How to check open ports in LinuxBriefly, we will describe ports within the computer networking and further, we will talk about how we can list every open port in Linux. A port can be defined as a logical entity in computer networking and software terms. It acts as a communication endpoint for identifying a given process or application on the Linux operating system. A port is a 16-bit (o to 65535) number that differentiates a single application from others on various end systems. Two of the most famous Internet transport protocols, User Datagram Protocol (UDP) and Transmission Control Protocol (TCP) and other protocols apply port numbers for many sessions of communication (destination and source port numbers in conjunction with the destination and source IP addresses). A combination of a protocol, port, and IP address like TCP/UDP is called a socket. It is necessary that all the services should have a specific socket. Categories of PortThese ports are divided into three categories for ease of use because the variety of ports is large. All the categories are labeled as the port value range: 0-1023: These ports are well-known and called "System" ports. They are reserved for the processes of the system that provide a huge range of network services. A process should have the privileges of a superuser for binding with any "Well-known" port. 1024-49151: These ports are "Registered" and called the "User" ports. They are designated via IANA for unique services. A process might have authentication to them upon request. It does not need any privilege of a superuser for using these ports in the most systems case. 49152-65535: These ports are "Dynamic" and called the "Private" ports. They can not be registered with IANA. These types of ports are open for using for customized and private services and may also be allocated as the ephemeral ports (known as short-lived ports applied by IP) automatically. There are so many ways for checking open ports in Linux. By default, a port will close unless any application is applying it. A port should be assigned to a process or service if it is open. Open Ports ListIt is easier to know which port is in use instead of which port is open. Hence, the below section will provide methods for listing every port that is in use currently. There are several tools present for this task in Linux. Most of them available built-in in a Linux distribution. Learning which port is currently open could be helpful in many scenarios. It is possible to determine a dedicated port for an assured application. An open port might be a strong intrusion indication within the network. The methods are used on Ubuntu 20.04 LTS which are mentioned below. List open ports and protocols using /etc/services fileThe file, i.e., /etc/services contains details about the running services (currently). It is a large file. 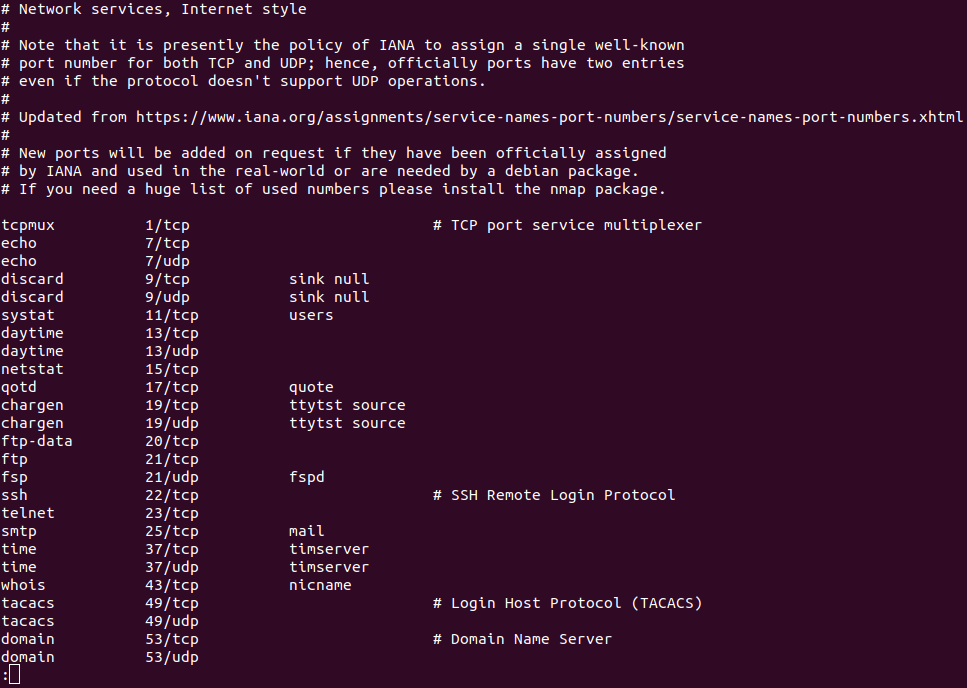
List open ports with netstatThe netstat tool can be described as a utility to display network connections for routing tables, TCP, and several network interfaces. Also, it facilitates statistics of network protocol. We could list every open port of a system by using the netstat tool. We can execute the below command: 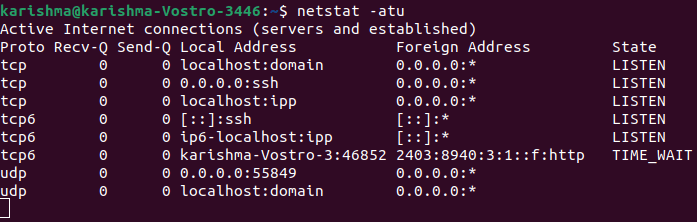
Let's quickly explain the breakdown of each flag that we used in the above command: 1. a: This flag informs netstat for displaying each socket. 2. t: This flag informs netstat for listing TCP ports. 3. u: This flag informs netstat for listing UDP ports. The netstat command has another variation which is mentioned below: 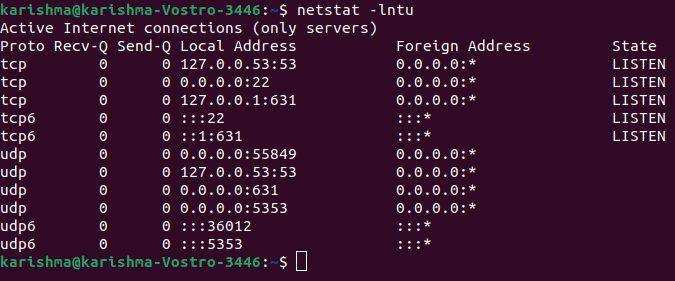
