Banker's Algorithm in C++
The Banker's method is a resource allocation and deadlock avoidance method that is used in operating systems to guarantee that operations are carried out effectively and securely in a multi-resource environment. Edsger W. Dijkstra created it in 1965, and it is essential for managing resources including CPU time, memory, and I/O devices.
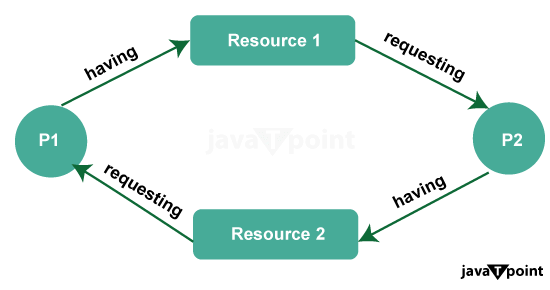
The fundamental problem the Banker's Algorithm addresses is preventing deadlock. Deadlock occurs when processes in a multi-resource system get stuck because they are waiting for resources held by other processes, creating a circular waiting scenario. To avoid this situation, the Banker's Algorithm uses a set of data structures and checks to ensure that resource allocation requests can be satisfied without leading to an unsafe state.
Key components of the Banker's Algorithm
- Available Resources: This is a vector that represents the number of available instances of each resource type in the system.
- Maximum Demand Matrix: A 2D array that indicates the maximum number of resources that each process may need during its execution.
- Allocation Matrix: Another 2D array that shows the number of resources currently allocated to each process.
- Need Matrix: This 2D array represents the remaining resources needed by each process to complete its execution.
Components of Banker's Algorithm
- Available Resources (Vector): This component represents the number of available instances of each resource type in the system. The vector holds the current availability of each resource.
- Maximum Demand Matrix (2D Array): The maximum demand matrix specifies the maximum number of each resource type that a process may request throughout its execution. It describes the upper limit on resource requirements for each process.
- Allocation Matrix (2D Array): The allocation matrix shows the number of resources that are currently allocated to each process. It reflects the resources that have been granted to processes at any given time.
- Need Matrix (2D Array): The need matrix represents the remaining resources needed by each process to complete its execution. It is calculated as the difference between the maximum demand and the allocation for each process.
- Safety Algorithm: The safety algorithm is a core part of the Banker's Algorithm. It is responsible for determining whether granting a resource request will lead to a safe or unsafe state. The algorithm checks if a sequence of resource allocations can be found where all processes can complete their execution without causing a deadlock.
- Resource Request Algorithm: When a process requests additional resources, the resource request algorithm checks whether the requested resources can be safely allocated without violating safety conditions. It involves comparing the request with the available resources and the process's remaining need.
- Finish Array: The finish array is a Boolean array that keeps track of the completion status of each process. It helps the safety algorithm identify which processes can complete their execution given the current resource allocation.
- Safe Sequence: If the safety algorithm determines that there exists a safe sequence of processes, it can provide this sequence as an output. A safe sequence is a sequence of processes in which each process can be allocated the requested resources without causing a deadlock.
- Resource Release: The Banker's Algorithm also considers the release of resources by processes once they have completed their execution. Resources that are released become available for allocation to other processes.
Application of Banker's Algorithm
- Operating Systems: The Banker's Algorithm is primarily used in contemporary operating systems. It controls how many processes can run at once while sharing system resources including CPU time, memory, and I/O devices. Operating systems can prevent instances in which processes stall out while waiting for resources by employing the algorithm.
- Database Management Systems: Database management systems (DBMS) often have multiple concurrent transactions or queries competing for resources like locks, buffer space, or access to specific tables. The Banker's Algorithm can be used to allocate these resources efficiently, ensuring that transactions can proceed without causing deadlock.
- Resource Management in Distributed Systems: In distributed systems, resources may be distributed across multiple nodes or servers. The Banker's Algorithm can be adapted to manage resource allocation in distributed environments, preventing deadlock and ensuring efficient resource utilization.
