Transport Layer Security | Secure Socket Layer (SSL) and SSL ArchitectureTransport Layer SecurityThe application layer, which makes use of TCP (or SCTP) as a connection-oriented protocol, is actually secured by the transport layer, which also offers security for that layer. These apps' messages are first enclosed in security protocol packets before being contained in TCP. Due to the nature of security, which necessitates connection formation between the two entities, apps that employ UDP cannot take advantage of these security services. The transport-layer security does not apply to electronic mail (e-mail), which is another application. We need a particular security provision for this application because it only allows one-way communication between the sender and the receiver. This is covered in the below section. The Secure Sockets Layer (SSL) and the Transport Layer Security (TLS) protocols are currently the two most used ones for delivering security at the transport layer. Actually, the latter is a modified version of the former by the IETF. TLS is extremely similar to SSL, which is covered in this section. The location of TLS and SSL in the Internet paradigm is depicted in the image below: 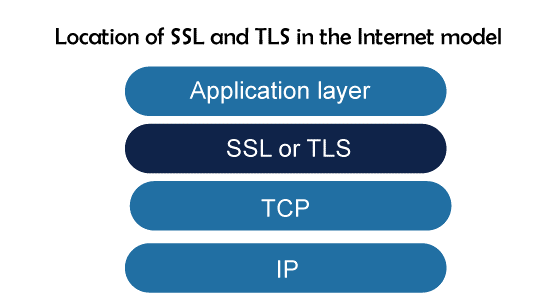
These protocols aim to guarantee data secrecy, data integrity, and server and client authentication, among other things. Applications-layer client/server programs that employ TCP services, like HTTP, can encapsulate their data in SSL packets (HTTPS). In order to allow HTTP messages to be encased in SSL (or TLS) packets, the client can use the URL https://... rather than http://... if the server and client are both capable of executing SSL (or TLS) programs. For example, banking information can be safely exchanged over the Internet for online buyers. Socket Security Layer (SSL) ArchitectureIn order to secure and compress data produced at the application layer, SSL was created. Any application-layer protocol can send data via SSL in most cases; however, HTTP is the most used one. The program sends back data that has been signed, encrypted, and compressed (optional). A trustworthy transport-layer protocol, such as TCP, receives the data at this point. In 1994, SSL was created by Netscape. In 1995, versions 2 and 3 were made available. SSLv3 is discussed in this section. Services Offered by SSL:On data that has been received from the application layer, SSL offers a number of services:
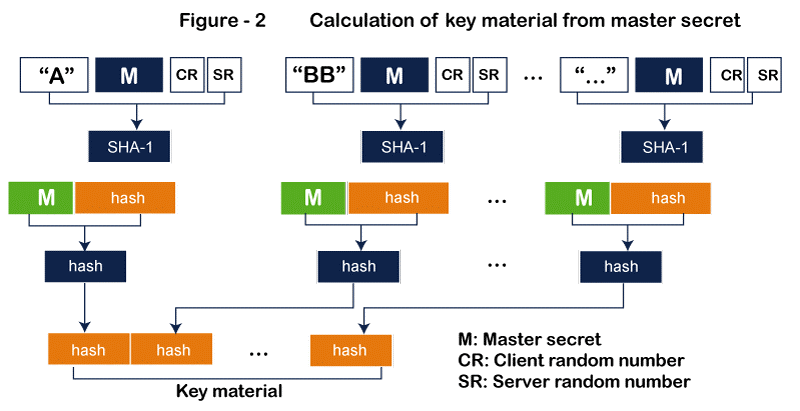
Key Exchange Algorithm - Each of the clients and servers must have a unique set of cryptographic secrets in order to exchange an authorized and confidential communication. One pre-master secret must first be created between the two parties in order to produce these secrets, though. This pre-master secret is established using one of the key-exchange protocols specified by SSL. Encryption/Decryption Algorithm - A set of encryption and decryption techniques must also be agreed upon by both the client and the server. Hash Algorithm - Hash algorithms are used by SSL to ensure message integrity (message authentication). For this reason, a number of hash algorithms have been defined. Cipher Suite - Each SSL session has a unique cypher suite that is defined by the interaction of the key exchange, hashing, and encryption algorithms. Compression Algorithm - In SSL, compression is not required. There is no defined compression algorithm. Consequently, a system is free to employ any compression strategy it chooses. Cryptographic Parameter Generation - SSL requires six cryptographic secrets: two IVs (initialization vectors) and four keys, ensuring message integrity and confidentiality. For message authentication, encryption, and use as the initial block in calculations, the client needs one key for each. The server also requires it. A requirement of SSL is that the keys used in one direction and the other direction be distinct. The opposite way is unaffected by an attack coming from one direction. The process used to produce the parameters is as follows:
Sessions and Connections - A connection and a session are distinguished by SSL. A client and server are connected through a session. Following the establishment of a session, the two parties share data such the session identification, the certificate validating each of them (if necessary), the compression technique, the cypher suite, and a master secret that is used to generate keys for message authentication encryption. The creation of a session is required, but not sufficient for two entities to communicate with one another and exchange data. The two parties exchange two random integers while generating the keys and parameters required for transmitting messages including authentication and privacy using the master secret. 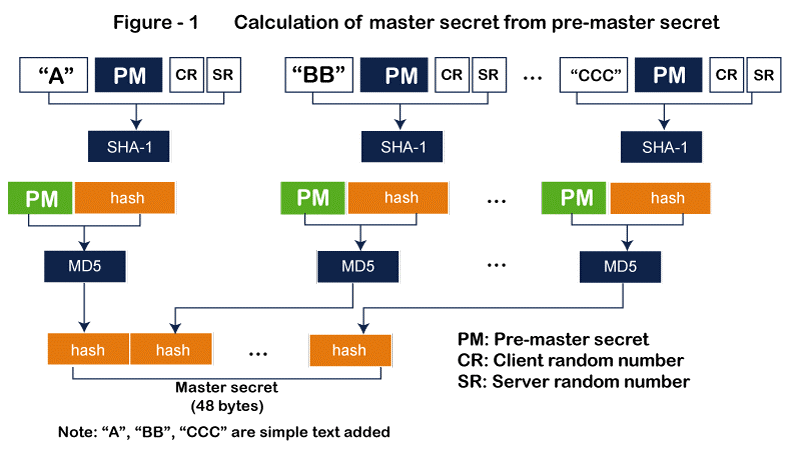
There may be numerous connections inside a session. Within the same session, a link between two participants can be broken and then repaired. The two parties can choose to end the session when the connection is cut off, although it is not required. A session may be stopped and started again. 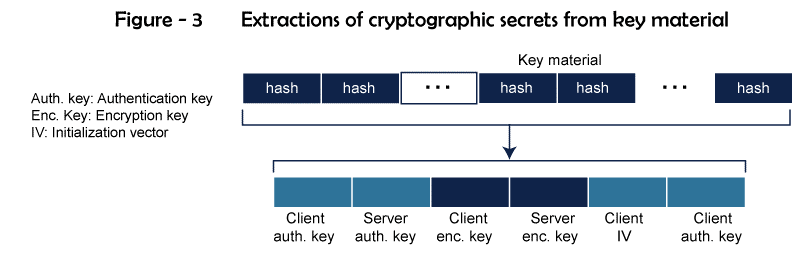
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