Two flags are new in the above command which is explained as follows: 1. l: This flag informs netstat for printing the listening sockets only. 2. n: This flag informs netstat for showing the port number. We can use a flag, i.e., "-p" to show the process PID that is using any port. 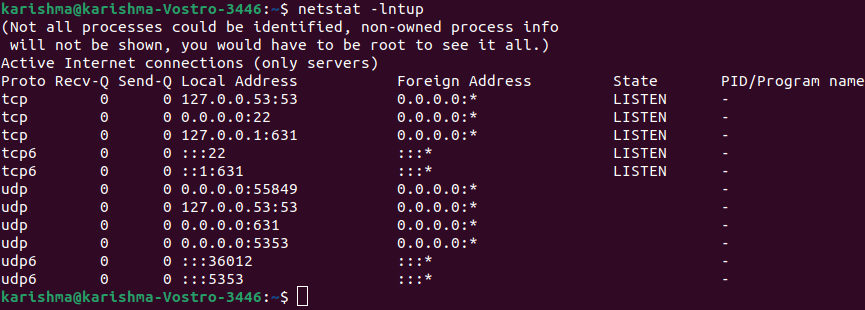
Check open ports locallyThe netstat command is available on every computer operating system for monitoring network connections. The below command applies netstat to display each listening port with the TCP protocol: 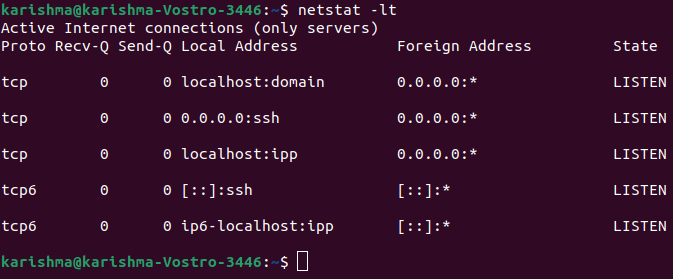
Let's briefly define the flags which are present in the above command: 1. -l: It lists the listening ports. 2. -t: It specifies the TCP protocol. The result is well ordered in columns displaying the protocol, human friendly, sent and received packets, port state, remote and local IP addresses. If we modify the TCP protocol for UDP protocol, then the output will show open ports only. The result will show without describing the state due to contradiction to the TCP protocol. 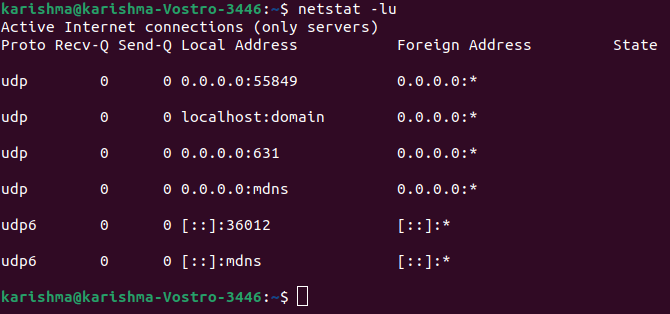
We can ignore describing protocols and apply only the option --listen or -l for getting details on each port listening freely of the protocol: 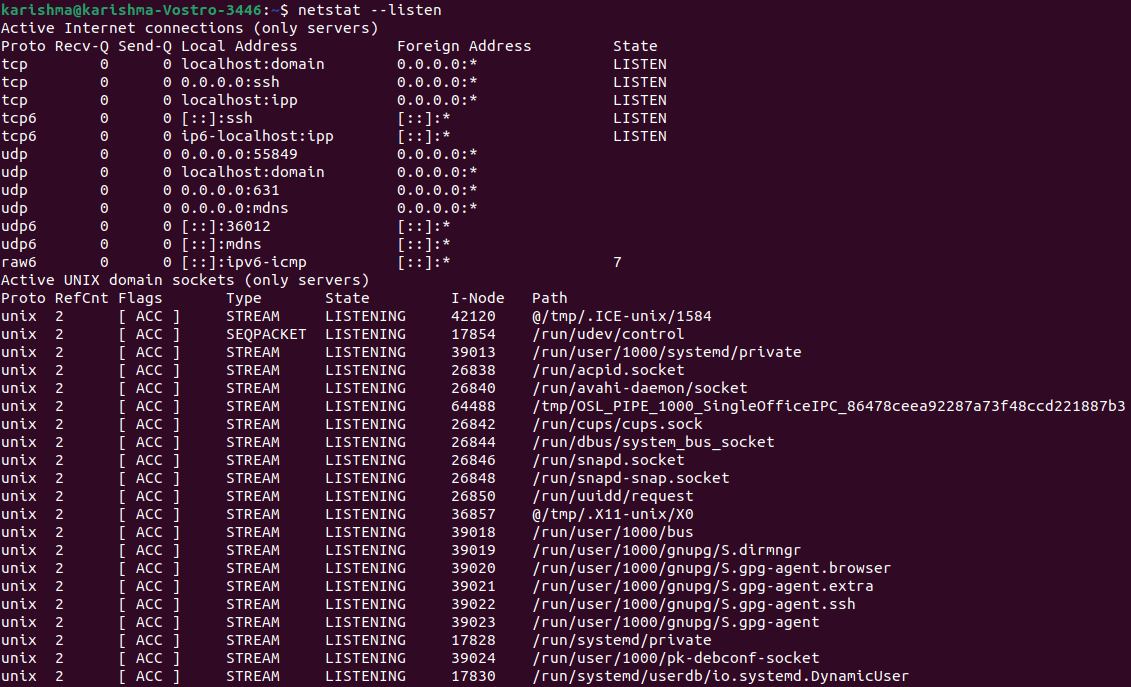
The above option will show the details for Unix, UDP, and TCP socket protocols. Every example above displays how to print the details over listening ports without authorized connections. The below commands display how to show listening ports and authorized connections. 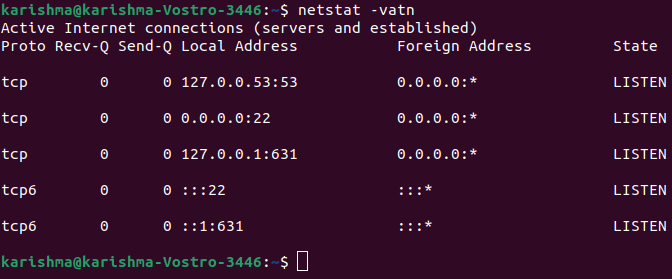
