Design Issues for the Layers of Computer NetworksIntroductionComputer networks are the lifelines of our digital era, supporting the flow of information, data, and communication across a wide range of devices and in an increasingly linked world. However, the complicated web of interconnected networks that enables our daily interactions and global connectedness is anything from simple. To ensure the seamless operation and scalability of computer networks, one must delve into the intricacies of design issues that span the layers of these intricate systems. 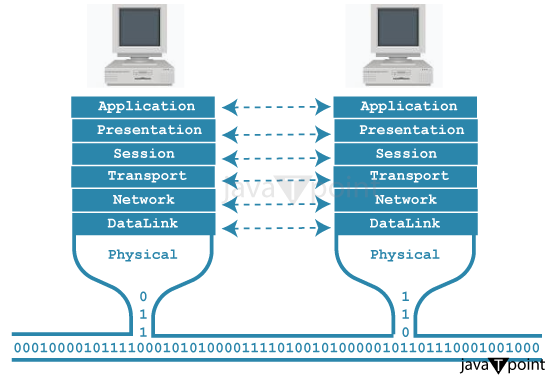
The design issues in computer network layers are not mere technical details; they are the foundation upon which the reliability, security, and efficiency of our digital interactions are built. In this comprehensive exploration, we will dissect the critical challenges that network architects and engineers must address to craft networks that function smoothly and adapt to the ever-evolving landscape of technology. In this read, we will look into the problems that might occur while designing the network. 1. ReliabilityReliability is a cornerstone design issue in computer networks. Networks are composed of various components, and some of these components may be inherently unreliable, leading to potential data loss during transmission. Ensuring that data is transferred without distortion or corruption is paramount. Robust error detection and correction mechanisms are essential for preserving data integrity, especially in the face of unreliable communication channels. 2. AddressingAddressing is a fundamental aspect of network layers. In a network, numerous processes run on multiple machines, and each layer requires a mechanism to identify both senders and receivers accurately. Effectively assigning and managing addresses helps facilitate efficient communication, ensuring that data reaches its intended destination. 3. Error ControlThe inherent imperfections in physical communication circuits necessitate error control as a vital design issue. To safeguard data integrity, error-detecting and error-correcting codes are employed. However, it's imperative that both the sending and receiving ends reach a consensus on the specific error detection and correction codes to be used, ensuring effective data packet protection. 4. Flow ControlMaintaining an equilibrium between data senders and receivers is essential to prevent data loss due to speed mismatches. A fast sender transmitting data to a slower receiver necessitates the implementation of a flow control mechanism. Several approaches are used, such as increasing buffer sizes at receivers or slowing down the fast sender. Additionally, the network should handle processes that cannot accommodate arbitrarily long messages by disassembling, transmitting, and reassembling messages as required. 5. Multiplexing and De-multiplexingEfficient data transmission on a network often involves transmitting data separately on the transmission medium. Setting up separate connections for every pair of communicating processes is neither practical nor cost-effective. To address this challenge, multiplexing is employed at the sender's end, allowing data from multiple sources to be combined into a single transmission stream. De-multiplexing is then performed at the receiver's end to separate and direct the data to the appropriate recipients. 6. ScalabilityAs networks expand in size and complexity, new challenges inevitably arise. Scalability is crucial to ensuring that networks can continue to function effectively as they grow. The network's design should accommodate increasing sizes, reducing the risk of congestion and compatibility issues when new technologies are introduced. Scalability is a cornerstone for ensuring the network's long-term viability. 7. RoutingRouting is a critical function within the network layer. When multiple paths exist between a source and destination, the network must select the most optimal route for data transmission. Various routing algorithms are utilized to make this determination, with the aim of minimizing cost and time, thereby ensuring efficient and reliable data transfer. 8. Confidentiality and IntegrityThe security of a network is critical. Confidentiality methods are critical for protecting against risks like eavesdropping and preventing unauthorized parties from accessing sensitive data. Data integrity is also crucial since it protects against tampering and unauthorized changes to messages during transmission. 9. Service Quality (QoS):QoS refers to a network's ability to deliver varying levels of service to different types of traffic. Video streaming, VoIP, and data transmission all have varying bandwidth, latency, and reliability needs. It is a difficult challenge to ensure that the network can prioritize and distribute resources effectively to satisfy these objectives. 10. Network management:Network management includes monitoring and maintaining the health and performance of different network components such as routers, switches, and servers. Device configuration, fault detection, performance analysis, and security monitoring all need network management tools and protocols. Effective network administration is critical for detecting and resolving problems in real time, optimizing resource utilization, and maintaining a positive user experience. 