What is a Keystroke?A keystroke is referred to as typing one character on a physical or virtual keyboard or any other input device. In other words, a single keypress (not stroking your keyboard like a cat) on the keyboard is considered a keystroke. You perform a keystroke when you hit a key every time. The keystroke is an important component, which is used for programming purposes in order to respond to the user pressing a special key. The keystroke is considered better for typing speed, hardware, software, acoustic analysis, keystroke logging, and other studies on the basis of human-computer interaction. In one hour, 5400 keystrokes mean hitting 5400 keys; thus, 90 keys a minute is equal to 5400 is divided by 60 (5400 ÷ 60 minutes). When measuring typing speed, keystrokes per minute (KSPM) or keystrokes per hour (KSPH) are frequently used instead of words per minute (WPM). After all, when you write the word "Nebuchadnezzar" 50 times, it will take much time as compared to writing the word "hi" 50 times. Software applications and operating systems proceed with their next actions with the help of keystrokes. Actions and specified events are available in software and operating system-based applications to collect and analyze keystrokes. Furthermore, keystroke rhythm is a behaviour biometric that is unique to an individual on a certain keyboard. It can also be used for security purposes, surveillance and authentication because it is considered a behavior biometric. Typing tutor programs that record keystrokes are examples of software programs that help users to type more quickly with accuracy. Parental control programs are a program that allows parents to keep their eyes on their children to see what they are doing on the computer because these programs can be set up to record keystrokes. Software with keylogging may also be used by schools and businesses to track their student's or employees' activities on the computer or to verify they are not doing any illegal or inappropriate activity on the computer. 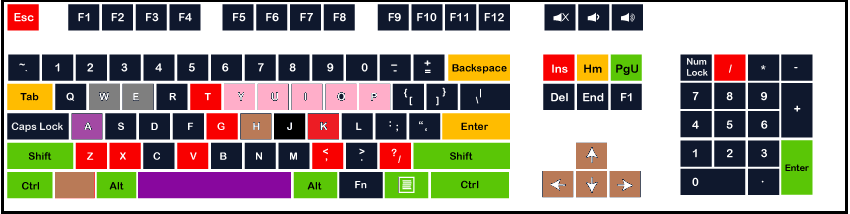
The above keyboard image represents a log of more than 2.5 million keystrokes and shows how frequently each key was pressed. The space and A latter from the keyboard are the most frequent keys, and the keys that are colored with black color are the least frequent. The primary use of keystrokes is to give input. On the other hand, the keystroke is dynamic that can monitor the keyboard inputs thousands of times per second, which helps to measure the typing speed on the basis of the habitual typing rhythm patterns. Keystroke loggingKeystroke logging, also known as keylogging or keyboard capture, is the process of recording the keys pushed by users on a keyboard. Generally, it records covertly through which the person who is using the keyboard is unaware that whatever he is doing on the computer is being monitored. Then the person operating the logging program can retrieve data. Keystroke loggers, or simply keyloggers, can be either software or hardware, which have the ability to offer malevolent actors with a user's personal information like usernames and passwords. This information can be used by the malicious actor to gain unauthorized access to any user accounts, such as social media accounts, user's bank accounts, etc. Although the programs are designed to allow persons to keep their eyes on the use of their computers, these programs are legal. For example, the program may be used by schools and businesses to track their student's or employees' activities on the computer. But keyloggers are also used to steal passwords and other confidential information, which can be much harmful. There are also some keystroke loggers available that have the potential to record the keypresses on virtual keyboards, like the keyboard included by smartphones and tablets. Furthermore, there are various software and hardware-based keylogging methods available for acoustic cryptanalysis. Types of Keystroke LoggersSoftware keyloggers and hardware keyloggers are two kinds of keystroke loggers. The hardware keyloggers, to record the pressed keys on the keyboard, can plug directly into a computer as it is any physical device. A typical hardware key logger, which comes in the shape of a flash drive and records the user's keystrokes in a text file, may be inserted straight into a computer's USB port. The following are the several types of hardware keyloggers:
On the other hand, Software keyloggers are installed on the mobile or computer device. Similar to hardware keyloggers, software keyloggers function to record the keys pressed on the device's keyboard. It also holds the information, which can be accessed by a hacker at a later time. On virtual keyboards, Software keyloggers are widely used to record key information while pressing on the keyboard. Software keyloggers also have some types, which are as follows:
Uses for KeyloggersThere is a need to consider first what are legal keylogger activities to explain the uses of keyloggers. If keylogger use is legally acceptable, there are four factors outlined, which is discussed below:
How Keystroke Logging WorksKeystroke logging is the action of recording the keys pressed by users on the keyboard, often without the permission or knowledge of the user. A keystroke is referred to as typing one character on a physical or virtual keyboard. The working concept of keystrokes are dependent on how you "speak" to your computers. A signal is transmitted by each keystroke that describes to the computer what task you are going them to do. These commands may have:
When keystroke is logged, you will feel all this information like a private conversation. You are thinking lie you are doing conversation only with your device, but it is not, and another person listened and wrote down everything you communicated with your device. In modern times, we share sensitive information on our devices that may be harmful if it has been stolen by any authorized person. When logged, the user's private data and behaviors can be assembled easily. Users enter everything into their computers, such as their social security numbers, online banking access information, email id, and password, which even are saved on their computer that all can be highly revealing. History of keyloggingIn the 1970s, the use of keyloggers started when a hardware keylogging device was developed by the Soviet Union for electric typewriters. The keylogger was known as the selectric bug at the time, and it tracked the motions of the printer by sensing the magnetic field emitted. The Selectric bug was used to eavesdrop on US diplomats in Moscow and St. Petersburg, in the US embassy and consulate facilities. The main objective to develop the electric bug was to target IBM Selectric typewriters. The keyloggers were employed until 1984, when a US ally, who was a distinct target of this operation, discovered the infiltration and keyloggers in 16 typewriters. In 1983, Perry Kivolowitz wrote another early keylogger that was a software keylogger. Since then, in the 1990s, the use of keyloggers has increased. The attackers did not have to install hardware keyloggers as there was more keylogger malware was developed, which allowed attackers to gain secret information from unsuspicious victims remotely. The use of keyloggers began to fraud in different industries and homes as well for phishing purposes. The US Department of Homeland Security began warning hotel operators about keyloggers in 2014 after a keylogger was discovered in hotels in Dallas, Texas. In addition, keyloggers began to target computers in shared settings that were available to the public. A keylogger was hidden in the mod for the game Grand Theft Auto V in 2015. In 2017, a keylogger was discovered in HP laptops, which HP stated was used as a debugging tool for the program. Detection and removalThe single detection or removal method is not considered the best method as there are numerous kinds of keyloggers available that utilize various techniques. To detect a keylogger, only a task manager is not enough because keyloggers have the potential to manipulate an operating system kernel. There are some security software programs have designed that can help to scan keyloggers. An anti-keylogger software tool, for example, is used to scan for software-based keyloggers by comparing files on a computer to a checklist of typical keylogger traits or a keylogger signature base. As compared to using an antispyware or an antivirus program, an anti-keylogger can be more effective as later it may identify a keylogger as a legitimate program rather than spyware. On the basis of the techniques used by the antispyware application, it may be possible easily to locate and disable keylogger software. Because it warns users each time a programme tries to create a network connection, a network monitor allows the security team to block any potential keylogger activity. Protection against keyloggersTo detect hardware keyloggers, although visual inspection can be used, if you implement it on a large scale, it can be time-consuming and impractical. Also, a firewall can be used to identify a keylogger. The firewall has the potential to pick up and prevent data transfer, as the keyloggers transfer data back and forth from the victim to the attacker. Password managers may also help that have the ability to fill the fields of username and password automatically. In favor of preventing keyloggers and keeping the system healthy, antivirus software and monitoring software can also help to resolve it. With the help of installing a system cage to the user's desktop configuration, which prohibits access to or tampering with USB and PS/2 connections, system cages can also assist defend against keyloggers. Using a security token as part of two-factor authentication can give an extra layer of protection by ensuring that an attacker cannot access a user's account using a stolen password or voice-to-text software with an onscreen keyboard to avoid using a physical keyboard.
Next TopicWhat is a Tilde
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









