Cyber Security DefinitionCybersecurity (cyber security), also known as information technology security (IT security), is the defense of computer systems and networks from malicious actors who want to compromise data security, steal data, steal hardware, software, or data, or interrupt or reroute the services that computers and networks offer. 
The use of computers, the Internet, wireless network protocols like Bluetooth and Wi-Fi, as well as the growth of smart gadgets like smartphones, televisions, and other components of the Internet of things (IoT), have all contributed to the topic's rising prominence. One of the major issues in the current world is cybersecurity because of how complicated information systems and the societies they support are. Security is crucial for large-scale systems that have significant physical effects, such as those that manage banking, elections, and electricity distribution. History:The term "cybersecurity" has become widely discussed in both our professional and personal lives with the development of the Internet and the start of the digital transformation in recent years. Throughout the past 50 years of technology advancement, cybersecurity and cyber dangers have always existed. Prior to the invention of the Internet, when increased connectedness led to a surge in computer viruses and network breaches, computer security in the 1970s and 1980s was primarily confined to academics. Following the rise of viruses in the 1990s, the 2000s saw the institutionalisation of cybersecurity and cyberthreats. A key turning point in the development of computer security was the session Willis Ware convened at the Spring Joint Computer Conference in April 1967 and the subsequent release of the Ware Report. The concerns of politics, culture, society, and the economy were all entwined in Ware's work. The CIA triumvirate of availability, integrity, and confidentiality was first suggested in a 1977 NIST article as a straightforward and concise approach to explain important security objectives. Many more complex frameworks have subsequently been suggested, though they are still applicable. However, there were no significant computer threats in the 1970s and 1980s because computers and the internet were still in their infancy and security risks were easy to detect. Threats were typically made by insiders who were malicious and had accessed private information without authorization. Although there was malware and network breaches in the beginning, they were not used for monetary benefit. In the second half of the 1970s, well-known computer companies like IBM started offering access control systems and computer security software. The computer worm Creeper, created by Bob Thomas at BBN and spread across the ARPANET in 1971, is one of the early instances of an attack on a computer network. There was no harmful payload in the application; it was only experimental in nature. Ray Tomlinson developed a later programme called Reaper in 1972, and it was this programme that obliterated Creeper. A group of German hackers conducted the first recorded case of cyber espionage between September 1986 and June 1987. In order to obtain information, the organisation broke into the networks of American universities, military bases, and defence companies. After that, they sold the information to the Soviet KGB. The group's leader, Markus Hess, was arrested on June 29, 1987. On February 15, 1990, he and two other people were found guilty of being agents of foreign intelligence. The Morris worm, one of the earliest computer viruses, was disseminated online in 1988. That attracted a lot of attention from the media. In 1993, the National Centre for Supercomputing Applications (NCSA) published Mosaic 1.0, the initial web browser. Soon after, Netscape started developing the SSL protocol. In 1994, Netscape was ready to deploy SSL version 1.0, but a number of significant security flaws prevented it from being made available to the general public. Replay attacks and a flaw that let hackers manipulate user-send unencrypted communications were two examples of these flaws. Version 2.0 of Netscape was nevertheless launched in February 1995. The National Security Agency (NSA), in addition to acquiring foreign intelligence, is in responsibility of protecting American information networks. In order to identify security flaws, the agency examines widely used software. It then saves these vulnerabilities for use in offensive operations against American rivals. Rarely does the agency engage in defensive measures like reporting problems to software developers so they can fix them. NSA contractors created and sold close friends and US government agencies with click-and-shoot attack capabilities, but eventually those adversaries were on the other side of the world. Russia and North Korea have both exploited the NSA's own hacking tools, which were breached in 2016. Employers and contractors at the NSA have been sought out by rivals eager to engage in cyberwarfare at high salaries. Since the US and Israel began exploiting security flaws in the Microsoft Windows operating system in 2007, Iran's nuclear material processing equipment has been targeted and damaged. Iran invested heavily in its own cyberwarfare capabilities as retaliation, which it then began using against the United States. Attacks and Vulnerabilities:A vulnerability is a flaw in the planning, carrying out, running, or internal control of something. The vast majority of known vulnerabilities have descriptions in the Common Vulnerabilities and Exposures (CVE) database. There must be at least one successful attack or exploit to qualify as an exploitable vulnerability. Automated tools or custom scripts can be used to find, investigate, look for, or exploit vulnerabilities. Understanding the potential attacks on a computer system is crucial for its security, and these dangers may often be grouped into one of the following categories: Backdoor:Any covert means of getting beyond standard authentication or security restrictions is known as a backdoor in a computer system, cryptosystem, or algorithm. Many factors, such as faulty arrangement or original design, may have led to their existence. Whatever the motivations for their addition, they constitute a vulnerability. They might have been added by an authorised person to permit some legal access or by an attacker