SSH Meaning| SSH Protocol DefinitionSSH stands for Secure Shell or Secure Socket Shell. It is a cryptographic network protocol that allows two computers to communicate and share the data over an insecure network such as the internet. It is used to login to a remote server to execute commands and data transfer from one machine to another machine. The SSH protocol was developed by SSH communication security Ltd to safely communicate with the remote machine. Secure communication provides a strong password authentication and encrypted communication with a public key over an insecure channel. It is used to replace unprotected remote login protocols such as Telnet, rlogin, rsh, etc., and insecure file transfer protocol FTP. Its security features are widely used by network administrators for managing systems and applications remotely. The SSH protocol protects the network from various attacks such as DNS spoofing, IP source routing, and IP spoofing. A simple example can be understood, such as suppose you want to transfer a package to one of your friends. Without SSH protocol, it can be opened and read by anyone. But if you will send it using SSH protocol, it will be encrypted and secured with the public keys, and only the receiver can open it. Before SSH: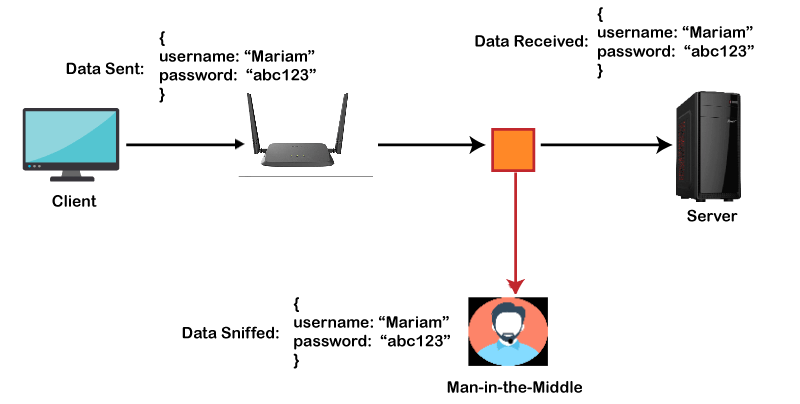
After SSH: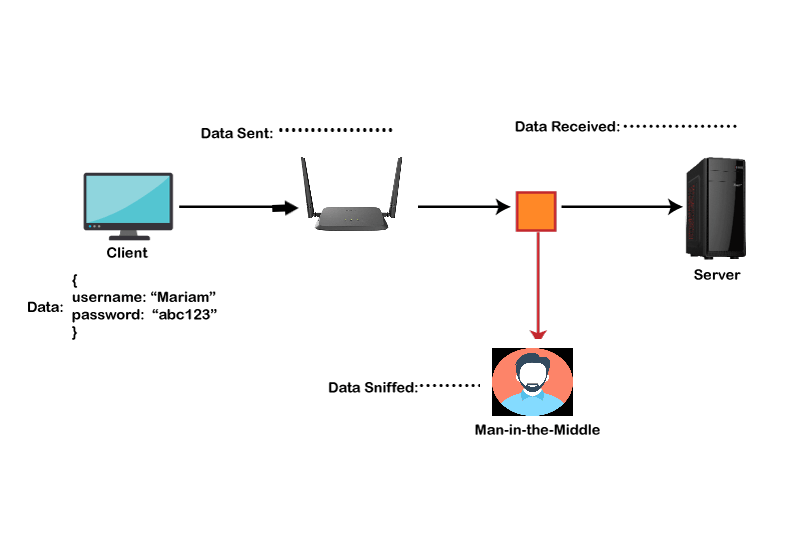
Usages of SSH protocolThe popular usages of SSH protocol are given below:
How does SSH Works?The SSH protocol works in a client-server model, which means it connects a secure shell client application (End where the session is displayed) with the SSH server (End where session executes). As discussed above, it was initially developed to replace insecure login protocols such as Telnet, rlogin, and hence it performs the same function. 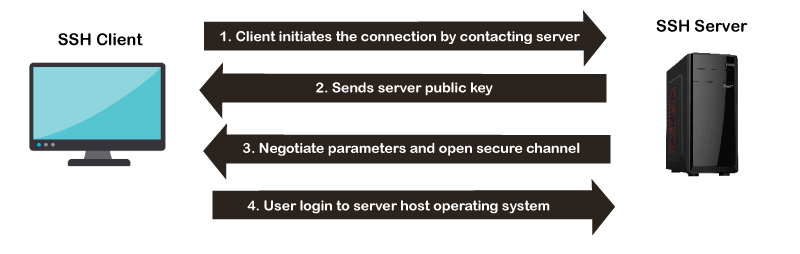
The basic use of SSH is to connect a remote system for a terminal session and to do this, following command is used: The above command enables the client to connect to the server, named server.test.com, using the ID UserName. If we are connecting for the first time, it will prompt the remote host's public key fingerprint and ask to connect. The below message will be prompt: To continue the session, we need to click yes, else no. If we click yes, then the host key will be stored in the known_hosts file of the local system. The key is contained within the hidden file by default, which is /.ssh/known_hosts in the home directory. Once the host key is stored in this hidden file, there is no need for further approval as the host key will automatically authenticate the connection. History of SSH ProtocolThere are 3 versions of SSH, which are given below:
The architecture of SSH ProtocolThe SSH architecture is made-up of three well-separated layers. These layers are:
The SSH protocol architecture is an open architecture; hence it provides great flexibility and enables SSH use for many other purposes instead of only a secure shell. In the architecture, the transport layer is similar to the transport layer security (TLS). The User-authentication layer can be used with the custom authentication methods, and the connection layer allows multiplexing different secondary sessions into a single SSH connection. Transport LayerThe transport layer is the top layer of the TCP/IP protocol suite. For SSH-2, this layer is responsible for handling initial key exchange, server authentication, set up encryption, compression, and integrity verification. It works as an interface for sending and receiving plaintext packets with sizes up to 32, 768bytes. User authentication LayerAs its name suggests, the user authentication layer is responsible for handling client authentication and provides various authentication methods. The authentication is done at the client-side; hence when a prompt occurs for a password, it usually for an SSH client rather than a server, and the server responds to these authentications. This layer includes various methods of authentication; these methods are:
Connection LayerThe connection layer defines various channels through which SSH services are provided. It defines the concept of channels, channel requests, and global requests. One SSH connection can host different channels simultaneously and can also transfer data in both directions simultaneously. Channel requests are used in the connection layer to relay out-of-band channel-specific data, for example, the altered size of a terminal window or the exit code of a server-side process. The standard channel types of connection layer are:
What can be transferred with SSH protocol?The SSH protocol can transfer the following:
The files are transferred using the SFTP(Secure file transfer protocol), the encrypted version of FTP that provides security to prevent any threat. Difference between SSH and Telnet
SSH Encryption TechniquesTo make a secure transmission, SSH uses three different encryption techniques at various points during a transmission. These techniques are:
Symmetrical EncryptionOnly one key can be used in symmetric encryption techniques to encrypt & decrypt messages sent and received from the destination. This technique is also known as shared key encryption because both devices use the same key to encrypt the data they send and decrypt the received data. This technique encrypts the entire SSH connection to prevent man-in-middle attacks. In this technique, one issue arises at the time of initial key exchange. As per this problem, if a third party is present during the key exchange, they could know the key and read the entire message. The Key exchange algorithm is used to prevent this problem. With this algorithm, the secret keys can be securely exchanged without an interception. Asymmetrical encryption is required to implement the key exchange algorithm. Asymmetrical EncryptionIn asymmetrical encryption, two different keys are used for encryption and decryption, private and public keys. The private key is private to the user only and cannot be shared with any other user, whereas the public key is shared publicly. The public key is saved on the SSH server, whereas the private key is saved locally on the SSH client; these two keys form a key pair. The message encrypted with the public key can only decrypt with the corresponding private key. It is a much secure technique as if a third party gets the public key, and they cannot decrypt the message because they don't know the private key. The asymmetrical encryption does not encrypt the complete SSH session. Instead, it is mainly used for the key exchange algorithm of symmetric encryption. In this, before establishing a connection, both systems (client and server) generate public-private key pairs temporarily and then share their private keys to generate the shared secret key. After establishing a secure symmetric connection, the server uses the public key to transmit it to the client for authentication. The client can only decrypt the data if it has the private key, and hence the SSH session establishes. HashingIn SSH, one-way hashing is used as the encryption technique, which is another form of cryptography. The hashing technique is different from the above two methods, as it is not meant by decryption. It generates the signature or summary of information. SSH uses HMAC(Hash-based Message authentication) to ensure that messages are reached in complete and unmodified form. In this technique, each transmitted message must have a MAC, which uses three components: symmetric key, packet sequence number, and message content. These three components form the hash function that generates a string that doesn't have any meaning, and this string is sent to the host. The host also has the same information, so they also generate a hash function, and if the generated hash matches with the received hash, it means the message is not tempered.
Next TopicUTP vs STP
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









