Edge RoutersAn edge router serves as a pivotal network infrastructure component, linking a network edge to either the public Internet or a Wide Area Network (WAN). It facilitates remote access from outside the network, encrypts data flows entering and leaving the network, and aids in prioritizing communications to enhance service quality. Data packets are predominantly directed across networks by routers based on the IP addresses in their destination headers. Edge routers typically maintain routing tables containing information about available network pathways and utilize this data to make routing decisions. When a data packet reaches an edge router, it consults its routing table to determine the most efficient route to the destination IP address. Various factors such as network topology, connection capabilities, and current network conditions can influence routing performance. Subsequently, the packet is forwarded to the next hop router or network interface according to the specified route. This routing process is imperative for ensuring timely and accurate data delivery. 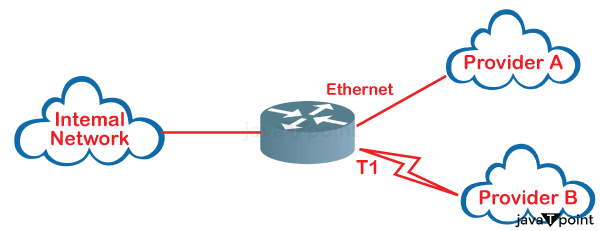
On the WAN aspect an edge router covers a large distance to connect the internal and external networks of an organization. This may include connectivity to different department workplaces, statistics centres or cloud offerings. To provide effective and stable communications over extended distances, threshold routers help deal with visitors between local networks and larger network architectures. An edge router acts as a gateway between a corporation's internal network and the worldwide net on the internet area. It carries out functions that include firewalling, routing, and network address translation (NAT), enabling numerous internal network devices to use a single public IP address for access to the network while guarding against unwanted access to the internal network. Edge routers are prominent with the aid of their flexibility to evolve to various community technologies. They can speak with diverse networks, inclusive of 5G, broadband, satellite tv, and Multiprotocol Label Switching (MPLS). This adaptability allows agencies to stay linked throughout many kinds of community infrastructures. Edge routers normally offer Virtual Private Networks (VPNs), which permit for secure conversation over public networks. VPNs provide an additional diploma of security by encrypting data site visitors between various places or remote users, retaining the confidentiality and integrity of sent statistics. Quality of Service (QoS) is especially significant in the context of edge routers, as networks frequently handle a variety of traffic types with varying requirements. Edge routers accomplish QoS using techniques such as traffic prioritization, bandwidth reservation, and traffic shaping. By assigning different priorities to different types of traffic, the router may guarantee that key applications receive preferred treatment, allowing the network to remain responsive and efficient even during times of high demand or congestion. When a variety of applications share the same network infrastructure, quality of service (QoS) becomes even more important since it helps maintain equilibrium and allocate resources according to the unique requirements of each application. What differentiates an edge router from a normal router?An edge router varies from a normal router in the following methods: Location: An edge router hyperlinks a LAN to the Internet or different outside networks via status at the threshold of the network. In evaluation, a normal router is frequently used to hyperlink a couple of devices inside an inner network. Connectivity: Edge routers control connections to external networks, which also require better bandwidth and scalability. They function with many high-speed interfaces that can connect with diverse network provider vendors or outside networks. Conversely, normal routers often have fewer interfaces for linking gadgets inside a community. Security and services: Edge routers generally include strong security capabilities since they are responsible for implementing security policies and defending a network from external threats. In evaluation, normal routers often have more rudimentary safety competencies that concentrate on nearby network safety rather than external connection. Routing capacity: Edge routers can efficiently manage large quantities of network traffic and path records between networks due to the fact they have more effective processors, greater memory, and greater complete routing tables to deal with complicated routing protocols and make superior routing decisions. Normal routers often have lesser routing capacity because they take care of smaller-scale community traffic inner a single network. Administration and management: Network Administrators and IT experts who are skilled in managing elaborate network settings and external connectivity are usually in the rate of handling side routers. They necessitate a more sophisticated setup and monitoring due to their important characteristic in linking a community to the outside world. Normal routers, on the other hand, are typically simpler to lay out and administer on the grounds that they cope with basic network configurations in a managed environment. Roles and Functions of Edge Routers in Network InfrastructureEdge routers are versatile devices that perform a multitude of functions on the network side. They enable the smooth and secure operation of services, facilitate wireless connectivity, oversee IP address allocation, offer DNS services, and contribute to an organization's overall network security and performance. Accepting incoming customer traffic: Edge routers act as points of access for customer traffic coming into the network. They are in charge of connecting the internal community to external networks such as the Internet and wide-area networks (WANs). Data packets must be routed and sent using edge routers to reach their intended destination within the company. Handling Network Edge Services: Edge routers are becoming increasingly more essential in supporting decentralized services as extra services and applications are administered on the network edge. Applications and services have been regularly managed in cloud computing environments or significant statistics facilities. However, as edge computing gains attraction, certain services are being pushed toward end users or network-side devices. Edge routers provide for the effective delivery and management of those dispersed services. Wireless capabilities: Since they manipulate Wi-Fi communication in the network area, edge routers often include Wi-Fi capabilities. This is mainly critical in contexts wherein Wi-Fi or different wireless technologies are used to hyperlink laptops, cellphones, IoT (Internet of Things) devices, and other wirelessly enabled devices to the network. DHCP (Dynamic Host Configuration Protocol) Services: Edge routers frequently offer DHCP services in the network's area. DHCP is a community protocol that allocates IP addresses and other network configuration records to networked devices. Edge routers offer DHCP, which aids in the dynamic distribution of IP addresses to networked devices, simplifying network administration. Domain Name System (DNS) services: DNS is a key carrier that converts human-readable domain names to IP addresses. Edge routers may additionally offer DNS services on the network, allowing devices at the neighborhood network to solve domains to IP addresses and connect to assets on the internet or different networks. Load Balancing: Some edge routers offer load-balancing functions that