11. Load Balancing:In scenarios where a network has multiple servers or paths to handle incoming traffic, load balancing becomes critical. The challenge is to distribute network traffic evenly across these resources to prevent overloads and optimize resource utilization. Load balancing can be achieved through hardware or software solutions, and it may require advanced algorithms to make intelligent decisions based on factors like server health and current traffic loads. 12. Network Topology Design:The choice of network topology can significantly impact the network's performance, scalability, and fault tolerance. Designing the right topology for a given scenario involves considering factors such as cost, reliability, ease of expansion, and fault tolerance. For example, a star topology might be suitable for a small office network, while a mesh or hybrid topology could be preferred for a large-scale data center. 13. Energy Efficiency:With increasing concerns about energy consumption and its environmental impact, designing energy-efficient networks is essential. This includes using energy-efficient hardware, optimizing network protocols, and implementing strategies for turning off or reducing power to unused network components during periods of low demand. Energy-efficient network design helps reduce operational costs and minimizes the carbon footprint. 14. Interoperability:It is a huge task to ensure that these components can function together seamlessly. Adherence to industry standards and protocols, as well as testing and certification processes, are used to achieve interoperability. It's crucial to ensure that data can flow smoothly between diverse network elements. 15. Virtualization and Network Function Virtualization (NFV):Network virtualization involves creating virtual instances of network components and services, such as virtual routers and firewalls. Managing these virtual networks, ensuring their security, and dynamically scaling resources to meet changing demands is a complex task. Network Function Virtualization (NFV) extends this concept by virtualizing network functions like firewalls and load balancers, enabling flexible and cost-effective service delivery. 16. Mobile and Wireless Networks:As the use of mobile devices and wireless connections continues to grow, designing networks that provide seamless connectivity as users move between different access points is a challenge. This involves implementing mobility management protocols, handover procedures, and efficient spectrum management to prevent interference and optimize wireless performance. 17. Legacy Systems Integration:Many existing networks include legacy systems and technologies that must be integrated with modern networking solutions. This can be complex because older systems may not support the latest standards and security protocols. Network designers must ensure compatibility while maintaining security during the integration process. 18. Disaster Recovery and Redundancy:Planning for network resilience in the face of disasters, equipment failures, or cyberattacks is critical. Redundancy, failover mechanisms, and disaster recovery strategies must be in place to maintain network continuity. This involves duplicating critical components, creating backup data centers, and implementing data backup and recovery solutions. 19. IoT and Edge Computing:With the proliferation of Internet of Things (IoT) devices and the adoption of edge computing, networks must handle a massive number of connected devices and process data at the edge of the network. This presents challenges related to device management, data processing, and ensuring security and privacy for IoT devices. 20. Compliance and Regulatory Issues:Networks often need to comply with specific regulations and industry-specific standards, such as data privacy laws (e.g., GDPR) or compliance requirements for industries like healthcare or finance. Meeting these requirements involves implementing security measures, data encryption, and auditing processes to ensure network compliance while avoiding legal and financial penalties. These problems reflect the evolving nature of computer networks and the diverse demands placed on them in a constantly changing technological landscape. Network designers must consider these challenges to create robust, efficient, and secure network architectures. ConclusionIn conclusion, the design issues for the layers of computer networks are multifaceted, encompassing reliability, addressing, error control, flow control, multiplexing, scalability, routing, and network security. Successful network design requires a delicate balance between addressing these challenges while adapting to the ever-evolving landscape of network technologies and user demands. Careful consideration of these design issues is essential to maintaining efficient and error-free data transmission in modern computer networks.
Next TopicWhat is AMD (Advanced Micro Devices)
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









