Implementation of Access matrix in the operating systemIn this article, you will learn about implementing the access matrix in the operating system. But before discussing the implementation of the access matrix, you must know about the access matrix in the operating system. What is Access Matrix in Operating System?The Access Matrix is a security model for a computer system's protection state. It is described as a matrix. An access matrix is used to specify the permissions of each process running in the domain for each object. The rows of the matrix represent domains, whereas the columns represent objects. Every matrix cell reflects a set of access rights granted to domain processes, i.e., each entry (i, j) describes the set of operations that a domain Di process may invoke on object Oj. There are various methods of implementing the access matrix in the operating system. These methods are as follows:
Global TableIt is the most basic access matrix implementation. A set of ordered triples <domain, object, rights-set> is maintained in a file. When an operation M has been performed on an object Oj within domain Di, the table is searched for a triple <Di, Oj, Rk>. The operation can proceed if this triple is located; otherwise, an exception (or error) condition has arrived. This implementation has various drawbacks. The table is generally large and cannot be stored in the main memory, so additional input and output are required. Access Lists for ObjectsEvery access matrix column may be used as a single object's access list. It is possible to delete the blank entries. For each object, the resulting list contains ordered pairs <domain, rights-set> that define all domains for that object and a nonempty set of access rights. We may start by checking the default set and then find the access list. If the item is found, we enable the action; if it isn't, we verify the default set. If M is in the default set, we grant access. Access is denied if this is not the case, and an extraordinary scenario arises. Capability Lists for DomainsA domain's capability list is a collection of objects and the actions that can be done on them. A capacity is a name or address that is used to define an object. If you want to perform operation M on object Oj, the process runs operation M, specifying the capability for object Oj. The simple possession of the capability implies that access is allowed. In most cases, capabilities are separated from other data in one of two ways. Every object has a tag to indicate its type as capability data. Alternatively, a program's address space can be divided into two portions. The programs may access one portion, including the program's normal instructions and data. The other portion is a capability list that is only accessed by the operating system. Lock-Key MechanismIt is a compromise between the access lists and the capability lists. Each object has a list of locks, which are special bit patterns. On the other hand, each domain has a set of keys that are special bit patterns. A domain-based process could only access an object if a domain has a key that satisfies one of the locks on the object. The process is not allowed to modify its keys. Now, let's take an example to understand the implementation of an access matrix in the operating system. Example: 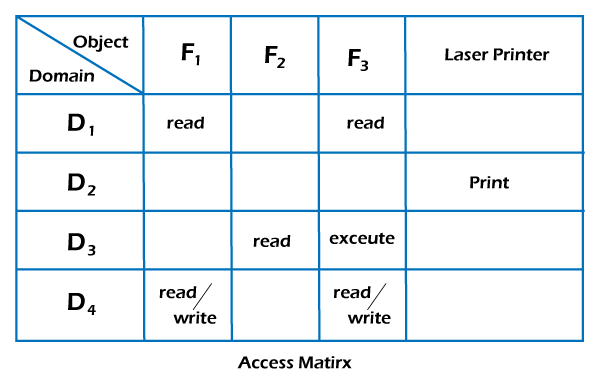
In this example, there are 4 domains and objects in the above matrix, and also consider 3 files (including F1, F2, and F3) and one printer. Files F1 and F3 can be read by a process running in D1. A process running in domain D4 has the same rights as D1, but it may also write on files. Only one process running in domain D2 has access to the printer. The access matrix mechanism is made up of various policies and semantic features. Specifically, we should ensure that a process running in domain Di may only access the objects listed in row i. The protection policies in the access matrix determine which rights must be included in the (i j)th entry. We should also choose the domain in which each process runs. The OS usually decides this policy. The Users determine the data of the access-matrix entries. The relationship between the domain and the processes might be static or dynamic. The access matrix provides a way for defining the control for this domain-process association. We perform a switch action on an object when we switch a process from one domain to another. We may regulate domain switching by containing domains between the access matrix objects. If they have access to switch rights, processes must be enabled to switch from one domain (Di) to another domain (Dj). 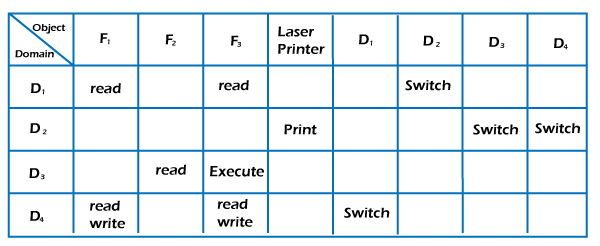
According to the matrix, a process running in domain D2 can transition to domains D3 and D4. A process in domain D4 may change to domain D1, and a process in domain D1 may change to domain D2.
Next TopicKaiOS Operating System
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