Where: 1. -v: It is used for verbosity. 2. -a: It displays active connections. 3. -t: It displays tcp connections. 4. -n: It displays ports (numerical value). Let's say we recognize a suspicious process within our system and we wish to check related ports to it. We can use the lsof command which is used for listing open files related to processes. Where, 1. -i: It lists the files collaborating with the Internet, the 6 option is present for IPv6, and the 4 option instructs for printing only IPv4. 2. -a: It instructs the result to be ANDed. 3. -p: It specifies the process PID number we wish to check. List open ports with ssThe ss tool can be specified as a utility to investigate the socket. The usage of this tool is the same as the netstat command. We can run the below command for listing the open ports: 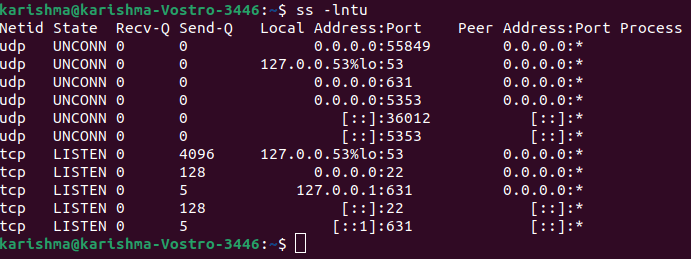
The above flags are the same as the netstat command. The functions which are described by the ss tool are quite the same as well. 1. l: This flag informs ss for displaying the listening sockets. 2. n: This flag informs ss not to attempt to conclude service names. 3. t: This flag informs ss for display TCP sockets. 4. u: This flag informs ss for displaying UDP sockets. List open ports with lsofThe lsof command can be used for listing open files. But, it can be used to display the open ports as well. We can execute the following command: 
For getting the open ports of a particular protocol (UDP, TCP, etc.) then specify it after using the "-i" flag, we can execute the following command: List open ports with nmapThe nmap command can be defined as a strong one for port/security scanning and network exploration. It can also report each open port within the system. We can execute the following command for listing the open TCP ports. 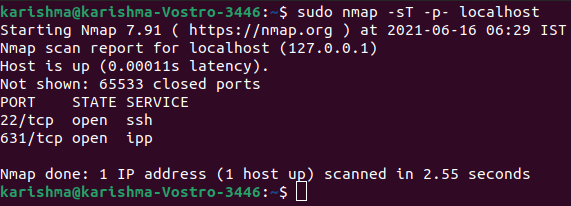
