What is a Regular File?
In computing, a regular file is a type of file that contains user-created data in a specific format. Regular files can be text files, binary files, or any other type containing data that is not a directory or a special file. These files are typically identified by their file extensions or by their content. For example, a text file may have a .txt extension, and a JPEG image file might have a .jpg extension.
However, the file extension is not the only way to identify a regular file. For example, a file with no extension might still be a regular file if its content indicates that it contains data in a specific format.
In Unix-like operating systems, regular files are one of several files that can be created. Other files include directories, special files (device files), and symbolic links. Regular files can be manipulated using various commands and utilities, such as cp, mv, rm, cat, and more.
Regular File Attributes
Regular file attributes describe the file's characteristics, such as its size, permissions, timestamps, and ownership. Here are some common regular file attributes:
- File size:This attribute indicates the file size in bytes, kilobytes, megabytes, or gigabytes.
- Permissions: This attribute specifies the file's read, write, and execute permissions for different users and groups on the system.
- Timestamps:This attribute includes the file's creation time, access time, and modification time. These timestamps indicate when the file was created, last accessed, and last modified.
- File ownership:This attribute indicates the user and group ownership of the file. This information determines which users and groups can access the file.
- File type:This attribute specifies the type of regular files, such as text files, binary files, image files, audio files, video files, and more.
- File location: This attribute specifies the location of the file on the file system, including the directory and path.
- File checksum:This attribute is a unique identifier of the file's contents, calculated using a hashing algorithm. It is often used to verify the file's integrity during backup and transfer.
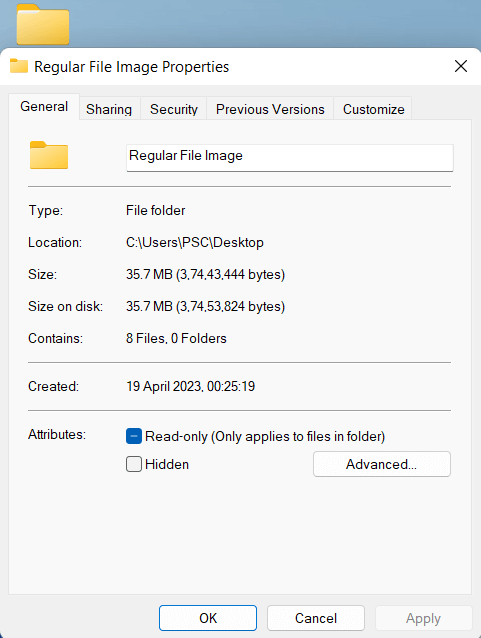
Regular file attributes can be viewed using various tools and commands. Understanding common file attributes can be useful in managing files and troubleshooting issues related to file permissions, ownership, and integrity.
Regular File Formats
Regular files can be saved in various formats depending on the data type. Here are some examples of different file formats for regular files:
Text files:These files contain plain text and are usually saved with a .txt extension. They can be created and edited using text editor software such as Notepad, TextEdit, or Vim.

Image files:These files contain digital images and can be saved in formats such as JPEG, PNG, GIF, TIFF, BMP, and more. Each image format has unique features and benefits depending on its intended use.

Audio files: These files contain digital audio and can be saved in various formats such as MP3, WAV, FLAC, AAC, and more. Each audio format has unique features and benefits depending on its intended use.
Video files: These files contain digital video and can be saved in various formats such as MP4, AVI, MOV, WMV, and more. Each video format has unique features and benefits depending on its intended use.
Compressed files: These files contain one or more files that have been compressed to reduce their size. Some examples of compressed file formats include ZIP, RAR, GZIP, TAR, and more.
Document files: These files contain formatted text, images, and other elements and are typically created using a word processor or desktop publishing software. Examples of document file formats include DOCX, PDF, ODT, and more.