with bad intent. Backdoors can be quite difficult to spot, and they are typically only found by someone with access to the source code of the relevant applications or in-depth knowledge of the computer's operating system. Denial-Of-Service Attack:A system or network resource is intended to be made inaccessible to its intended users using denial of service (DoS) attacks. Attackers may choose to lock down a victim's account by purposefully inputting the wrong password enough times in a row, or they may overtax a computer or network's resources and block all users at once. Attackers may also choose to restrict service to specific victims. While a network attack from a single IP address can be halted by adding a new firewall rule, a variety of Distributed denial of service (DDoS) attacks are possible, where the attack comes from a big number of sites - and defending is far more difficult. Such assaults can come from zombie computers in a botnet or from a variety of other methods, like distributed reflective denial of service (DRDoS), in which unwary systems are tricked into delivering traffic to the target. As a result of using less bandwidth themselves, the amplification factor in such attacks facilitates the attack for the attacker. Direct Access Assaults:Data from a computer can most likely be immediately copied from it by an unauthorised person who physically gains access to it. By altering the operating system, installing software worms, keyloggers, hidden listening devices, or employing wireless microphones, they might also jeopardise security. Even when the workstation is secured, standard security measures can be disregarded by booting another operating system or as tool from a CD-ROM or other bootable media. These attacks are guarded against by disc encryption and the Trusted Platform Module. Eavesdropping:Eavesdropping is the illegal practise of secretly listening in on a private computer conversation (communication), usually between hosts connected to a network. For instance, to spy on internet service provider networks, the NSA and Federal Bureau of Investigation (FBI) have used programmes like Carnivore and NarusInSight. By observing the flimsy electromagnetic emissions produced by the hardware, it is possible to listen in on even closed systems (i.e., devices that have no communication with the outside world). The NSA has defined these attacks under the term TEMPEST. Attacks with Several Vectors and Variety:Several different types of assaults were integrated into one new class of multi-vector, polymorphic cyber threats that first surfaced in 2017. These threats also altered their forms as they spread to get around cybersecurity measures. Phishing:Phishing is the practise of tricking consumers into handing over personal data including usernames, passwords, and credit card numbers. Phishing frequently instructs visitors to enter their personal information at a phoney website that has a nearly identical look and feel to the real one. It is typically carried out using email spoofing or instant messaging. Personal information, including passwords and login information, is frequently requested by the bogus website. Once access to the person's actual account on the actual website has been gained, this information can be utilised to do so. Phishing is an example of social engineering because it preys on the victim's confidence. To access actual accounts, attackers employ innovative strategies. Attackers frequently trick people by sending them bogus electronic invoices that appear to show that they recently bought music, apps, or others and tell them to click a link if the sales were not approved. Spear phishing is a more deliberate form of phishing in which the attacker impersonates a reliable source by using details about the victim's identity or the details of their company. As opposed to the wide net that phishing attempts cast, spear-phishing attacks specifically target certain people. Increasing Privilege:Privilege escalation refers to a circumstance in which an attacker with a limited amount of access is able to increase their access level or privileges without being given permission. For instance, a regular computer user may be able to take advantage of a system vulnerability to access data that is restricted, or even become root to have full, unlimited access to a system. Engineering in Reverse:Reverse engineering is the process of dissecting a human-made object to reveal its designs, code, and architecture or to extract knowledge from the object, much like scientific research. The only distinction is that scientific study focuses on a natural occurrence. Attack From the Side:All computational system has some sort of impact on its surroundings. This impact it has on its surroundings is determined by a wide range of factors, including electromagnetic radiation, residual effects on RAM cells that make a Cold boot attack feasible, and hardware implementation errors that permit access to and/or guessing at other values that ordinarily should be inaccessible. In side-channel attack scenarios, the attacker would gather this knowledge about a system or network to make an educated guess as to its internal status and then access the data that the victim believes to be secure. Use of Social Engineering: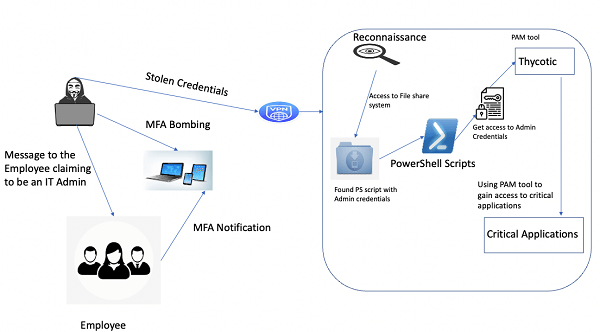
In terms of computer security, social engineering involves assuming the identity of a senior executive, bank, contractor, or client in order to convince a user to divulge information like passwords, card numbers, etc. or grant physical access. This typically entails taking advantage of people's trust and cognitive biases. A typical fraud involves sending emails to members of the accounting and finance departments pretending to be their CEO and pleading for them to take immediate action. The FBI reported that such business email compromise (BEC) schemes have cost American companies more than $2 billion in just over two years at the beginning of 2016. The Milwaukee Bucks Basketball club fell victim to this kind of cyber fraud in May 2016, when a perpetrator pretended to be Peter Feigin, the team president, and obtained the 2015 W-2 tax forms for every member of the team. Spoofing:Spoofing is the act of pretending to be an approved entity by inventing data (such as an IP address or username) in order to get access to information or resources that one is not otherwise entitled to use. Several different types of spoofing exist, such as:
The cybersecurity company Trellix produced research on the potentially fatal risk of spoofing in the healthcare sector in 2018. Tampering:Data that has been maliciously modified or altered is referred to as tampering. a deliberate but illegal act that alters a system, a system's component, a system's intended behaviour, or data. Examples include "Evil Maid" attacks and the installation of surveillance software by security agencies into routers. Malware:
When malicious software (malware) is installed on a computer, it has the ability to corrupt or permanently wipe data as well as expose any information, including passwords, financial information, and personal and commercial information. It can also give the attacker control of the machine. Smuggling HTML:"By concealing harmful payloads inside of ostensibly benign HTML files," the authors write, "adversaries may smuggle data and files past content filters." - Mitre.org Culture of Cybersecurity:Organizational information security can be greatly impacted by employee behaviour. The efficacy of various organisational segments with regard to information security can be influenced by cultural conceptions, which can also be used against them. "...the totality of patterns of conduct in an organisation that contribute to the protection of information of all sorts" is what information security culture is. Employees frequently act in a way that thwarts organisational reforms because, according to Andersson and Reimers (2014), they do not view themselves as contributing to their organization's information security efforts. As a matter of fact, the Verizon Data Breach Investigations Report 2020, which looked at 3,950 security breaches, found that 30% of cybersecurity events involved inside actors within a firm. According to research, the culture surrounding information security needs to be constantly improved. In "Information Security Culture from Analysis to Change," the authors stated, "It's a never-ending process, a cycle of evaluation and reform or maintenance." Five steps?pre-evaluation, strategic planning, operational planning, implementation, and post-evaluation?should be followed to manage the information security culture.
Systems at Risk:As the number of computer systems grows and as people, organisations, sectors of industry, and governments rely more and more on them, there are more and more systems at danger. Financial Structures:The systems of financial institutions and regulators, such as the U.S. Securities and Exchange Commission, SWIFT, investment banks, & commercial banks, are common targets for hackers attempting to influence markets and earn illegal gains. Websites and apps that take or store credit card numbers, trading account information, and bank account information are also common hacking targets since they offer the chance to make an instantaneous profit through money transfers, purchases, or the selling of the information on the black market. Customers' account information and PINs have also been obtained through hacking ATMs and in-store payment systems. Services and Machinery Used in Industry:The management of communications, the electrical grid, nuclear power plants, as well as the opening and closing of valves in water and gas networks are all activities that many utilities utilise computers to do. It was demonstrated by the Stuxnet infection that even devices run by computers not linked to the Internet could be vulnerable. The Internet provides a potential attack vector for such devices if connected, but even if not connected, it is still possible to compromise them. Investigations of 79 hacking incidents at energy businesses were conducted in 2014 by the Department of Homeland Security's Computer Emergency Readiness Team. Aviation:Several intricate systems that could be attacked are heavily dependent on by the aviation sector. Controlling Aeroplanes across oceans is particularly risky since radar monitoring only extends 175 to 225 miles offshore, a simple power outage at one airport can have effects on the entire planet, and much of the system depends on radio broadcasts that could be interfered with. In an aeroplane, there is also a chance of assault. In Europe, with the (Pan-European Network Service) and NewPENS, and in the US, with the NextGen plan, air navigation service providers are taking measures to establish their own specialist networks. If an assault is successful, there could be a variety of negative effects, including loss of secrecy, system integrity loss, disruptions in air traffic control, aircraft loss, and even human life loss. Consumer Electronics:In order to build a botnet to attack a different target, desktop computers and laptops are frequently attacked in order to collect passwords, financial account information, or both. Smartphones, tablets, smart watches, and other mobile devices, such as activity trackers and other quantified self gadgets, have sensors like cameras, microphones, GPS receivers, compasses, & accelerometers that might be used for nefarious purposes and might be able to gather private health data. Any of these devices might potentially be attacked through WiFi, Bluetooth, or mobile phone networks, and after a successful intrusion, sensors could be remotely triggered. Another group of possible targets is the growing number of home automation gadgets like the Nest thermostat. Major Companies:Common targets include big businesses. Attacks frequently involve data breaches and are intended to steal people's identities for financial benefit. Examples include the disclosure of Home Depot, Staples, Target Corporation, and Equifax regarding the theft of millions of customers' credit card and bank information. Identity theft in general, health insurance fraud, and patient impersonation to get prescription medications for personal use or resale have all targeted medical records. Despite the fact that cyber risks are on the rise, 62% of all firms did not boost security training for their workforce in 2015. However, not all attacks are carried out for financial gain. For instance, hacktivist group Anonymous launched a serious campaign of attacks against security firm HBGary Federal in 2011 in retaliation for the CEO of the firm alleging to have infiltrated the group, and Sony Pictures was targeted