There are two sections of this command which is mentioned above: 1. -sT: It informs the nmap tool for scanning TCP ports. 2. -p-: It informs the nmap tool for scanning every 65535 ports. The nmap tool will scan 1000 ports only by default if not used. If we require to list the open ports of UDP, then we can execute the following command: 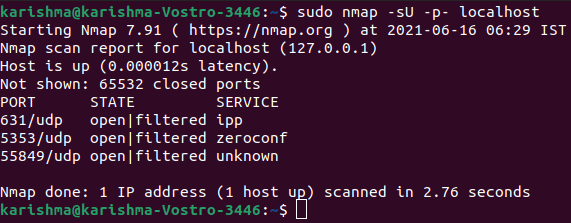
We can also execute the following command for getting both the UDP and TCP ports: 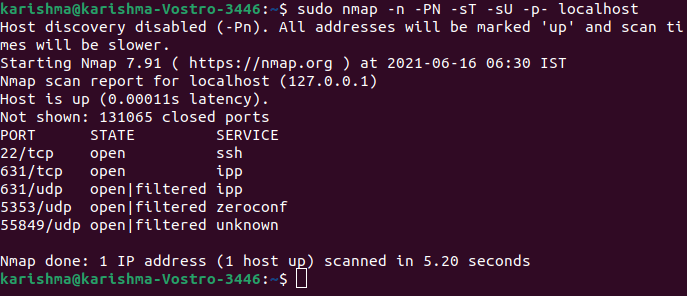
List open ports with netcatThe netcat tool can be described as a command-line utility to read and write data across many network connections on the UDP and TCP protocols. Also, it can be used to list open ports. This tool can implement tests over a particular port or a variety of ports. The below netcat command is used for scanning the port from 1-1000. By default, it will implement the scan over TCP protocol: 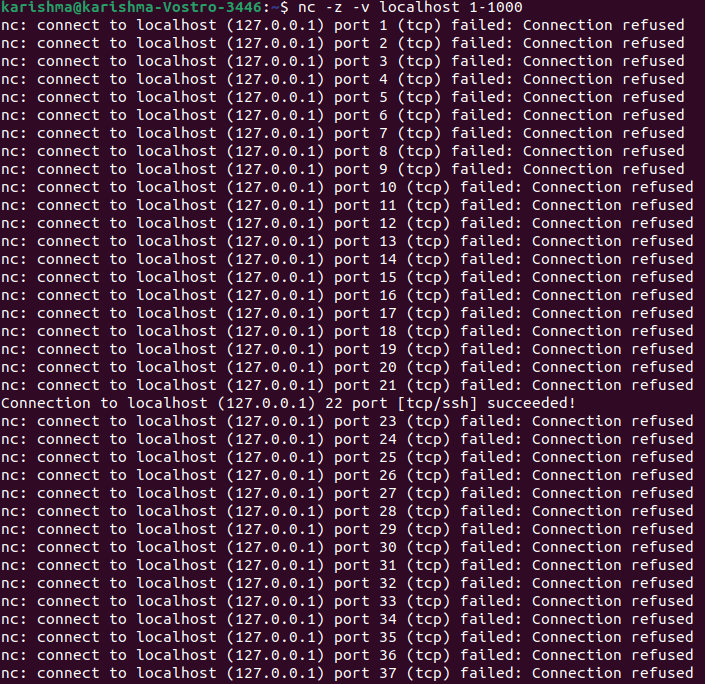
Also, it can be extended to the whole list of certain ports: 
Let's have a breakdown of these flags quickly. 1. z: It informs the netcat command for scanning open ports only, without transferring any data. 2. v: It informs the netcat command for running in verbose mode. We can filter the result with the help of grep for a term "succeeded" for getting only the open ports through this list. 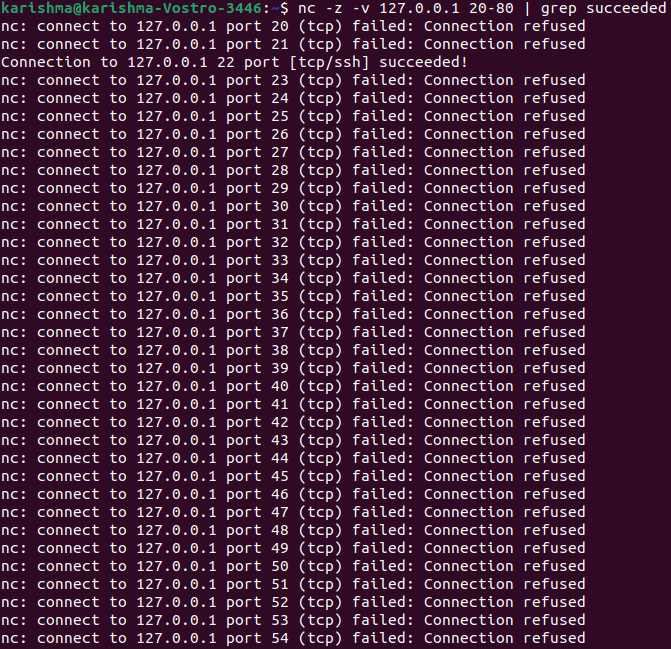
If we wish to implement the scan over UDP protocol, the. We can include the "-u" flag.
Next TopicLinux vs Ubuntu
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









