MAC Filtering
In the world of laptop networks, ensuring robust protection is a paramount situation. Community directors deploy many security features to shield opposition from unauthorized get admission to and capacity for cyber threats. One such approach is MAC Filtering, a powerful get-entry to manipulate the mechanism. In this text, we can explore MAC Filtering and apprehend its operating standards, blessings, and capability limitations.
What is MAC Filtering?
MAC (Media Access Control) Filtering is a security feature generally located in community devices like routers and switches and gets entry to points. It operates at the OSI version's records link layer (Layer 2) and entails controlling access to the network-based totally on the physical MAC cope with of a tool. Every community interface, whether wired or wireless, possesses a unique MAC deal assigned by the producer. This 12-digit hexadecimal identifier is a device's particular identifier in a community.
How does MAC Filtering work?
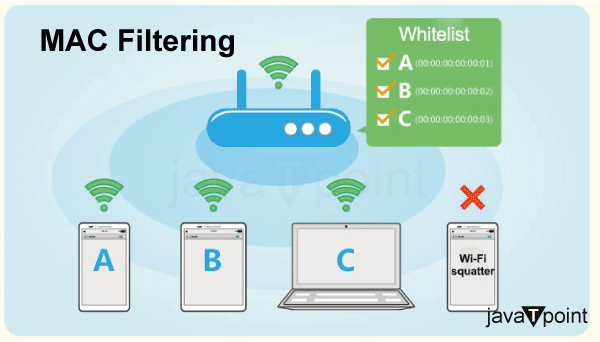
The MAC Filtering system entails three number one components:
- MAC Whitelisting: This approach entails growing a whitelist of accredited MAC addresses. Only devices with MAC addresses indexed on this whitelist are granted community access. Any tool connecting with the community with an accredited MAC address is allowed entry.
- MAC Blacklisting: Conversely, this method entails a blacklist of MAC addresses. Devices on this listing are denied network access rights, while all devices can join. This technique is less common than MAC whitelisting and is usually used to dam precise devices.
- Filter Modes: MAC Filtering may be implemented in two modes:
- Allow mode: Only devices on the whitelist (or no longer on the blacklist) are allowed community access.
- Deny mode: Devices on the blacklist (or no longer on the whitelist) are denied community access.
Advantages of MAC Filtering:
- Enhanced Network Security: MAC Filtering presents an extra layer of safety to networks by permitting only authorized gadgets with approved MAC addresses to attach. This can help prevent unauthorized get right of entry and capacity protection breaches.
- Simple Implementation: Setting up MAC Filtering is notably clean, as maximum current routers and get admission to points have built-in configuration alternatives for this selection. Network administrators can quickly manage the listing of allowed or blocked gadgets.
- Low Overhead: Since MAC Filtering operates at the statistics hyperlink layer (Layer 2) of the OSI model, it minimizes community performance. It doesn't require extra processing for better-degree protocols, making it green and unobtrusive.
- Device-Specific Control: MAC Filtering permits administrators to work out a unique management over which devices can access the network. This feature is specifically valuable for eventualities in which the most straightforward specific gadgets should be permitted to connect.
- Additional Deterrent: While MAC addresses may be modified or spoofed, MAC Filtering can nevertheless serve as a deterrent to casual intruders or unauthorized customers. It provides an additional step for capacity attackers, discouraging them from attempting to breach the network.
Disadvantages of MAC Filtering:
- MAC Spoofing: MAC addresses may be without difficulty spoofed or changed, making MAC Filtering liable to assaults. Skilled attackers can manage their MAC addresses to impersonate authorized gadgets and benefit from unauthorized entry to the network.
- Administrative Overhead: In large networks with an extensive quantity of devices, coping with the MAC cope with whitelist can become bulky. As devices are introduced or changed, everyday updates to the whitelist are a vital, growing administrative burden.
- Lack of Granularity: MAC Filtering most straightforward controls get admission primarily based on MAC addresses, without thinking about other factors like personal identities or context. This issue means that it is not appropriate for networks that require greater granular access control based on consumer roles or device sorts.
- Inflexible: MAC Filtering may be overly restrictive, especially in environments in which devices often alternate or whilst visitors need transient networks to get the right of entry. Adding new devices to the community may require guide intervention to replace the whitelist.
- Limited Protection Against Internal Threats: MAC Filtering basically makes a specialty of external threats, along with unauthorized devices attempting to connect to the community. However, it no longer provides safety against threats originating from within the network, such as malware-inflamed gadgets.
Applications of MAC Filtering:
MAC Filtering, which controls community get right of entry primarily based on MAC addresses, unearths applications in diverse eventualities to decorate protection, network control, and manipulation. Some of the critical applications consist of the following:
- Wireless Network Security: MAC Filtering is usually used in Wi-Fi networks to improve protection by permitting the most straightforward gadgets with authorized MAC addresses to connect with the Wi-Fi entry to factor. This facilitates saving you from unauthorized entry and strengthens general community safety.
- Guest Networks: In environments in which visitor admission is granted, MAC Filtering may be employed to create a whitelist of permitted MAC addresses for guest gadgets. This guarantees that the most effective legal guests can hook up with the network while keeping the leading community steady from ability threats.
- BYOD (Bring Your Own Device) Policies: In organizations that permit personnel to use their private devices on the company network, MAC Filtering can be used to manage and control which devices are allowed to connect. This enables in implementing of security rules and lowering the risk of unauthorized get right of entry.
- IoT Device Management: The proliferation of Internet of Things (IoT) gadgets brings protection to demanding situations. MAC Filtering may be applied to get admission to IoT gadgets, ensuring that the best-authorized gadgets can connect with the community, stopping unauthorized access, and decreasing the assault surface for cyber threats.
- Parental Controls: At home, MAC Filtering may be a part of parental control measures to limit the net right of entry to particular gadgets used by youngsters. By growing a whitelist of permitted devices, dads and moms can control and restrict their children's online sports.
- Public Wi-Fi Hotspots: In public Wi-Fi networks, MAC Filtering is used to manipulate access and prevent unauthorized use. Approved MAC addresses are allowed to get admission. At the same time as unapproved gadgets are denied the connection, improving the security of the hotspot.
- Network Segmentation: In large corporations with a couple of departments or user corporations, MAC Filtering can be used to phase the network. Each phase may have its very own MAC address whitelist, enhancing network business enterprise and improving safety by controlling get entry to among segments.
- Device-Based Authentication: MAC Filtering can be included in the authentication method, permitting devices with particular MAC addresses to skip extra authentication steps. This may be useful for particular trusted gadgets, streamlining the login technique.
- Restricting Access to Specific Devices: MAC Filtering allows community administrators to manipulate and get admission to particular devices or devices. For example, in a network with printers, scanners, or different shared assets, MAC Filtering can make sure that the handiest authorized gadgets can make use of these resources.
- Preventing Unauthorized Network Usage: In environments in which community usage is precisely regulated, MAC Filtering can be used to enforce compliance with the aid of allowing admission to only legal gadgets and stopping unauthorized connections.
|

 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now