by hackers in 2014 with the apparent dual goals of embarrassing the organisation through leaks of information and crippling the company by removing workstations and servers. Automobiles:More and more features in cars are automated, including engine timing, cruise control, anti-lock brakes, seat belt tensioners, door locks, airbags, and advanced driver aid systems on many models. Furthermore, WiFi and Bluetooth may be used by connected cars to connect to onboard consumer electronics and the cellular network. Self-driving automobiles are anticipated to be considerably more complicated. These systems all have certain security risks, and these problems have received a lot of attention. Basic examples of danger include a malicious CD being used as an attack vector and the onboard microphones of the car being exploited for eavesdropping. If access is acquired to a car's internal controller area network, the risk is greatly increased. In a well-publicized test in 2015, hackers remotely carjacked a vehicle from a distance of 10 miles and drove it into a ditch. Different manufacturers are responding, with Tesla in 2016 downloading some security upgrades over the air to its cars' systems. The United States Department of Transportation called for states to develop unified regulations for autonomous vehicles and released some early safety guidelines in September 2016. Government:Activists and foreign forces frequently assault computer networks used by the government and the military. Infrastructure used by municipal and regional governments, including traffic light controllers, communication between law enforcement and intelligence departments, student and employee data, and banking systems, is also vulnerable to assault. This is because these systems are now largely computerised. Cloning is a possibility for government identification documents like passports and government ID cards that regulate entry to RFID-enabled buildings. Internet of Things and Physical Weaknesses:The Internet of Things (IoT) is a network of actual physical objects, including machines, vehicles, and buildings, that are equipped with electronics, software, sensors, and network connectivity. This technology allows these objects to gather and share data. There have been complaints that the security issues involved are not being properly taken into account while this is being created. The Internet of Things (IoT) offers prospects for a closer integration of the real world with computer-based systems, but it also presents risks for abuse. Cyberattacks in particular are anticipated to become a more physical (rather than merely virtual) menace as the Internet of Things expands. A burglar could enter the house at the touch of a button from a stolen or hacked phone if the front door's lock is connected to the Internet and can be locked or opened from a phone. In a world ruled by IoT-enabled devices, people risk losing far more than just their credit card information. Electronic tools have also been used by thieves to get around hotel door locks that are not connected to the Internet. A cyber-kinetic attack is one that targets human life or physical infrastructure. Cyber-kinetic attacks may spread and cause serious harm as IoT devices and appliances become more popular. Medical Systems:Both implantable devices like pacemakers and insulin pumps as well as diagnostic equipment used in hospitals have either seen successful attacks or had potentially fatal flaws exposed. Several claims have been made of hospitals and healthcare organisations being hacked, including ransomware attacks, viruses, Windows XP exploits, and data breaches involving sensitive information kept on hospital systems. On December 28, 2016, the US Food and Drug Administration published advice for medical device manufacturers regarding how to preserve the security of devices that are connected to the Internet, but no enforcement framework. Sector of Energy:The possibility of a cyber assault in distributed generation systems is actual, according to Daily Energy Insider. A big area may lose power for a protracted period of time due to an attack, which might have equally dire repercussions as a natural disaster. The District of Columbia is thinking about establishing a Distributed Energy Resources (DER) Authority in the area in order to give residents more control over how much energy they consume and to give the neighborhood's electric utility, Pepco, the opportunity to more accurately predict energy demand. But, the D.C. proposal "would permit third-party providers to establish numerous energy distribution points, thus increasing the opportunity for cyber attackers to pose a danger to the electric grid." Consequences of Security Breaches:Security breaches have resulted in significant financial loss, but as there is no accepted method for calculating the cost of an incident, the only information that is available is that which the organisations concerned make public. " The overall global damages attributed to worm and virus attacks as well as hostile digital actions in general are estimated by a number of computer security consulting companies. According to these companies, the losses from 2003 range from $13 billion (only from worms and viruses) to $226 billion (for all forms of covert attacks). These estimations are frequently questioned for their accuracy because the approach used to make them is essentially anecdotal." Although it may seem counterintuitive, companies can actually benefit from credible estimations of the financial cost of security breaches in order to make wise investment decisions. According to the traditional Gordon-Loeb Model, which examines the ideal investment level in information security, the sum a company spends to protect information should typically only be a small portion of the anticipated loss, or the anticipated value of the loss resulting from a cyber/information security breach. Motives of the Attacker:Computer security breaches are motivated for different reasons by different attackers, just like physical security breaches are. Some are vandals or thrill-seekers, some are activists, and still others are thieves out to make money. Yet, amateurs like Markus Hess, who worked for the KGB, were the first state-sponsored hackers, as Clifford Stoll describes in The Cuckoo's Egg. Today, these attacks are frequent and well-resourced. 