- Network Resource Management: In computer networks, especially in scenarios like Quality of Service (QoS) management, where different applications or users request network resources (e.g., bandwidth), the Banker's Algorithm can be employed to allocate these resources fairly and avoid network congestion or deadlock.
- Supply Chain Management: Equipment, raw materials, and transportation can be distributed among multiple production processes or orders in supply chain management and manufacturing. The Banker's Algorithm can aid in resource allocation optimization while preventing resource shortages or production bottlenecks that could cause delays.
- Cloud computing service providers distribute virtual machines, storage, and network resources across numerous clients. By effectively managing these resources, The Banker's Algorithm makes sure that clients can increase their operations without worrying about resource conflict or impasse.
- Multiple users or applications may request access to databases, printers, files, or other shared resources in multi-user systems. Using the Banker's Algorithm, resource disputes can be avoided and fair access can be ensured.
- Project Scheduling: The Banker's Algorithm can assist with task scheduling and resource allocation in project management, particularly in large-scale projects with numerous dependencies and resource limitations. This will help to ensure that project deadlines are fulfilled without resource bottlenecks or deadlocks.
- Process Synchronization: When programming concurrently, different threads or processes may fight for access to the same resources, including mutex locks. The Banker's Algorithm implementations can be used to effectively manage these locks, avoiding deadlocks and maintaining thread safety.
- Robotics and autonomous systems: Different components like sensors, actuators, and computing units may compete for resources in robotics and autonomous systems. These resources can be distributed using the Banker's Algorithm, guaranteeing that the robot or system functions correctly and without resource-related problems.
Working of Banker's Algorithm
- Initialization:
- The system maintains information about the available resources of each type.
- It also keeps track of the maximum demand of each process, i.e., the maximum number of resources each process may need.
- It maintains information about the resources currently allocated to each process.
- Request Phase:
- When a process requests resources, it specifies the maximum additional resources it needs.
- The system checks if the requested resources can be allocated without violating the safety conditions.
- The safety conditions ensure that the system remains in a safe state even after granting the resources.
- The algorithm examines if the requested resources are less than or equal to both the available resources and the maximum resources the process can claim.
- Resource Allocation:
- If the requested resources can be safely allocated, the system grants them to the requesting process.
- It also updates the data structures to reflect the new allocation.
- Safety Check:
- After each resource allocation or request, the system checks if the system remains in a safe state.
- The safety check involves simulating the allocation and deallocation of resources to check if there exists a sequence in which all processes can complete without getting stuck in a deadlock.
- Deadlock Avoidance:
- If the system determines that granting the requested resources would lead to an unsafe state, it denies the request.
- The requesting process must wait until the resources become available.
- This ensures that resources are allocated in a way that avoids deadlock.
- Resource Release:
- When a process finishes, it releases all its allocated resources.
- The released resources are added back to the available resource pool.
- Repeat:
- Steps 2 to 6 are repeated as processes make requests and release resources.
- Termination:
- The system continues to operate safely unless all processes have completed.
- When all processes have finished, the system is in a safe state.
Assumptions in Banker's Algorithm
- The Banker's Algorithm presupposes that there are a set number of resource categories in the system. A few examples of these resource kinds include CPU time, RAM, and I/O hardware. The algorithm requires prior knowledge of the system's maximum availability of each resource type.
- Fixed Number of Processes: It presupposes that the system has a fixed number of processes. A program or task that needs access to one or more resource types is represented by each process. The algorithm must be aware of each process's maximal resource requirements.
- Resources Can Be Preempted: The algorithm makes the assumption that resources allotted to one process can be redirected to other processes if that process is preempted. This implies that a resource can be removed and assigned to another process if a process no longer requires it.
- Processes Must Request Resources in Advance: Processes must indicate their maximum resource needs in advance. This information is crucial for the algorithm to determine if a resource request can be granted without causing a deadlock. If a process doesn't declare its maximum resource requirements, the algorithm cannot work effectively.
