Linux Firewall
Introduction to Linux Firewall
A firewall can be defined as a system of network security that controls and filters the traffic on the rule's predefined set. It is an intermediary system between the Internet and the device.
The kernel of Linux contains a subsystem, i.e., Netfilter. It is used for deciding or manipulating the network traffic fate headed through or into our server. All latest solutions of Linux firewall apply this system for a process which is known as "packet filtering".
The packet filtering system process of the kernel will be of tiny use to many administrators without any userspace interface for managing it. It is the goal of iptables: if a packet reaches our server, it would be handed off for rejection, acceptance, or manipulation to the Netfilter subsystem based on various rules supplied to it through userspace by iptables.
Hence, iptables is all we require to handle our firewall if we are known to it. However, several frontends are present for simplifying the task.
Note: If we already know about firewall working and only wish to know about the commands, then we can skip the firewall working and go to the tutorial's end.
Some key points are mentioned below that we need to know about Linux firewall:
- A firewall is a group of rules.
- When a packet of data moves out or into a protected space, then its contents (information about its target, protocol, and the origin it plans for using) are checked against the rules of the firewall to see if it must be permitted through.
- Besides, iptables is another tool of CLI to manage the rules of firewall on any Linux machine.
- Also, Firewalld is a tool to manage the rules of a firewall on any Linux machine.
- Linux firewall can also be described as a device that checks Network traffic (outbound/inbound connections) and establishes a decision to traffic out or pass the traffic.
- In this era, Network Security is derived from different kinds of Linux firewalls.
- In the traditional packet, firewall filtering deals with filtering and routing packets, where else NGFWs would work with some other functions (with OSI layers).
firewalld
firewalld can be defined as a way for protecting machines from outside from unwanted traffic. It enables all the users to manage network traffic (incoming) on host machines by specifying the firewall rules set. These rules can be used for sorting the traffic and either allow it or block through.
- firewalld applies the concepts of services and zones that simplify the management of traffic.
- Zones are a set of predefined rules.
- Network sources and interfaces are assigned to the zone.
- The traffic permitted depends on the network our computer is linked to and the level of security this network is elected.
- The firewall services can be defined as some predefined rules that enclose each essential setting to permit the traffic for a particular service and they use within the zone.
- Services use multiple addresses or ports for network communication.
- The filter communication of firewalls is based on the ports.
- To permit network traffic for any service, its ports should be open.
- firewalld can block every traffic on the ports that aren't set as open explicitly.
- By default, a few zones like trusted permit each traffic.
- firewalld could be used for separating networks into distinct zones based on the trust level that a user has determined for placing on the traffic and interfaces in that network.
Working of Linux Firewall
Most of the distributions of Linux ship with many tools of default firewall that could be used for configuring them. We will use "IPTables" (default tool) given in Linux to create a firewall. Iptables is used for setting up, inspecting, and maintaining the packet filter rules of IPv6 and IPv4 tables in a Linux kernel.
Important: Every command in this article requires the privileges of sudo.
Iptables Working
Network traffic is composed of packets. Data is divided into various small pieces (known as packets), transferred over a network, put back altogether. Specifically, iptables recognizes the packets which are received and applies a group of rules for deciding what we can do to them.
Ipatables is a command-line interface application that permits an administrator for configuring particular rules that would enforce a Linux kernel to implement an action like drop, modify, or inspect network packets.
In a Linux device or machine, enabling the iptables will act as a router or/and Network Firewall.
Distinct programs and modules of the kernel are used for distinct protocols such as IPtables applies on IPv4, arp tables on ARP, ip6tables on IPv6, and ebtables on Ethernet frames.
Later a project called Netfilter developed the Nftables for scalability and performance. It is a framework for the packet filtering process that does a similar job to Iptables.
Iptables is used for filtering packets according to:
- Tables: These are files that can join the same operations. A table is composed of various chains.
- Chains: The chains are the rule's string. Ipatales finds an appropriate table if any packet is received, then executes it from the rule's chains until it searches for a match.
- Rules: The rules are the statement that informs a system what needs to do with the packets. They can block a single packet type, or forward other types of packets. The result, in which a packet is transferred, is known as the target.