Recent assailants have also been motivated by extreme groups looking to advance their political agendas or obstruct social movements, which can be linked to previous attacks. As capabilities have increased as a result of the development of the internet, mobile technologies, and low-cost computing devices, there is also a risk to surroundings that are thought to be essential to business operations. The susceptibility of all crucial targeted environments has led to a number of proactive research on how to move the risk while considering the goals of these types of actors. The motive of hackers and nation state actors attempting to attack based on an ideological preference differ significantly in a number of important ways. Finding out what might spur an assault on a system and who might be driven to breach it is a basic component of threat modelling for any given system. Depending on the system that needs to be protected, different levels and types of measures will be used. Even when the basic technology are the same, the risks faced by a home computer, bank, and a classified military network are significantly different. Computer Security (Prevention Measures):A countermeasure in computer security is an activity, tool, process, or technique that lessens a risk, a weakness, or an attack by eradicating it or preventing it, minimising the damage it can do, or by identifying and reporting it so that remedial action can be taken. The following sections include a list of some widespread defences: Design-Based Security:Software that has been created from the ground up with security in mind is said to be secure by design, or secure by design. Security is seen as a key component in this situation. The following are some of the methods used in this strategy:
The Security Architecture:IT security architecture is described by the Open Security Architecture organisation as "the design artefacts that outline the placement and relationship of security controls (also known as security countermeasures) within the broader information technology architecture. These measures are taken to maintain the system's quality characteristics, including its availability, accountability, and secrecy ". Security architecture is described by Techopedia as "a comprehensive security plan that takes into account both the requirements and dangers present in a particular situation or environment. Additionally, it details where and when to implement security controls. In general, the design process is repeatable." Security architecture's most important characteristics are:
The correct framework is provided by security architecture practise to methodically address business, Technology, and security issues in an organisation. Security Precautions:The conceptual ideal, which is obtained by using the three procedures of threat prevention, detection, and reaction, is a state of computer security. The following policies and system elements, among others, form the basis for these processes:
In the modern day, computer security mostly comprises of preventive measures like firewalls or an exit procedure. A firewall is a method for filtering network traffic between a host or network and another network, like the Internet. A firewall is a device that provides real-time filtering and blocking capabilities. It can be implemented as software that runs on the computer that connects to the network stack, or, as is the case with the majority of UNIX-based operating systems, including Linux, as part of the operating system kernel. The use of a "physical firewall," which entails a separate machine screening network traffic, is another implementation. Machines with a constant Internet connection frequently have firewalls installed. Big data systems like Apache Hadoop are being used by certain businesses to increase data accessibility and use machine learning to find sophisticated persistent threats. Nevertheless, only a small number of businesses maintain computer systems with reliable detection systems, and even fewer have well-planned response processes in place. Consequently, according to Reuters, "Businesses for the first time report they are losing more through electronic theft of data than physical theft of goods." An over reliance on firewalls and other automated detection systems might be connected as the principal obstacle to the effective eradication of cybercrime. But, putting offenders in jail is a simple matter of obtaining evidence using packet capture devices. The cornerstone of information security is the confidentiality, integrity, and availability (CIA) of a network, which must be preserved in order to ensure acceptable security. Security measures should be used on an administrative, physical, and technical level to accomplish those goals. Only when an asset's value is understood can the level of security provided to it be calculated. Management of Vulnerabilities:Identification, correction, and mitigation of vulnerabilities, particularly those in software and firmware, make up the cycle of vulnerability management. Network security and computer security are both reliant on vulnerability management. A vulnerability scanner, which examines a computer system for known vulnerabilities such as open ports, unsafe software configuration, and susceptibility to infection, can find weaknesses. With each new version the vendor releases, these tools must be kept current in order to be useful. These upgrades often do a scan for any newly discovered vulnerabilities. Beyond scanning for vulnerabilities, a lot of companies use outside security auditors to do recurring penetration testing on their systems to find security holes. This is a contractual necessity in various industries. Minimizing Vulnerabilities:Although it is technically conceivable, formal verification of the accuracy of computer systems is still not very prevalent. SeL4 and SYSGO's PikeOS are two operating systems that have undergone rigorous verification, however their share of the market is extremely limited. 
