Two-Factor Authentication (2FA)What is Two Factor Authentication?When attempting to access a system or program, the user must provide two different forms of identification: one of which is usually their password, while the second form can be OTP verification or any other approach based on the respective program/system. This is known as two-factor authentication (2FA). 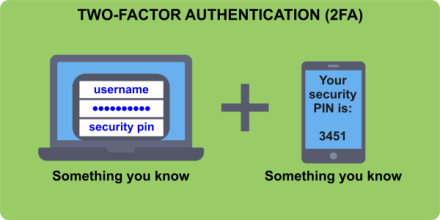
Nowadays, a typical business operates using various resources, including third-party applications and software-as-a-service (SaaS) solutions. The 2FA secures everything from commonplace services like email to delicate activities like obtaining consumer data. In general, the employees are given user credentials for each of the necessary services, and it is their responsibility to follow proper password hygiene so that these credentials do not lead to security flaws. Passwords should be changed frequently, be as complicated as feasible (a combination of alphabets, digits, and symbols), and not be used again across different apps. All of this does, however, leave a lot of possibility for human error. Hackers know that forgotten and easy-to-crack passwords (like 12345) are the weakest points in an organization's security. They try phishing and other social engineering tactics to access user credentials if the brute force does not work. In about 80% of data breaches, brute force attacks or credentials that have been lost or stolen are used, according to Verizon's 2020 Data Breach study. The degree of protection afforded to an organization's various resources, applications, and services determines its security posture. Despite having different infrastructure security levels, the level of security ultimately depends on how strong the passwords are. This indicates that a company cannot solely rely on conventional passwords. Two-factor authentication can be used in this situation. To put it simply, 2FA requires two steps for authentication. In addition to the secure password, the second step can be any type of authentication that typically depends on something the user has, such as one-time passwords (OTPs), key fobs that produce tokens, fingerprint scanners, or even merely push notifications delivered to mobile devices. Although the first step is typically a regular password, this extra step ensures that even if hackers discover the password, they would still need the other secure data to break through the second authentication. Therefore, it becomes tough for hackers or other unauthorized access to get control over users' personal information or other sensitive information. Multi-factor authentication (MFA) includes two-factor authentication as a subset. MFA typically calls for more verification steps than 2FA, which terminates at just two. Entry points to resources that are vital to operations typically use multi-factor authentication. A banking app might, for instance, ask employees to input a password as a first step, a time-limited one-time password as the second step of verification, and a fingerprint scanner as a third step for added protection. Additionally, there is usually also a need to connect to specific network servers. However, regarding customer-facing services, 2FA is the most widely used type of MFA. Different Ways to Use 2FA1. 2FA for EmployeesWhen used with email, VPN, remote access, and other third-party services like file-sharing apps, cloud repositories, etc., this is referred to as 2FA on an internal, corporate level. At the corporate level, it is mostly utilized by the employees. Businesses must make sure that the execution of respective services is consistent at all organizational levels. 2. 2FA with Customers in MindCustomers of any company's goods, programmes, or services must go through this layered authentication procedure for additional protection. Customer-facing 2FA is frequently found in banking systems. Typically, this is done to uphold SLAs (service-level agreements) and keep data secure with legal requirements. Security is not the only reason to use two-factor authentication. Depending on the business's sector, it might also be a legal requirement to prevent unauthorized transactions. Healthcare (which must adhere to strict HIPAA requirements), e-commerce, social media, and education are some sectors that frequently use 2FA (considering that the COVID-19 pandemic has pushed most education online across the world). 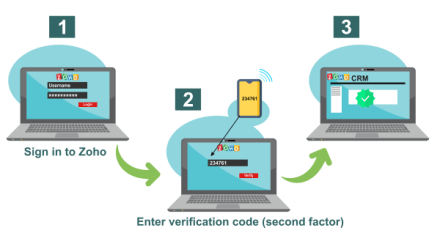
Example 2FAInstagram is an excellent example of two-factor authentication in social media, as it usually only requires a password to sign in. The option to add a second authentication step using a security code provided through text message or an authenticator app is also available to users. Especially for influencers whose brand heavily depends on their Instagram feed, this might be a sensible choice to take into account. Significant Advantages of Two-Factor AuthenticationA two-factor authentication method has numerous significant advantages. These consist of the following: 1. Reduces human mistakes to reduce the attack surfaceA company is only strong when it has the strongest passwords or security systems for data. However, it's challenging to keep track of dozens of passwords while adhering to strict hygiene standards. Likewise, it is difficult to keep all the passwords secure for longer use. Unsurprisingly, password-only access points to the system are the main target of cyberattacks. A significant step in enhancing security is 2FA, and it is doubtful that hackers will be able to bypass each authentication step and get access. 2. The first stage of a zero-trust security paradigmA zero-trust security paradigm is a security idea that operates under the presumption that every device, programme, user, and network-internal or external-is unreliable and requires additional security measures. Since cybercrime is expected to cost the globe $10.5 trillion annually by 2025, utilizing 2FA is not a surprise move. Guarding all access points with increased protection is the first step toward a perimeter-less security strategy. 3. Permits businesses to adopt BYOD guidelinesThe number of remote users has unexpectedly increased as a result of the COVID-19 outbreak. Businesses that in the past had not even thought about BYOD (Bring Your Own Device) policies now had to deal with external networks and devices accessing their systems. Companies are compelled to implement the proper authentication procedures in all BYOD scenarios through a two-factor authentication system. 4. Assists in adhering to industry regulationsRules like the Federal Financial Institutions Examination Council (FFIEC) directive mandate multi-factor-based authentication for internet banking transactions. Implementing a two-factor authentication method is the most straightforward way to abide by such rules when regulating the industry. 5. Makes use of hardware improvements in daily lifeOver time, computing has made tremendous strides. The average person today has access to extremely powerful hardware and computer resources. In reality, improvements come to the public every few months. Utilizing this power to improve authentication systems and protect personal data is only logical. There is no denying the advantages of two-factor authentication for companies of all sizes. The details of the 2FA procedure and what organizations must do to adopt it are essential for each company and business in various fields. Explaining the Two-Factor Authentication ProcessThe concept of "factors" underpins all multi-factor authentication procedures, including two-factor authentication. When we state that a user must go through two authentication processes, we mean that the user must employ two factors (or two systems). The best 2FA systems combine several distinct elements, such as:
On a scale of 2FA
Best Practices for Using and Managing Two-Factor Authentication
Next TopicWhat is the 3-6-3 Rule
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









