Stack smashing detected in C++Stack smashing detected in C++ is an error message generated by the C or Cpp compilers like GCC and many runtime environments when buffer overflow occurs or when someone tries to store more amount of data in a fixed amount of memory. At the same time, it behaves as a security mechanism to alert the users and developers saying that there's been an attempt to corrupt the program's stack, which is a very common sign of malicious activity. After showing this stack smashing detected error, the program that is currently running will be terminated to prevent further execution and save from malicious risks. There are many cases where this error is likely to occur. Some of them are listed below:
Now, we will discuss each case with an example code: 1. Buffer Overflow:Every buffer is allocated with some fixed stack space. When a program writes more data into the buffer than the allocated fixed size, it causes the buffer to overflow. It means writing beyond the allocated memory corrupts the stack, which leads to the stack smashing. Example: Output: 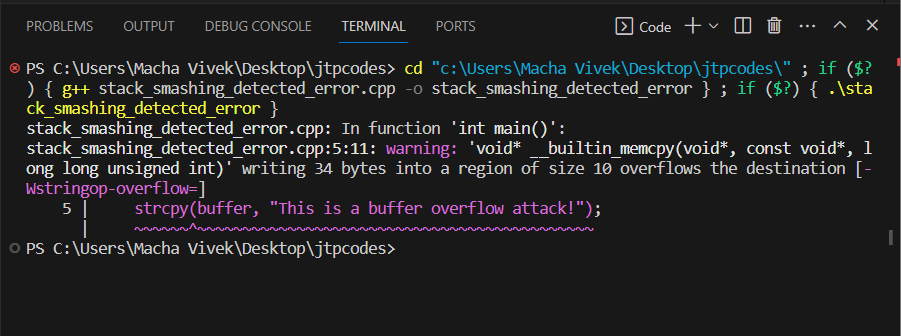
Program which avoids the stack smashing detected error: Output: 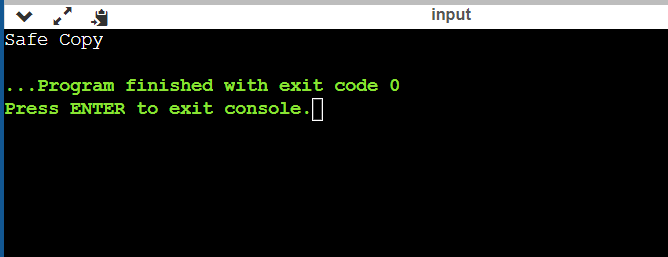
3. Incorrect use of the string functions:Some string inbuilt functions like strcpy and strcat, when used without the proper bounds checking, will cause the buffer overflow. As these functions do not check the size of the destination buffer, making buffer overflow and override the adjacent memory blocks. 4. Function pointer manipulation:This error is shown when a program attempts to call a function through a manipulated or corrupted function pointer. It usually happens when an attacker or a bug in the program will alter the function pointer's value. Pointing it to an unintended location or a non-function address. Example: A program that causes the error: Output: 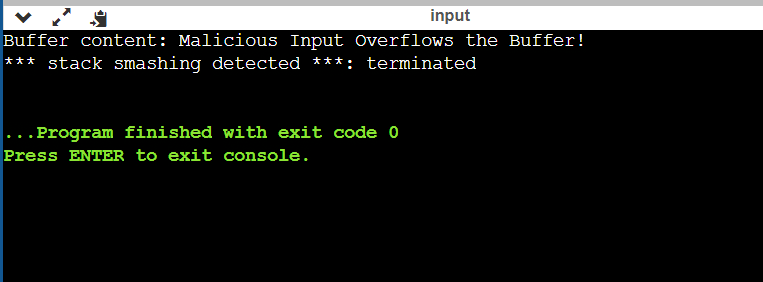
Program which avoids the stack smashing detected error: Output: 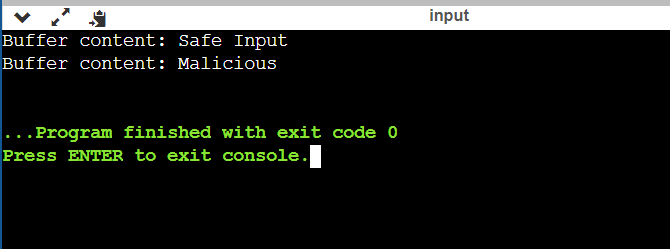
4. Recursion without base casebase case or base condition are used in the recursion for stopping the further recursion and returning the required result to the called function. If the base condition is not met then the recursion will not stop. It throws the stack overflow error. This error is due to the filling of function calls in the stack. To avoid the error we can use proper base condition for any type of the recursion Example: A program that causes the error: Output: 
Program which avoids the stack smashing detected error: Output: 
5. Malicious input handling:If the user is not correctly validated, it allows the attackers to input excessively long strings. So, the attackers will send the long strings to overflow buffers, causing stack smashing. 6. Array Index Out Of Bounds:If an array goes out of its fixed size, we get an array index out-of-bounds error. When someone tries to access the element using an index that is not present in the array, we get the array index out of bounds. When we write the elements to the array even after the length of the array is exceeded, we get the array index out-of-bounds error, which causes the stack smashing error. 7. Incorrect use of pointers:Improper dereferencing or manipulation of pointers can lead to writing data into unintended memory locations. Writing data to unintended memory addresses can corrupt the stack or other program data structures. |
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