A technique for preventing unauthorised access to a system or sensitive data is two factor authentication. It takes something you have?a card, dongle, mobile, or other piece of hardware?and something you know?a password or PIN. This improves security because it takes both of these for an unauthorised individual to enter. Only non-computer methods, which can be challenging to implement given how sensitive the material is, can stop social engineering and direct computer access (physical) attacks. In order to reduce this risk, training is frequently used, but social engineering attacks can still be challenging to recognise and avoid, especially in highly structured contexts (such as military organisations). The term "inoculation," which comes from the inoculation hypothesis, refers to the process of preventing social engineering and other deceptive tricks or traps by fostering a resistance to persuasion through exposure to previous or comparable attempts. Keeping systems updated with security patches and updates, utilising a security scanner, and/or engaging security experts can all help to lessen an attacker's chances of success, but none of these measures can ensure the prevention of an attack. By taking thorough backups and getting insurance, the effects of data loss or damage can be lessened. Hardware Security Measures:Hardware can be a source of security risks, such as intentionally added microchip flaws during manufacture, while hardware-based or assisted computer security also provides an alternative to software-only computer security. Because physical access (or clever backdoor access) is needed to be compromised, using tools and techniques like dongles, trusted platform modules, intrusion-aware cases, disc locks, turning off USB ports, and mobile-enabled access may be regarded more secure. Below, we go into greater depth on each of these. USB dongles are frequently used in software licencing schemes to unlock programme features, but they can also be considered as a means of preventing unwanted access to a computer or other device's software. Between the key and the software programme, the dongle or key essentially builds a safe encrypted tunnel. According to the underlying theory, using an encryption system like Advanced Encryption Standard (AES) on the dongle offers a higher level of security because it is more difficult to hack and copy the dongle than it is to merely copy the native software to another computer and run it. Using dongles for web-based content access, such as cloud computing or virtual private networks, is another security use (VPNs). Moreover, a computer can be programmed to lock or unlock using a USB dongle.
Operating Systems with Security:The phrase "computer security" can apply to a variety of technologies, including those used to construct secure operating systems. The United States Department of Defence (DoD) continues to apply the "Orange Book" criteria from the 1980s despite the Common Criteria's definition of a succession of ever more stringent Evaluation Assurance Levels in the current international standard ISO/IEC 15408, Common Criteria. Although though many widely used operating systems are "Methodically Designed, Tested, and Reviewed" as defined by the EAL4 standard, they are rare due to the rigorous verification needed for the highest levels. The Airbus A380 and other military aircraft use the INTEGRITY-178B system, a notable example of an EAL6 ("Semiformally Verified Design and Tested") system. Encrypted Coding:Secure coding is a practise in software engineering that seeks to prevent the unintentional introduction of security flaws. Software that is built to be secure from the ground up is also a possibility. By design, these systems are secure. Beyond this, formal verification seeks to establish the accuracy of a system's underlying algorithms, which is crucial for cryptographic protocols, for instance. Access Control Lists and Capability Lists:Access control lists (ACLs) and role-based access control are two of the most common security paradigms used in computer systems for implementing privilege separation (RBAC). A collection of permissions connected to an object is called an access-control list (ACL) in relation to a computer file system. An ACL specifies which system processes or users are permitted access to objects as well as the operations that are permitted on particular objects. In order to restrict authorised users' access to systems, the majority of businesses with more than 500 employees utilise role-based access control, which can be used to create either mandatory access control (MAC) or discretionary access control (DAC). Another strategy is capability-based security, which has generally only been implemented in research operating systems. Yet, it is also possible to incorporate capabilities at the language level, creating a programming paradigm that is simply a more advanced version of the conventional object-oriented architecture. The E language is a project in this field that is open-source. End-User Security Education:More than 90% of security incidents and breaches are thought to include some sort of human error, making the end user the weakest link in the security chain. Poor password management, sending emails with sensitive data and attachments to the incorrect recipient, failing to spot misleading URLs, and failing to spot phoney websites and potentially dangerous email attachments are some of the most frequently reported errors and misjudgments. To make it simpler to log in to banking websites, customers frequently make the error of keeping their user name and password in their browsers. This is a favour given to attackers who have somehow gained access to a computer. By using two-factor authentication, the risk might be reduced. At all levels, security awareness training not only assures formal compliance with industry and regulatory regulations, but is also considered to be essential in lowering cyber risk and protecting people and organisations from the great majority of cyber threats. This is due to the fact that a company's overall cyber risk can be best estimated by including the human element of cyber risk. It moves in the direction recommended by major security centres to create