- Hold and Wait: It assumes that processes can hold resources while waiting for additional resources. However, to prevent deadlock, a process cannot request additional resources while holding some resources. This "hold and wait" assumption aims to avoid circular waiting, a condition that can lead to deadlock.
- No Preemption: The algorithm assumes that resources cannot be forcibly preempted from a process. In other words, if a process holds certain resources, it can either release them voluntarily or request additional resources, but it cannot have its resources forcibly taken away by the system.
- Processes Release All Resources at Once: When a process completes its execution, it releases all the resources it holds. The algorithm does not handle cases where a process releases resources incrementally.
- Resource Allocation is Immediate: The algorithm assumes that resource allocation is immediate and that resources are allocated and deallocated atomically. In reality, resource allocation may involve some delay or take time to complete.
- Resource Requests Are Known in Advance: Processes must know their resource requirements in advance and must request all the resources they need at the beginning of their execution. This assumption may not hold in situations where a process's resource needs change dynamically during execution.
- A Safe State Exists: The most critical assumption is that a "safe state" exists in the system. A safe state is a state in which the system can allocate resources to processes in such a way that no deadlock can occur.
Source Code
Complexity Analysis of Banker's Algorithm
- Initialization (O(R x P)): The algorithm starts by initializing data structures such the availability, maximum, allocation, and requirement matrices. This is known as initialization (O(R x P)). The temporal complexity of this initialization step, which iterates across all resources and processes, is O(R x P).
- Safety Algorithm (O(R x P^2)): The safety algorithm is used to determine if a system is in a safe state. It iterates through each process (P) and resource (R) combination to check for safe sequences. In the worst case, the time complexity is O(R x P^2). This step is usually performed whenever a resource request is made.
- Resource Request (O(R + P)): When a process requests additional resources, the algorithm checks if the request can be granted safely. This check involves iterating over the resources (R) and processes (P) once, making it O(R + P) in time complexity.
- Resource Release (O(R + P)): When a process releases resources, the algorithm updates the state accordingly. This operation also has a time complexity of O(R + P) since it involves iterating over resources and processes.
Computational Efficiency and Limitations:
- Computational Efficiency: The Banker's Algorithm is known for its efficiency in preventing deadlocks. It does not unnecessarily block processes, and it can effectively allocate resources when sufficient resources are available to meet process requirements.
Limitations of Banker's Algorithm terms of Complexity
- Static Allocation: One significant limitation is that the Banker's Algorithm assumes a fixed maximum requirement for each process at the start, making it less suitable for systems were resource needs change dynamically.
- Resource Utilization: The algorithm may not make the best use of available resources because it can be conservative in its approach. It may leave resources idle to ensure safety, leading to underutilization.
- Complexity: The worst-case time complexity of the safety algorithm (O(R x P^2)) can be a limitation for large systems with many processes and resources. It may lead to a significant computational overhead.
- Knowledge Assumption: The algorithm makes the assumption that the maximum resource needs for each process are known in advance. In actuality, this data might not always be accessible or might alter on demand.
- Resource Priority: The Banker's Algorithm doesn't consider the priority of processes. It treats all processes equally, which may not be suitable for systems where certain processes need to be given priority.
- No Preemption: The algorithm does not allow for resource preemption, meaning if a process is denied resources, it must release all its resources and start over, which can be inefficient.
Resource Request:
- The Process Requests Resources: A process must identify the types and quantities of resources it requires when making a resource request. This request comes from the process and contains a vector-based request for resource allocation.
- Safety Check: The Banker's Algorithm first performs a safety check to determine if granting the request will lead to a safe state. It checks if the requested resources can be allocated without violating the safety conditions. The safety algorithm is used to evaluate this.
