What is Deep WebIntroductionParts of the World Wide Web that are not indexed by conventional online search engines are referred to as the "deep web," "invisible web," or "hidden web." In contrast, the "surface web" is available to anybody with an Internet connection. The phrase was coined in 2001 as a search-indexing word and is ascribed to computer scientist Michael K. Bergman. 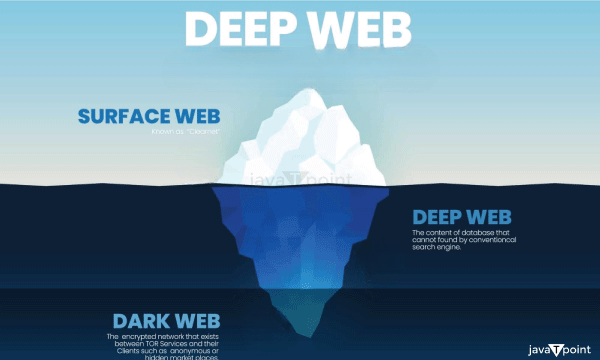
Direct URLs or IP addresses may be used to visit deep web sites, but in order to see the real content, you might need to provide a password or other security details. Web mail, online banking, cloud storage, social media pages and profiles with limited access, and online forums where content viewing requires registration are some of the applications for deep web sites. It also covers various online periodicals and newspaper, as well as paywalled services like video on demand. A large portion of the deep web's material is lawful and not illegal in nature. Emails, chats, private posts on social media, bank statements, electronic health records (EHR), and other material that can be accessed online in one way or another are examples of deep web content. Search engine bots are also prevented from accessing any paywalled website, including news article text sites and subscription-only educational material sites. Furthermore, the bots do not crawl sites that charge for services like Netflix. Consequently, the deep web offers some benefits. To begin with, a large portion of the material on the deep web is irrelevant, which would further complicate searches. Furthermore, privacy is a concern; nobody wants Google bots to go through their Fidelity Investments account or Netflix library. Dark Web vs Deep WebAlthough the phrases "deep web" and "dark web" are sometimes used synonymously, they are not the same. Similar to the wider deep web, the "dark web" is a subset of the internet that is not indexed by and hence not available via search engines like Google. 
The deep web is replete with authentic and lawful material, such as databases, academic papers, and research, while the black web is much more dubious. Numerous illicit activities take place on the dark web, such as prostitution, drug trafficking, weapons trafficking, malware, prostitution, sex trafficking, and black markets for credit card and personal information theft. There are other cyberattack services accessible, such as botnet access for distributed denial-of-service assaults. Illegal markets and forums where illicit behavior is marketed and discussed abound on the dark web. Dream Market, Nightmare Market, and Empire Market are a few examples. One drug-dealing website, Silk Road, gained so much notoriety that publications from mainstream media often used it as an example of the dark web. After being apprehended, the owner was given a life sentence without the possibility of release. The only category of unlawful merchandise not featured on the main dark web marketplaces is explicit child exploitation content. Pedophiles operate their own forums and dark web sites apart from the websites that sell credit cards and drugs. How to obtain access to the deep web?Information on the deep web is often still accessible even when standard search engines don't index it. The majority of internet users often access material on the deep web, which is generally safe to do so. A few instances of accessing data on a deep web site include logging into the Wall Street Journal, LinkedIn, or Gmail. Because criminals may find value in the personal information found in user accounts on the deep web, access to a large portion of it is limited. Users will never have access to the deep web or the black web. A dark web marketplace may be the source of spam and phishing attempts, but malware cannot be released until a user downloads anything compromised from that marketplace. It would not be the dark web site itself that would launch an assault. The dark web is purposefully concealed and accessible only with the use of certain technologies, such as the Invisible Internet Project (I2P) network and the Tor browser. Both are useful in their own right. While browsing websites, Tor will shield our IP address, and I2P is a proxy network that may support reporters in hazardous areas. Without the Tor browser, users cannot access a dark web marketplace. Furthermore, while being built on the Mozilla Firefox browser, Tor has poor maintenance and problems with how pages appear. Examining the dark web makes sense for one purpose. The dark web is an excellent area to identify where vulnerabilities that are not yet known are being discussed, because of all the conversations about hacking and exploit trafficking that take place there. Users may have the benefit of being aware of exploited locations before they become major security risks by keeping an eye on the dark web.
Next TopicUSB-C (USB Type C)
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









