HTTPS DefinitionIntroductionHTTPS is a protection-enhanced version of the Hypertext Transfer Protocol (HTTP), an application protocol for all kinds of communication on the web. HTTP facilitates the retrieval of web pages. HTTPS, or HTTP Secure, accomplishes the same function but more securely. HTTPS works by focusing on secure search so that unauthorized users cannot obtain the information they are not allowed to have. In December 2019, Google released information about its latest HTTPS update. Different Methods Used to Make the Data SecureEncryptionEncryption is essential for the security of HTTPS as it executes SSL and TLS. Public-key cryptography and the SSL/TLS handshake ensure that even if someone can access the data you submitted to a website, they cannot read it. Your sensitive information is converted through encryption into an unreadable jumble of characters, symbols, and numbers meaningless to anyone trying to read. 
AuthenticationThe next stage in ensuring data security approaches a website is authentication. The SSL/TLS certificate for a website will contain a public key to confirm that the data sent has been signed digitally by a specific individual using the right private key. This demonstrates that the information is reliable and acceptable. Data IntegrityFiles, photos, or web pages are subject to manipulation by third-party individuals if not properly secured. A website can utilize the digital signature from the original sender provided through HTTPS to verify the authenticity of each document sent through the server. It is possible to examine the document's contents, including its digital certificate, to ensure there hasn't been any data loss during transmission. What is HTTPS?
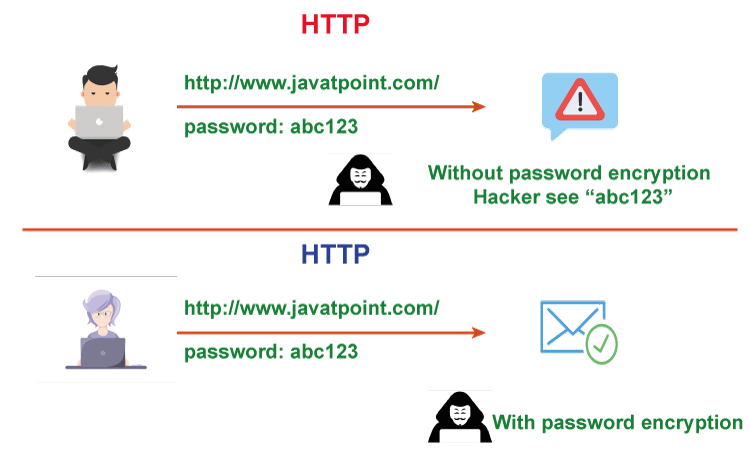
Difference between HTTP and HTTPSWeb users can send and receive information over the Internet with the use of both HTTP and HTTPS. So what makes HTTP and HTTPS different from one another? However, HTTPS is crucial for websites that send sensitive information, such as e-commerce sites where customers enter payment information like credit card numbers, billing addresses, and phone numbers. TLS, formerly known as Secure Sockets Layer (SSL), is a protocol that works with HTTPS to encrypt sensitive data, safeguard against information loss or tampering during transfer, and authenticate specific users to communicate with the website. Fundamentally, HTTPS secures data transfers by generating temporary session keys, or encryption codes, for communication between a user and the website server. The certificate authority like Symantec or Comodo must validate these encryption keys. Email, e-commerce, and other sensitive data transfers were the initial uses for HTTPS. It is now considered the industry standard for all websites, is supported by Google, and is necessary for many cutting-edge features, including advanced web applications. Importance of HTTPSUsing HTTPS is a must for any website dealing with secure information. However, HTTPS can still be useful for websites that don't deal with sensitive data. Google has been one of the leading supporters of HTTPS's universal application in secure search. If you work in e-commerce or finance, provide a SaaS solution, or have any other business model that includes processing sensitive client data online, the security dangers connected with HTTP are real and might have serious repercussions. Most significantly, HTTP can allow an internet service provider (ISP) or another outside actor to actively tamper with pages that site users travel to, changing content or removing page elements. However, in the hands of other parties, this could be used for much more criminal reasons. For example, in the case of ISPs, this is occasionally used to insert advertisements or behavioral tracking cookies for advertisements. Which is more secure, HTTP or HTTPS?HTTPS is safer. A 1999 note from the World Wide Web Consortium, a worldwide web community operated by Jeffrey Jaffe and Tim Berners-Lee, creator of the World Wide Web, reported several unique security factors and the potential attack transmitters linked with HTTP/1.1:
How Does HTTPS Protect Against Cyberattacks?Most data sent from an individual to a website is protected and encrypted by HTTPS. An HTTPS connection encrypts all data sent, including the query string arguments, post bodies, and URL path. Although HTTPS offers an extra layer of security for the data transmitted to and from a website, it is not intended to act as a firewall for the site. The SSL/TLS encryption protects the data transfer, but you should implement additional security measures to secure the other information on your website. Can HTTPS Prevent DNS Spoofing?Domain Name System (DNS) spoofing secretly directs users to a different website than they request. The HTTP Strict Transport Security (HSTS) protocol allows you to force a browser to display your website at all times. A hacker may attempt to create a fake version of your site since it has a secure SSL/TLS certificate. Still, users will be immediately made aware of the security violation. The strongest defense against DNS spoofing is setting up HSTS with HTTPS. Why Are HTTPS and VPN Required Together?Virtual private networks (VPNs) and HTTPS are great website security technologies. When combined, they can offer an even better level of security than you might be able to achieve on your own. Data is passed from a user to the website, and HTTPS secures the reverse. The sensitive data exchanged across websites today require this protection, but it only safeguards that communication channel. A VPN, on the other hand, protects your whole system while shielding your identity and surfing history. You can provide a second layer of security for every user on your network by using HTTPS and a VPN provider. Advantages of HTTPSHTTPS provides multiple benefits over HTTP connections:
Limitations of HTTPSome of the limitations of HTTP are:
How to switch from HTTP to HTTPS?Transform from HTTP to HTTPS in 7 stages:
HTTPS vs. HTTP is a query that has afflicted several website owners as they attempt to stay compliant with Google and offer a secure space for those who visit. How Does HTTPS Work?Cryptographic technologies like TLS or SSL are used on top of HTTP to encrypt and secure each data packet transmitted over an HTTPS connection. The technology used to encrypt communications is called Transport Layer Security (TLS), formerly Secure Sockets Layer (SSL). It is SSL's most recent and secure version. TLS protects against attacks and has three key objectives: privacy, authentication, and general security. An asymmetric key algorithm known as The Public Key Infrastructure, or PKI, is used by TLS to secure communications. This system utilizes two uniquely corresponding keys to encrypt and decrypt important data, allowing secure communication across the Internet. TLS connects the sender and recipient by combining the two keys. It ensures that both parties are recognized and are who they claim to be.
ConclusionIn this article, we learned what HTTPS is, how it functions, and how it differs from HTTP (and is, therefore, more secure). In short, HTTPS refers to the secured version of HTTP, the fundamental network protocol used to transport hypertext over the Internet. Additional security measures, such as TLS/SSL certificates and the TLS/SSL handshake, are used with HTTPS. It offers user and data authentication, ensuring that transactions are kept secure (with data integrity being a priority) without worrying about an information leak during client-server communication. Only the sender and intended recipient can see the contents of texts and transactions.
Next TopicHuman Pulse Definition
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share