- Grant or Block: If the safety check indicates that the system will remain in a safe state after granting the request, the algorithm allocates the requested resources to the process, and the process proceeds with its execution. Otherwise, the process is blocked and put in a queue of waiting processes until its request can be safely granted. This ensures that resource allocation will not lead to a deadlock.
Resource Release:
- Process Releases Resources: When a process has finished using allocated resources, it releases them by specifying the types and quantities of resources it is releasing. This is done explicitly by the process.
- Resource Release Handling: The Banker's Algorithm adjusts the available resources by increasing the available resource count for each resource type based on what the process is releasing. This ensures that the released resources are now available for allocation to other processes.
Example:
Let's illustrate how the Banker's Algorithm handles resource requests and releases with a simple example:
Suppose there are three resource types (A, B, C) and three processes (P1, P2, P3) in the system.
- Initialization: Initially, the algorithm initializes the following data structures:
- Maximum Matrix (Max): Specifies the maximum demand of each process.
- Allocation Matrix (Alloc): Specifies the resources currently allocated to each process.
- Need Matrix (Need): Indicates the resources needed by each process to complete its task.
- Available Vector (Avail): Represents the available resources of each type.
- Resource Request:
- If process P1 requests resources (2, 1, 0), the algorithm checks if this request can be safely granted without causing a deadlock.
- If the safety check passes, the algorithm allocates the requested resources to P1, updates the allocation and need matrices, and decreases the available vector.
- If the safety check fails, P1 is blocked until its request can be granted safely.
- Resource Release:
- When P1 has finished using resources, it releases them by specifying what it's releasing (e.g., (1, 1, 0)).
- The algorithm increases the available vector by the released resources and updates the allocation matrix accordingly.
Future Trends in Banker's Algorithm
- Dynamic Resource Allocation: Future variations of the Banker's Algorithm may focus on accommodating dynamic resource allocation. Today's systems often require flexibility in adjusting resource allocation in real-time based on changing workloads. Algorithms that can adapt to these dynamic demands while ensuring safety will be crucial.
- Distributed Systems: With the proliferation of distributed and cloud computing, resource allocation across multiple nodes and data centers becomes complex. Future developments may involve extensions or adaptations of the Banker's Algorithm to address distributed systems' unique challenges and ensure safe resource sharing in large-scale, networked environments.
- Machine Learning Integration: Leveraging machine learning techniques, future algorithms may have the capability to predict resource demands more accurately. Predictive modeling can help preemptively allocate resources to processes or nodes where they are likely to be needed, improving efficiency and responsiveness.
- Quantum Computing: As quantum computing becomes more prevalent, traditional algorithms may need to be rethought. Resource allocation in quantum systems may require entirely new algorithms that consider the unique properties of quantum computing and its associated resources.
- Real-time Resource Monitoring: Future developments may include the integration of real-time resource monitoring and anomaly detection. Systems may be capable of identifying potential resource contention issues and proactively reallocating resources to prevent deadlock situations.
- Integration with Containerization: Containerization technologies like Docker and Kubernetes are widely used for application deployment. Future Banker's Algorithm variants might integrate seamlessly with these container orchestration platforms, optimizing resource allocation within containerized environments.
- Security Considerations: As cybersecurity threats continue to evolve, resource allocation algorithms may need to incorporate security considerations. Ensuring that resource allocation decisions do not expose vulnerabilities or enable malicious activity will be a critical focus.
- Energy Efficiency: Given the increasing emphasis on energy-efficient computing, future developments in resource allocation may aim to optimize not only for performance but also for energy consumption. Resource allocation algorithms could factor in energy-saving strategies when making decisions.
- Quantifiable Metrics: Future algorithms may provide quantifiable metrics for resource allocation decisions, allowing administrators to understand the trade-offs between safety, performance, and other factors, facilitating more informed decision-making.
- Interoperability and Standardization: As heterogeneous computing environments become common, standardized resource allocation interfaces and protocols may emerge to ensure compatibility and ease of integration across diverse systems.
|

 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now










