DS Tutorial
DS Array
DS Linked List
DS Stack
DS Queue
DS Tree
DS Graph
DS Searching
DS Sorting
Differences
Misc
DS MCQ
Secure Message EncodingProblem StatementOne such developer, Recently graduated with a degree in Computer Science, has started a new employment opportunity at ShareChat and wants to develop an encoder for an application's messages. The encoding process involves two steps: Reverse adjacent characters in the string S, beginning with the first one. However, if the length of S is odd, then the last characters remain intact. Change every 'a' into a 'z', every 'b' into a 'y', every 'c' into an 'x', and so forth. Additionally, replace 'z' with 'a'. You will assist in implementing a secure message encoding. Design an algorithm that will receive as an argument the initial message represented in the string S after decoding it via the previously described stages. Input: This comes as the first line with the number of characters that comprise the message string, N. The next line holds a message string S made up of all lowercase English alphabet alone. Output: Print one line for each test case with the encoded message. Constraints: 1 ≤ T ≤ 100 1 ≤ N ≤ 100 The string S is made up of simple English lowercase letters alone. Note: Before getting into the solution would highly recommend to come up with an approach to gain greater insights of the problemJava Implementation of mentioned approachJava Approach 1Output: 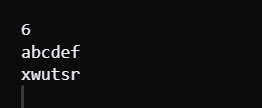
Code Explanation : Java code accepts integer n and string s. It turns characters in a string into an array of characters. For every even position index from 0 to n-1, it changes the places of these neighboring characters within the array. Finally, it replaces every character by complementing it using the formula (char)((219-(int)c[j])). The encoded characters are printed. To that effect, the code undertakes those operations consecutively so as to achieve the intended message encoding. Time Complexity : It has a time complexity of O(n) for an input string having n elements. The code iterates through the string twice: one pass for swapping adjacent characters and one pass for simple replacing of characters. The operation is linear in both iterations, so the total of time complexity is linear on input size. Space Complexity : That is, the space complexity is O(n), and n is a measure of the length of the input string. The input string is presented as a character array of length n in the code. According to the space required, it is a matter that scales with the length of the input. Java Approach 2 Using HashMapJava Code Output: 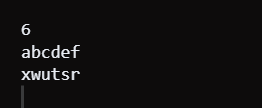
Code Explanation : They give an integer n and a string st as inputs. It initiates an instance of HashMap in which it pairs a character that ranges from 'a' to 'z' and its mirror reflection. It then switches two consecutive characters of the string, applies the cipher algorithm, and writes out the encrypted text. It also does this effectively by utilizing Hashmap for character mapping. Time Complexity: Its time complexity is O(n), where 'n' is the length of the input string. It carries out two consecutive operations - switching adjacent characters as well as mapping characters, which are all achieved in one pass of the string with linear time complexity. Space Complexity : Additional space used does not depend on input size, and hence, space complexity is O(1). HashMap has fixed twenty-six key-value pairs, while the character array is encoded as Mod.
Next TopicSort an almost sorted array
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