- Targets: The target is a determination of what needs to do with the packets. It is typically is for accepting it, rejecting it, or dropping it (which transfers the error back to a sender).
Chains
A chain is a group of rules described for a specific task.
There are three types of chains that can be used for processing the traffic:
- FORWARD Chains
- OUTPUT Chains
- INPUT Chains
1. FORWARD Chains: The traffic which is arising from the network (external) and going to other networks requires to go from the forward chain. It can be used if two or more systems are linked and we wish to transfer data between them.
2. OUTPUT Chains: The traffic going through our local machine towards the Internet requires us to go from these output chains.
3. INPUT Chains: The traffic arising through the network (internal) to our local machine will go from the input chains. It means they need to go from every rule that has been fixed up within the input chains.
Tables
The iptables of the Linux firewall contain four tables by default. We will list every four tables.
1. Filter
This table is widely used. It works as the bouncer and determines who gets out and in of our network. It contains some default chains such as forward, input, and output chains.
2. Network Address Translation (NAT)
It includes rules of Network Address Translation (NAT) to route packets to the networks that can't be directly accessed. If the source or destination of a packet has to be modified, then the NAT table will be used. It contains some chains which are mentioned below:
- Prerouting: It is used for assigning the packets as soon as a server gets them.
- Output: This chain acts similarly to the output chain that we explained above.
- Postrouting: It permits to make of alterations to the packets after these packets leave the output chain.
3. Mangle
This table is used for adjusting the packet's IP header properties. It contains every chain we explained above:
- Forward
- Input
- Output
- Postrouting
- Prerouting
4. Raw
This table is used for exempting packets through connection tracking. It contains two chains:
5. Security
This table is optional. Some of the Linux versions use the Security table for managing unique access rules. It contains forward, input, and output chains.
Targets
The target is what goes on after the packet matches any rule criteria. Many targets (non-terminating) keep matching various packets with rules within a chain even if a packet is matching a rule.
The packet is immediately evaluated and isn't matched with other chains in the terminating targets.
Different Types of Policies
There are three different actions that an iptables can implement over the traffic:
- ACCEPT
- REJECT
- DROP
- RETURN
1. ACCEPT: The iptables will accept the traffic when the traffic passes some rules in the specified chain. It means it opens up many ways and permits the user to access the rules and regulations.
2. REJECT: This action is the same as the drop action. However, it transfers a message to a sender of any traffic illustrating that the transfer of data has failed.
We can use the REJECT action as a normal rule when we wish another end to understand the port is unavailable.
3. DROP: The iptables can block any traffic when it can't pass the rules inside the specified chain. It means that the firewall has closed.
Note: We need to remember a general rule here:-
In the iptables, the rules we set are inspected through the topmost rules towards the bottom. It is permitted to pass a firewall whenever the packet passes any top rule. The lower rules aren't inspected. Hence, we have to be careful at the time of setting up the rules.
4. RETURN: It transfers a packet back to the producing chain so we could match it with other rules.
Configure and install firewall iptables in Ubuntu
By default, the iptables is installed on most of the Linux distros. We can use the following command to ensure that iptable is available on our system:
Syntax and options in iptables
The command for iptables generally looks like below:
The following are some of the frequently used options of iptables:
- --append, -A: It is used for adding any rule to the end of a chain.
- --check, -C: It looks for the rule that is matching with the requirements of a chain.
- --delete, -D: It removes the defined rule from the chain.
- --flush, -F: It removes every rule from a chain.
- --insert, -I: It is used for adding any rule to the chain at a specified position.
- --list, -L: This option is used for displaying every rule within a chain.
- --new-chain, -N: It makes a new chain.
- --verbose, -V: It displays more details if using this option.
- --delete-chain, -X: It deletes a given chain.
Note: Ensure that we are using the appropriate option because iptables is case-sensitive.
