Communication Protocols In System DesignCommunication protocols in system design refer to a collection of rules, norms, and standards that control how various components within a system or between several systems communicate information and data. These protocols establish the format, timing, sequencing, error control, and security mechanisms required for effective data transmission and reception. 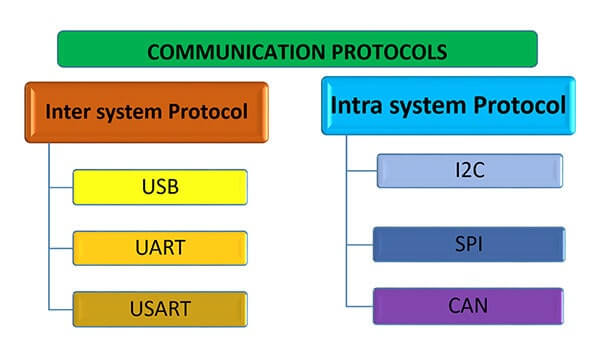
Communication protocols are essential in system architecture because they provide the smooth interaction and interoperability of diverse hardware and software pieces. They let devices, applications, and systems interact successfully despite variations in design, programming languages, or functionality. The following are important characteristics of communication protocols in system design:
Communication ProtocolI. TCP/IP (Transmission Control Convention/Web Convention):A fundamental set of networking protocols forms the basis for communication between private networks and the Internet. As a matter of fact, it is a bunch of conventions, instead of a solitary norm, that incorporates a few levels to allow information transmission between gadgets across connected networks. A summary of its primary components is as follows: TCP (Transmission Control Convention):
Internet Protocol (IP):
TCP and IP operate together to facilitate data transfer across networks:
II. HTTP (Hypertext Move Convention)HTTP (Hypertext Move Convention) is an application-layer convention that fundamentally permits correspondence between internet browsers and web servers. It is the reason for information trade on the Internet, empowering the recovery of assets like HTML records, pictures, recordings, and different media. HTTP's key characteristics include:
Main Purpose The essential objective of HTTP (Hypertext Transmission Convention) is to make hypertext recovery and transmission more straightforward by permitting internet browsers to ask for and get pages, pictures, recordings, and different assets from web servers. This convention sets the principles for client-server correspondence, specifying how clients make demands and how servers respond, permitting clients to investigate and associate with content on the Internet. III. MQTT (Message Lining Telemetry Transport)It is a lightweight informing convention created for productive gadget correspondence in settings portrayed by restricted data transmission, low power utilization, and high idleness organizations. It is broadly used in the Web of Things (IoT), where organized gadgets should convey trustworthy and effective information. MQTT's key characteristics include:
Main Purpose MQTT (Message Lining Telemetry Transport) is a lightweight, distributed buy-in informing convention produced for effective, low-data transfer capacity and reliable correspondence between gadgets in IoT (Web of Things) and other asset-obliged applications. It gives smooth, versatile, and nonconcurrent information sharing by permitting gadgets to distribute messages to determined themes and different gadgets to buy into those subjects, considering adaptable, continuous correspondence across many organized gadgets and frameworks. IV. Control Area NetworkReal-time and high-integrity data transmission between electronic control units (ECUs) in automotive, industrial, and other embedded systems is the primary purpose of the Controller Area Network (CAN), a dependable and widely used serial communication protocol. Bosch initially developed it for use in in-vehicle communication, but due to its dependability and effectiveness, it has since found use in a variety of industries. The following are key aspects of the CAN protocol:
Main Purpose CAN enables the reliable and timely exchange of information between network nodes, enabling critical functions such as the engine. It controls shifting systems, frame management, and many more uses across business sectors, especially in circumstances that are susceptible to electromagnetic radiation and that demand accurate timing and adaptability. V. SMTP (Basic Mail Move Convention)The SMTP (Basic Mail Move Convention) convention generally conveys and transfers active messages from a shipper's email client or server to the beneficiary's email server. It depicts the principles and guidelines used to ship messages across servers and guarantees they are conveyed to the beneficiary's letter box. Email recovery strategies POP3 (Mail Center Convention Rendition 3) and IMAP (Web Message Access Convention) are utilized by email clients to get to and recover messages from a mail server.
Principal Reason The essential capability of SMTP (Basic Mail Move Convention) is to permit email moving between mail servers. It relays outgoing emails from the sender's email client or server to the recipient's email server. SMTP depicts the correspondence conventions and cycles expected to move email messages, guaranteeing proper conveyance by organizing the trading of messages across different mail servers on the web. ConclusionCommunication protocols are rules and standards in system design that control how devices, applications, or systems communicate data and information. These protocols specify standards for data formats, transmission techniques, error handling, and security measures to provide smooth interoperability, dependability, and security among interconnected components inside a system or between systems. By defining a common language and communication norms, these protocols enable effective data transmission, synchronization, and interaction among varied hardware and software pieces, which is critical in creating efficient, interoperable, and secure systems.
Next TopicExtensible Authentication Protocol (EAP)
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









