffic initiated within the network, it can pass the reply of outbound traffic with the aid of this entry. The IoS-based firewall CBAC mechanism accomplishes this by temporarily opening gaps in the access list (applied to the inbound traffic) to let reply packets through. ACLs are a set of rules for regulating network traffic and minimising network attacks. Using a set of rules specified for the network's incoming or outgoing traffic, ACLs are used to filter traffic. Features -The CBAC has some features, including:
Configuration -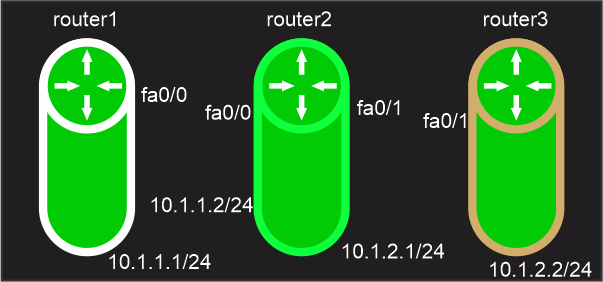
There are three routers: router1 (10.1.1.1/24 on fa0/0), router2 (10.1.1.2/24 on fa0/0 and 10.1.2.1/24 on fa0/1) and router3 (10.1.2.2/24). To enable pinging between routers, we will first assign routes via EIGRP to every router. Following that, we will configure router 3 as an ssh server, and router 2 (on which CBAC will be running) will only permit traffic after it has been examined by router 2. Setting up EIGRP on router 1 initially: Next, set up EIGRP on router 2 to connect to other networks: Now, configuring eigrp on router3: We will now set up SSH on router 3: On router 2, we will now create an Access-list through which we will block all traffic aside from EIGRP because EIGRP ensures that all routers can still communicate with one another. Applying it now to the user interface: Now that we have applied access-list, which will only accept Eigrp packets and deny all other packets, router1 will no longer be able to ssh router3. Now, set up CBAC on router 2 to examine ssh traffic (Only traffic that will be examined by the IoS router operating CBAC will be permitted.) While the second command will examine the ssh traffic, the first command (!cbac) will enable the cbac feature. Now, examining the interface through inspection Now that the ssh packet has been examined by router2 before leaving the outbound (fa0/1) interface, router1 will be able to ssh router3 (as we have configured). This is corroborated by: Note: Because we only want traffic coming from outside the network that was started by the inside network, Access-list has been applied inbound and CBAC has been applied out (10.1.1.1). To temporarily allow return packets to pass through the Access-list applied to the interface (into fa0/1) when CBAC is applied outbound, temporary holes are created on the ACL.Limitations -Some of the cbac mechanisms' drawbacks include:
Next TopicCristian's Algorithm
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