Basic Command of iptables
1. List the iptables current rules
We can use the following command for listing the iptables current rules:
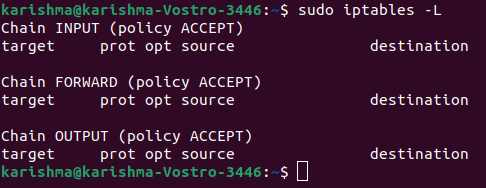
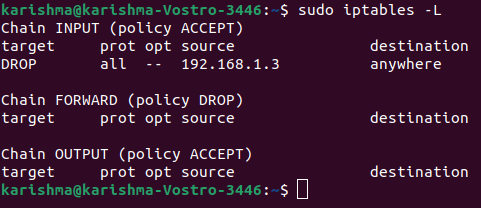
As we can check, there are three chains available (FORWARD, INPUT, OUTPUT). Also, we can check column headers. However, they are not original rules. It is because almost all Linux does not come with predefined rules.
Let's discuss the meaning of all the columns:
Target:
It specifies what operation requires to be implemented on the packet (ACCEPT, REJECT, DROP).
prot:
It specifies the protocol (IP, TCP) of a packet.
source:
It defines the source address of a packet.
destination:
It specifies the destination address of a packet.
2. Clear Rules:
If we ever wish to flush out or clear every existing rule, then we can execute the below command:
It will reset the iptables.
3. Modifying the default chain policy
The syntax is as follows:
The default policy of all chains is ACCEPT in the above screenshots.
For example,
We will check "Chain FORWARD (policy ACCEPT)" if we check the forward chain. It means our computer permits the traffic to forward to another computer.
We can use the following command to modify the forwarding policy to drop:
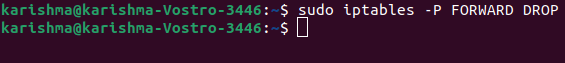
It will stop the traffic to forward from our computer. It means no other computers can access our computer for passing the data as an intermediary.
Creating our First Rule
1. DROP rule
Now, we will start building the policies of the firewall. First, we will work on an input chain in which the traffic (incoming) will be transferred through.
Syntax:
We will take an instance for understanding this topic:
Let's think we wish to block any traffic coming through the 192.168.1.3 IP address. The below command could be used:
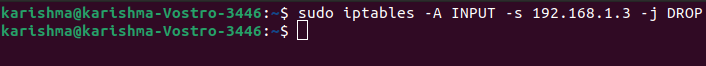
It may look typical, but it will make sense if we proceed over the elements:
-A INPUT
The -A flat is used for appending a rule to the chain's end. This segment of the command defines that the iptables that we wish to include a rule towards the INPUT chain's end.
-I INPUT
The rules are included to the chain's top in this flag.
-s 192.168.1.3
The -s flag is used for specifying the packet source. It tells an iptable to check for a packet coming through the 192.168.1.3 source.
-j DROP
It describes what an iptable must do with a packet. The command includes the rules to an INPUT chain which is mentioned above. It says if a packet comes whose IP address is 192.168.1.3, drop the packet, which means don't permit that packet to reach the system.
Once we run the command we can check the modifications with the help of the following command:
2. ACCEPT rule
If we wish to add the rules to the particular ports of our network, we can use the following command:
Where,
-p protocol_name
It is used for matching those packets that pursue the protocol_name protocol.
-dport port_number
It is available only when we provide the option, i.e., -p protocol_name. It defines to check many packets that are proceeding towards the "port_number" port.
For example,
Let's assume we wish to keep an SSH port open from the network 192.168.1.3 we blocked within the above condition. That is we just wish to permit those packets with 192.168.1.3 IP address and which wishes to reach the 22 port.
What will we do?
Let's try the following command:
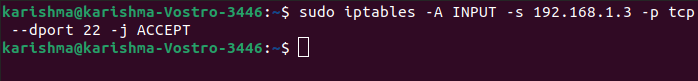
This command defines looks for those packets coming from the 192.168.1.3 IP address, having the TCP protocol, and wishes to provide something to the 22 port of our computer. If we find those kinds of packets, ACCEPT them.
As we explained earlier, in the iptables, the rules we set are inspected from top to the bottom. The packet is not inspected along with any lower rule whenever it is processed to any of the top rules.
But in our case, the packet was inspected using the top rule. It defines the iptable should drop the packets coming through the 192.168.1.3 IP address.
Hence, the packet didn't go to the upcoming rule once it got accessed from this rule which permitted the packets to the 22 port. So it failed.