disperse incoming network customers over various servers or pathways. This improves resource usage and ensures that no personal server or community hyperlink is overloaded with customers. Security Measures: Edge routers play an important role in implementing network security features. These measures include enforcing access manipulation lists (ACLs), firewalls, intrusion detection and prevention structures, and other safety features to shield the agency's network from unauthorized access and cyber threats. Real-World Applications of Edge RoutersSmart home: To ensure effective building automation and enhanced comfort for occupants, edge routers are critical in handling and protecting data flowing from multiple IoT devices, including electricity meters, security systems, and climate controls. Fleet management: Real-time information from motors, including role tracking, fuel intake, and renovation requirements, ought to be aggregated and despatched via edge routers for fleet management systems to allow optimized routing, more suitable safety, and effective fleet operations. PoS systems: Edge routers provide secure and reliable connections for PoS structures, ensuring efficient transaction processing, information encryption, and clean interaction with large retail management networks, improving each operational performance and purchaser revel. Types of Edge RoutersWhile the functioning of an edge router's hardware is normally regular, there are some substantial variations depending on how they're utilized in the network. In other words, every router can carry out any of these obligations, even though some are greater suitable to them than others. Aggregation edge routers:Route aggregation, developed in the 1990s, aims to conserve IPv4 addresses and optimize routing efficiency on the internet. It involves combining multiple smaller IP address ranges into larger ones to minimize the number of routing table entries. An aggregate edge router is a crucial component in this process, responsible for managing incoming and outgoing traffic to ensure smooth network operation. This router prioritizes and transmits data based on predefined parameters, enhancing network performance. However, one drawback of route aggregation is the reduction in the number of available routes at any given time. Aggregate edge routers are commonly deployed in large-scale networks, particularly in commercial or institutional settings such as businesses, schools, and government offices, where high-speed connectivity is essential due to the large number of connected devices. Branch edge routers:A branch edge router is located at a 'branch' or a more remote position of a WAN network. Branch edge routers do not employ the same aggregation mechanism as other routers since they are not required to. They are mostly utilized in small enterprises or branch office settings so that they can handle small volumes of data. This branch idea is also related to edge computing, which avoids sending locally stored data back and forth to the cloud for processing. Virtual Edge Routers:Virtual edge routing shifts routing from hardware to software. It is a type of network function virtualization (NFV) that involves developing software to perform the tasks of hardware. It works similarly to making your phone a hotspot. Virtual edge routers enable a single device to function as both a router and a network hub. This strategy needs to be improved in terms of speed. Hardware can quickly become overloaded if it is not intended to handle input from several devices. That is why virtual edge routers are more typically utilized in smaller, local networks than in large organizations with a significant number of IoT devices. Benefits of Edge RoutersFortified Security: Edge routers are key components of the firewall, protecting internal networks from external attacks. All data entering and exiting the organization's networks must go via at least one edge router. This centralized data flow enables the deployment of effective security procedures. Edge routers play an important function in screening and filtering incoming and outgoing traffic, hence preventing unauthorized access and potential security breaches. By default, each device connected to the network passes through the edge router's security screening processes, reducing the possibility of network vulnerabilities. Enable Remote Accessibility: Edge routers enable remote access by permitting people to connect to the corporate LAN from different locations. This is mainly essential for distant or cell personnel who need safe and regular access to enterprise assets. Edge routers offer Virtual Private Network (VPN) connections, which provide steady access for remote personnel. Effective Traffic Management: Edge routers effectively control network traffic. They use routing protocols to optimize data glide between internal and external networks. This includes load balancing, which distributes site visitors over several servers or pathways, guaranteeing the most appropriate useful resource utilization and averting congestion. Enhanced network performance: Edge routers help to improve overall network performance by optimizing data flow, prioritizing traffic, and managing network resources. This is especially crucial in circumstances requiring low-latency communication, efficient data transmission, and a consistent user experience. Centralized Screening Processes: Edge routers guarantee that all networked devices, regardless of location, go through centralized screening processes. This centralized method improves security by submitting all network traffic to standard screening processes, removing possible back doors, and strengthening overall defense against security threats. Support for Scalability: Edge routers are intended to meet the rising demands for network scalability. Edge routers can scale to support bigger data volumes, more devices, and more complicated network configurations as organizations develop and their network needs change. Challenges of Edge RoutersUnauthorized Access Risks: Unauthorized access to the edge router creates a considerable danger since it serves as the entry point for external traffic into the corporate network. Enterprises must develop robust authentication techniques and access control rules to prevent unauthorized persons or harmful entities from getting access to critical corporate assets. High Availability (HA) Configuration: Edge routers require high availability to maintain ongoing network functioning. If an edge router dies, its workloads should seamlessly transition to another operational router to avoid service interruptions. To ensure network continuity, high availability is configured with the aid of setting up failover methods and redundancy. This procedure necessitates meticulous instruction and testing to allow an unbroken transition in the case of a router failure. Monitoring and response: Promptly identifying and addressing security problems requires ongoing surveillance of edge router operations. Setting up efficient monitoring tools and reaction mechanisms needs continual work and resources to guarantee that any suspicious activity or anomaly is swiftly handled. Patch control and firmware updates: Updating edge router firmware is vital for solving safety vulnerabilities and defense against the most modern cyber threats. However, coping with firmware upgrades on aspect routers may additionally take a number of work, mainly in huge, scattered networks. Delayed or overlooked improvements may disclose the organization to protection worries.
Next TopicIPTV (Internet Protocol Television)
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









