Standard Access ListACLs are a set of rules for regulating network traffic and minimising network threats. Using a set of rules specified for the network's incoming or outgoing traffic, ACLs are used to filter traffic. Here, we can see that the source parameter is being searched for by the standard Acess list. Therefore, they won't be concerned with the layer 2 frame header; instead, they will examine the packet header, namely the source field, and match solely based on that. Therefore, they won't delve further into the transit layer. 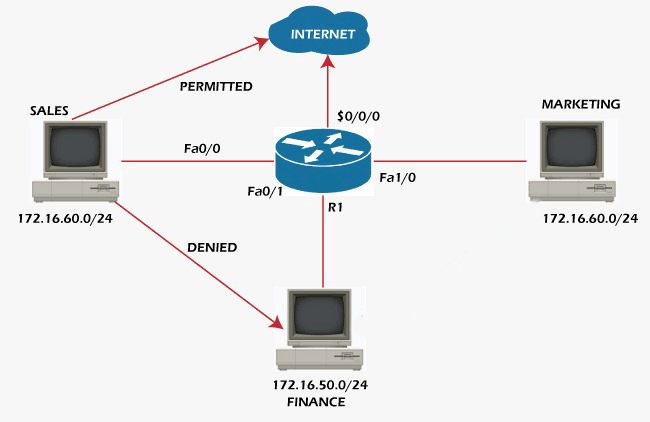
Standard Access list -These are Access-lists that are created solely utilising the source IP address. These ACLs either allow or disallow the whole set of protocols. TCP, UDP, HTTPS, and other types of IP transmission are not differentiated. The router will recognise it as a regular ACL and the provided address as the source IP address if you use the numbers 1-99 or 1300-1999. Features of Standard Access List -
Note: Standard Access-lists are less commonly used than extended Access-lists since they accept or deny communication for the complete IP protocol suite because they cannot tell one IP protocol from another.Setting up -The sales, finance, and marketing departments are the three in this modest topology. The networks for the marketing department are 172.16.60.0/24, the finance department is 172.16.50.0/24, and the sales department is 172.16.40.0/24. In order to prevent others from accessing that network, you now wish to block connections from the sales department to the finance department. To prevent any IP connection from the sales department to the finance department, first configure a numbered standard access list. Similar to extended access-list, you cannot specify the specific IP traffic that should be allowed or blocked here. Please also note the use of the wildcard mask ( 0. 0. 0. 255 which means Subnet mask 255. 255. 255. 0). The number 10 is taken from the access-list standard range. As you are already aware, every access list has an implicit refuse at the end, which indicates that if the traffic does not comply with any of the access list's rules, the traffic will be discarded. Only traffic that complies with the aforementioned rules that you have specified will reach the finance department by specifying any means from a source with any IP address. You must now apply the access list to the router's interface: Remembering that the standard access-list is typically applied to the destination, outbound to interface fa0/1 has been applied since it will meet our needs if it is applied close to the destination. Standard Access-list illustration -You will now create a named standard access list while still keeping in mind the same structure. You have created an access-list called blockacl by running this command. The identical setup that you did in the numbered access-list is then applied. Example of a standard access-list for TelnetTelnet connection can be allowed or denied using standard access-list by applying access-list on line vty lines. As you are aware, you cannot specify specific IP traffic to be prohibited in standard access-list. Here, in the provided figure, you want to prevent telnet access from any network to the Finance department. Setting up for the same:
Next TopicTime Access List
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