What can be done?
We can add a rule to the chain's top. All we have to do is switch option -A to option -I.
The command for doing that is as follows:
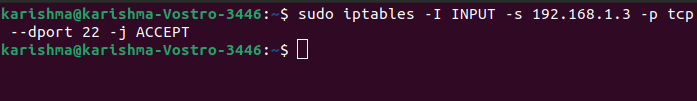
Now, we will check the configuration of iptable with -L option.
Hence, those packet originating from the 192.168.1.3 IP address is initially checked when it's going to the 22 port if it is not, it is executed from the next rule within the chain.
Otherwise, it is permitted for passing the firewall.
We have now understood to accept and block the traffic. Let's check how to remove or delete a rule.
3. Removing a rule through the iptable
Syntax:
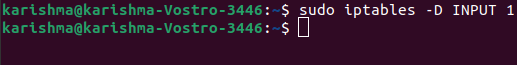
4. Saving our configuration
This segment is unnecessary if we are doing it on a PC that isn't a server. However, if we're implementing any firewall over the server, there are many chances that our server may get corrupted and we may lose all our data. Therefore, it is always better that we save our configurations.
There are so many ways for doing it, but the efficient way we find with iptables is- persistent package. We can download this package from the default repositories of Ubuntu:
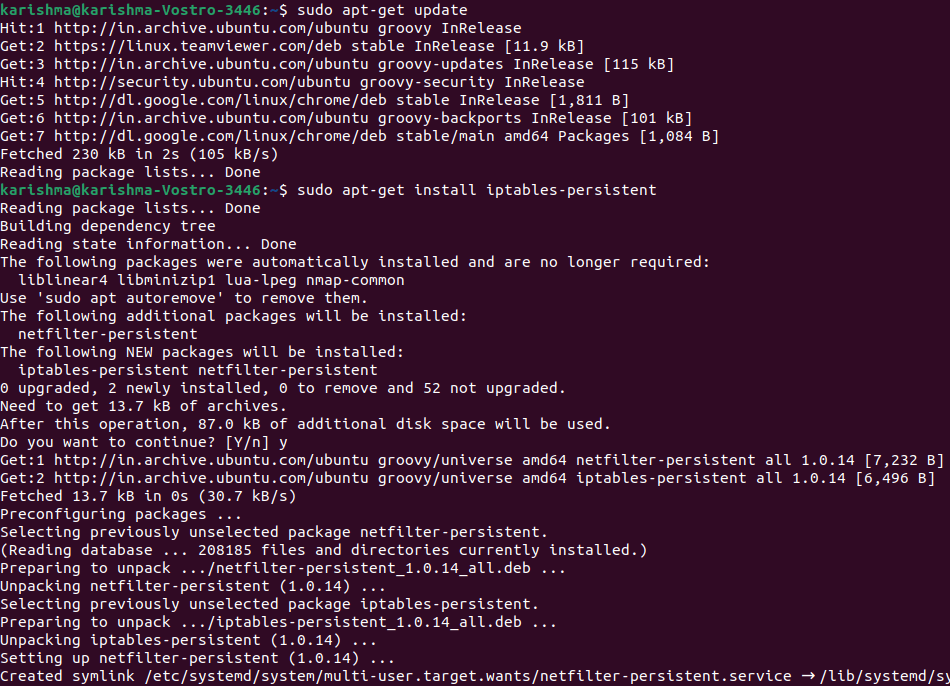
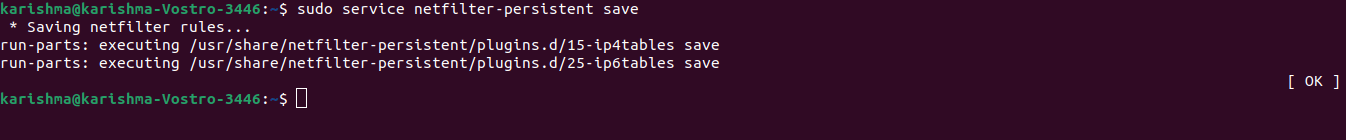
We can save our configuration with the help of the following command once the process of installation is complete:
|  For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now





