a culture of cyber awareness within the organisation, realising that security-aware users serve as an important first line of defence against cyberattacks. Many security professionals, who historically addressed cybersecurity primarily from a technical standpoint, have experienced a fundamental culture shift as a result of the emphasis on the end-user. Internet Safety:Digital hygiene, often referred to as cyber hygiene, is a key idea related to information security and, as the analogy to personal hygiene shows, is the equivalent of putting into practise simple routine acts to lower the risks from cyber threats. It has to do with end-user training. Effective cyber hygiene practises are supposed to give networked users an extra layer of protection by reducing the likelihood that one vulnerable node might be exploited to launch attacks or compromise another node or network, especially from conventional assaults. Moreover, the military phrase for proactive cyber defence, known as cyber hygiene, should not be confused with it. Cyber hygiene focuses mostly on routine precautions that are technically easy to apply and largely reliant on discipline or education, as opposed to a protection against threats that is entirely technology-based. It can be viewed as an abstract collection of recommendations or safety precautions that have been shown to improve individual and/or group digital security. So, everyone, not just security professionals, can carry out these precautions. The same way that computer viruses relate to biological viruses, personal hygiene has a connection to both (or pathogens). The phrase "computer virus," on the other hand, was created far later?possibly as late as 2000 by Internet pioneer Vint Cerf?than the first functional computer viruses. In contrast, the term "cyber hygiene" was almost exactly coined at the same time. Since then, the FBI, EU institutions, the United States Congress and Senate, and other heads of state have all embraced it. In Response to Violations:It can be exceedingly challenging to respond to attempted security breaches for a number of reasons, including: Attackers may use wireless connections, temporary anonymous dial-up accounts, proxies, and other anonymizing techniques, which make it difficult to track them down. They are also frequently based in another country, making it difficult to identify them. If they are successful in breaching security, they frequently have sufficient administrative access to be able to remove logs in order to hide their tracks. Organizations are unable to devote enough time to each of the many attacks that are undertaken, frequently by automated vulnerability scanners and computer worms. Police personnel frequently lack the knowledge, desire, or resources to pursue attackers. Also, it may be challenging or time-consuming to gather logs from numerous locations across the network and in numerous countries, which are sometimes necessary for the identification of attackers across a network. Many jurisdictions now have required security breach notification regulations in place where an attack is successful and a breach occurs. Planning for Incident Response:In order to avoid a breach or counter a cyberattack, incident response is an organised method of dealing with and managing the fallout from a computer security incident or intrusion. When an incident is not recognised and handled at the time of the intrusion, it frequently worsens and leads to a data breach or system failure. A computer security incident response plan aims to confine the issue, minimise damage, and aid in the return to normal operations. By immediately responding to compromises, exploited vulnerabilities can be reduced, services and processes can be restored, and damages can be kept to a minimum. An organisation can create a set of best practises for stopping an infiltration before it causes damage by using incident response planning. The organization's response to a cyberattack is outlined in a set of written guidelines found in most incident response plans. Without a written plan in place, an organisation may be unable to identify an incursion or compromise, and stakeholders may not be aware of their respective responsibilities or escalation processes, which would delay the organization's ability to respond and resolve the situation. A computer security incident response strategy should include the following four elements:
Significant Attacks and Breaches:Robert Morris and the Original Computer Virus:60,000 machines were linked to the Internet in 1988, with the majority being mainframes, minicomputers, and workstations for professionals. Many began to experience performance issues on November 2, 1988, as a result of executing the first internet computer worm, a malicious programme that ate up processor time and spread to other machines. The software was linked to Robert Tappan Morris, a 23-year-old PhD student at Cornell University who claimed "he wanted to count how many PCs were connected to the Internet." Italian Laboratory:The Rome Laboratory, the principal command and research facility for the US Air Force, was the target of more than a hundred intrusions by unknown crackers in 1994. Hackers were able to enter Rome's networking infrastructure without restriction and erase evidence of their actions using trojan horses. By assuming the identity of a reliable Rome centre user, the intruders were able to access sensitive documents like data from the air tasking order systems and furthermore break into the connected networks of the Wright-Patterson Air Force Base, the Goddard Space Flight Center, the National Aeronautics and Space Administration, some Defense contractors, and other private sector companies. Card Information for a TJX Customer:In the beginning of 2007, the American clothing and home goods firm TJX disclosed that it had been the target of an unlawful computer intrusion and that the hackers had gained access to a system that stored information on credit card, debit card, check, and merchandise return transactions. Attack using Stuxnet:One-fifth of Iran's nuclear centrifuges are said to have been destroyed in 2010 by the Stuxnet computer worm. In order to accomplish this, it launched a targeted attack against