Python Tutorial
Python OOPs
Python MySQL
Python MongoDB
Python SQLite
Python Questions
Plotly
Python Tkinter (GUI)
Python Web Blocker
Python MCQ
Related Tutorials
Python Programs
Python JWTPython JWTJSON Web Token is a succinct, URL-safe mechanism to represent claims that need to be exchanged between two parties (JWT). It is frequently used to transport data between computers and authenticate users securely. We'll go through JWT's foundations and how to use them in Python in this tutorial. The JWT standard defines a clear and comprehensive technique for securely exchanging data between parties. This information can be verified and trusted because it is digitally signed. For instance, when a user signs into a website, JWT is frequently used to authenticate users and securely send information between systems. The header, payload, and signature of a JWT are represented as a three-part string that is divided into parts by dots (.). The two key parts of the header are the type of the token, which is JWT, and the signature technique being used, such as HMAC SHA256 or RSA. The assertions are in the payload. Claims consist of supplementary metadata and claims about an entity (usually the user). Registered, public and private claims are the three different categories of claims. In order to provide a collection of usable, interoperable claims, a set of predetermined claims known as registered claims is encouraged but not required. Iss (issuer), exp (expiration time), sub (subject), aud (audience), and other terms are examples of registered claims. The JWT's signature is used to confirm that the sender is who they claim to be and to guarantee that the message hasn't been altered along the route. In order to use JWT in Python, we need to install a library that supports it. There are several libraries available for encoding and decoding JWTs in Python, including PyJWT, Jose, and python_jose. In this article, we will use PyJWT as an example. First, we need to install the PyJWT library using pip: Once the library is installed, we can start using it to encode and decode JWTs. Let's start by encoding a JWT. Output 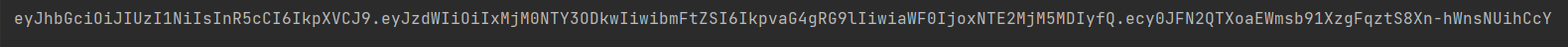
Explanation: In this example, we first defined the header and payload of the JWT. The header contains the signing algorithm (HS256) and the type of token (JWT). The payload contains the claims, such as the subject (sub), name, and issued at (iat) time. We also defined a secret key (Ravipass) that will be used to sign the token. Then we used the encode function from the PyJWT library to encode the payload and header with the secret key and algorithm. The function returns the encoded JWT as a byte string, which can be sent to the client or server. Now that we have encoded the JWT let's decode it to verify the claims. Output 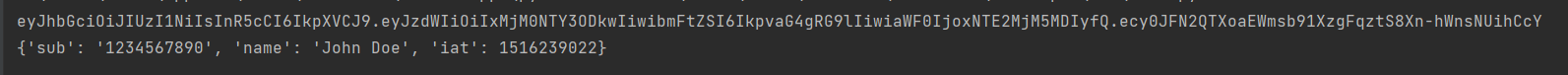
Explanation: This code demonstrates how to use the PyJWT library to encode and decode a JSON Web Token (JWT). The "header" variable is a dictionary containing the "alg" (algorithm) and "typ" (type) fields, which are set to "HS256" and "JWT," respectively. The "payload" variable is a dictionary containing information about the JWT's subject, name, and issue time. The "secret" variable is a string used as the key for encoding and decoding the JWT. The JWT is encoded using the jwt. encode() function, which takes the payload, secret, and algorithm as arguments. The encoded JWT is then printed to the console. The JWT is decoded using the jwt.decode() function, which takes the encoded JWT and secret as arguments. The decoded JWT is then printed to the console, which will give the original payload that we had encoded. It's also important to verify the signature of the JWT before trusting the claims. This can be done by passing in the verify parameter as True while decoding the JWT. Output 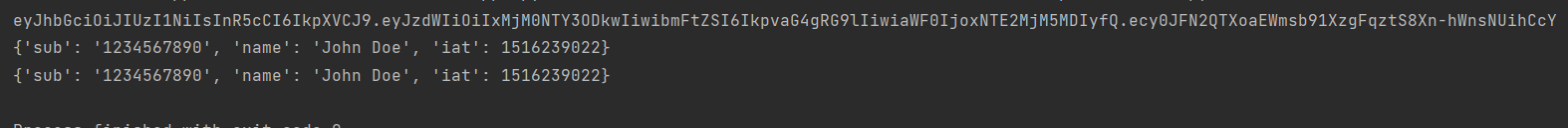
Explanation: In this example, the decode function will raise an InvalidSignatureError if the signature is invalid, and we can handle it with a try-except block. JWT is a strong standard for securely transferring information between parties, to sum up. With the aid of libraries like PyJWT, it is simple to implement in Python. It's important to keep in mind the security best practices, such as including expiration time and verifying the signature and expiration time of the token before trusting the claims.
Next TopicPython Learning Path
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