industrial programmable logic controllers (PLCs). Despite neither country's public admission, it is widely thought that Israel and the United States initiated Operation in order to thwart Iran's nuclear development. Information on Global Surveillance:Early in 2013, The Washington Post and The Guardian published documents obtained by Edward Snowden that revealed the extensive scope of NSA's global monitoring. There were also hints that the NSA might have added a backdoor to a NIST encryption standard. This requirement was later dropped as a result of strong opposition. Also, it was revealed that the NSA had monitored the connections between Google's data centres. Breaches at Target and Home Depot:In 2013, a Ukrainian hacker by the name of Rescator gained access to Target Corporation servers and stole about 40 million credit card numbers. In 2014, he gained access to Home Depot computers and stole between 53 and 56 million credit card numbers. Warnings were sent to both businesses but went unheeded; physical security vulnerabilities involving self-checkout machines are thought to have played a significant impact. According to Jim Walter, head of threat intelligence operations at security technology company McAfee, the heists might have been easily avoided by administrators if they had heeded the warnings from modern antivirus software. "The malware utilised is absolutely unsophisticated and uninteresting," he says. The enormity of the thefts has drawn significant attention from state and federal authorities in the United States, and an investigation is still underway. Information leak at the Office of Personnel Management:In April 2015, the Office of Personnel Management discovered that a data breach that occurred more than a year earlier had led to the loss of about 21.5 million personnel records that the agency controlled. According to federal officials, the Office of Personnel Management attack was one of the biggest data breaches in American history. the names, dates of birth, addresses, Social Security numbers, and fingerprints of current and past government employees as well as anyone who had completed a background check by the government were among the personally identifiable information that was targeted in the incident. Chinese hackers are thought to have carried out the hack. Ashley Madison Security Hole:A hacker group called as The Impact Team gained access to the extramarital affairs website Ashley Madison in July 2015. The website was created by Avid Life Media. According to the organisation, they also stole user data in addition to corporate data. The Impact Team vowed to release client data unless the website was permanently shut down after the hack, releasing emails from the company's CEO to support their argument. When Avid Life Media chose not to shut down the website, the organisation made two more compressed files available, one 9.7GB in size and the other 20GB. The website continued to operate despite Noel Biderman, the CEO of Avid Life Media, stepping down following the second data leak. International Regulatory and Legal Issues:The legal ramifications of cyberattacks on a global scale are complex. When security firms or agencies do identify the cybercriminal responsible for the development of a specific piece of malware or type of cyberattack, the local authorities frequently are unable to take enforcement action because there are no laws under which to prosecute. As a result, there is no global base of common rules to judge, and ultimately punish, cybercrimes and cybercriminals. For all law enforcement authorities, proving attribution for cybercrimes and cyberattacks is a significant challenge. "Computer viruses move around the world by switching from one nation to another and from one jurisdiction to another. They accomplish this by taking advantage of the fact that we are unable to worldwide police such operations. The Internet is like someone giving free plane tickets to all of the world's internet crooks." Investigation and enforcement are more difficult as a result of the usage of tactics like dynamic DNS, quick flux, and bulletproof servers. Government's Role:The government's job is to enact laws that compel businesses and organisations to safeguard their networks, hardware, and data from cyberattacks. It also has a responsibility to safeguard its own national infrastructure, such as the power grid. It's confusing how the government regulates online activity. As witnessed in many of the libertarian blockchain and bitcoin conversations of today, some people formerly believed that cyberspace was a virtual realm that should be free from government interference. The failure of the private sector to effectively address the cybersecurity issue has led many government officials and experts to believe that the government should be doing more and that improved legislation is urgently needed. R. Clarke said at a panel at the RSA Security Conference in San Francisco that he believes the industry "only behaves in response to threats of regulation. You must follow through if the industry doesn't react (to the threat)." On the other hand, business leaders concur that changes are required, but they believe that governmental interference would limit their capacity for effective innovation. In his analysis of this public-private cooperation in cybersecurity, Daniel R. McCarthy also considered the function of cybersecurity in the larger structure of political order. Conclusion:The obligation to respond rapidly to the steadily rising number of cybersecurity threats is placing organisations under pressure. Organisations were compelled to develop a vulnerability management life cycle because attackers have been employing an attack life cycle. The vulnerability management life cycle is set up to best and most quickly thwart any attempts made by attackers. In terms of the vulnerability management strategy, this chapter has covered the vulnerability management life cycle. It has gone through the construction of an asset inventory process, information flow management, risk assessment, vulnerability assessment, reporting, remediation, and more.
Next TopicDiffusion Definition Biology
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