Database files: These files contain structured data organized into tables, fields, and records. Some examples of database file formats include Microsoft Access, MySQL, Oracle, and more.
Note: The format chosen for a regular file will depend on the type of data being stored and the intended use of the file.
Regular File Compression
There are various ways to compress a regular file, and the specific method will depend on the compression algorithm and file format. Here are some common ways to compress a regular file:
- Zip compression: Zip is a popular compression format that can compress regular files and folders. To compress a file using Zip compression, you can use a utility like WinZip, 7-Zip, or the built-in Zip utility in Windows, macOS, or Unix-based systems.
- Gzip compression:Gzip is a Unix-based compression utility that uses the gzip compression algorithm to compress files. To compress a file using Gzip compression, you can use the gzip command-line utility in Unix-based systems.
- Bzip2 compression: Bzip2 is another Unix-based compression utility that uses the Bzip2 compression algorithm to compress files. To compress a file using Bzip2 compression, you can use the bzip2 command-line utility in Unix-based systems.
- Tarball compression: Tarball compression involves combining multiple files into a single archive file and then compressing the archive file using a compression algorithm such as Gzip or Bzip2. To create and compress a tarball archive, you can use the tar command-line utility in Unix-based systems.
- RAR compression: RAR is a proprietary compression format that can be used to compress regular files and folders. To compress a file using RAR compression, you can use a utility like WinRAR or the RAR command-line utility in Windows or Unix-based systems.
- 7z compression:7z is a high-compression format that supports various compression algorithms, including LZMA, LZMA2, and Bzip2. To compress a file using 7z compression, you can use a utility like 7-Zip, PeaZip, or the 7z command-line utility in Windows, macOS, or Unix-based systems.
The compression method will depend on the file format, the desired compression level, and the operating system and utilities available. Choosing the appropriate compression method is important to ensure that the compressed file can be easily opened and decompressed on the intended system.
When a regular file is compressed, its size is reduced, saving storage space and making it easier to transfer or share the file. However, compression can also increase the time required to access the file, as the file must be decompressed before it can be used. Additionally, some compression algorithms may lose quality or data, particularly when used to compress images, audio, or video files.
How to Backup Regular File
There are different ways to back up regular files, but one of the simplest methods is to copy them to an external storage device or cloud storage service. Here are the general steps to follow:
- Connect an external storage device (such as a USB drive or external hard drive) to your computer or sign up for a cloud storage service (such as Google Drive or Dropbox).
- Locate the file you want to back up. This can be done by browsing your files or using the search function.
- Right-click on the file and select "Copy" or "Cut."
- Open the external storage device or cloud storage service and create a new folder to store your backups.
- Right-click on the folder and select "Paste" to copy the file to the backup location.
- Repeat the process for any other files you want to back up.
- Once you have finished backing up your files, safely eject the external storage device or ensure your cloud storage service has completed syncing.
Regular file backup is important for protecting your data, ensuring business continuity, and complying with regulations. By establishing a reliable backup strategy, you can reduce the risk of data loss and ensure that your important files are always available when you need them. Backups should be done regularly to ensure that the most current versions of the files are available. Additionally, backups should be stored in a safe location to protect against theft, fire, or other disasters.
How to View and Change Regular File Permissions
In Windows, you can view and change regular file permissions using the following steps:
- Right-click on the regular file whose permissions you want to view or change, and select "Properties" from the context menu.
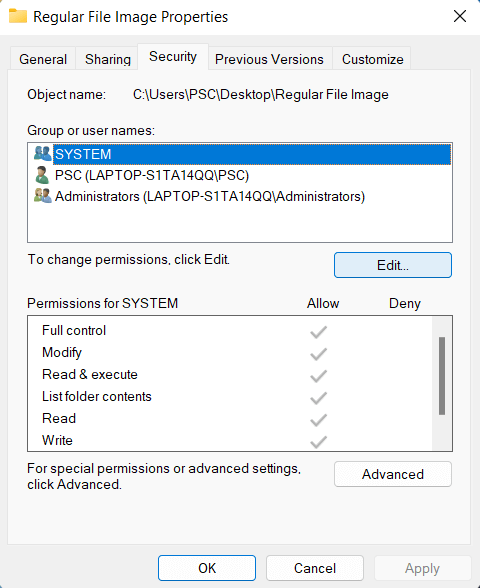
- In the "Properties" window, select the "Security" tab.
- The "Security" tab displays a list of user accounts and groups with permission to access the file. To view the permissions for a specific user or group, select it from the list and click the "Edit" button.
In the "Permissions for [user/group]" window, you can view and change the selected user or group
permissions. The available permissions include "Full Control," "Modify," "Read & execute," "Read," and "Write." To change the permissions for a user or group, check or uncheck the boxes next to the desired permissions, and click the "OK" button to save the changes.
Note: In Windows, file permissions are based on user accounts and groups, and can be more complex than in Unix-like systems. Changing file permissions can have security implications, so it should be done carefully and only by authorized users.
Different File Encryption Techniques
There are various file encryption techniques that are used to secure files and prevent unauthorized access. Here are some commonly used techniques:
- Symmetric-key encryption: In this technique, the same key is used for both encryption and decryption of the file. The data is encrypted with a secret key and decrypted with the same key. Examples of symmetric-key encryption include AES, DES, and Blowfish.
- Asymmetric-key encryption: In this technique, two keys are used, one for encryption and the other for decryption. The public key is used for encryption, and the private key is used for decryption. Examples of asymmetric-key encryption include RSA, DSA, and ECDSA.
- Password-based encryption: This technique uses a password to encrypt and decrypt the file. The password is used as a key to encrypt and decrypt the file. Examples of password-based encryption include ZIP encryption and RAR encryption.
- File-level encryption: This technique encrypts the entire file, including its contents and metadata. This technique is useful for securing sensitive files and preventing unauthorized access. Examples of file-level encryption include BitLocker, FileVault, and VeraCrypt.
- Cloud-based encryption: This technique encrypts the files before uploading them to the cloud. The files are encrypted on the client side and then uploaded to the cloud. This technique is useful for securing files that are stored in the cloud. Examples of cloud-based encryption include Boxcryptor, Cryptomator, and Tresorit.
Each technique has its own advantages and disadvantages, and the choice of technique depends on the specific security needs of the file and the user.
Basic Operations on Regular File
Basic file operations include creating, opening, reading, writing, moving, copying, renaming, and deleting files. Here is a brief overview of each operation:
- Creating a file: This operation involves creating a new file with a specified name and location on the file system. This can be done using a file manager or a command-line tool.
- Opening a file: To open a file, the file must first exist on the file system. Opening a file allows reading or writing its contents. A file can be opened using a file manager or a command-line tool.
- Reading a file: To read the contents of a file, it must be opened for reading. The contents can be read using a file manager or a command-line tool, displayed on the screen, saved to another file, or processed in some other way.
- Writing to a file: To write to a file, it must be opened for writing. The contents can be written using a file manager or a command-line tool and can be added to the end of the file or overwritten the existing contents.
- Moving a file: Moving a file involves changing its location on the file system. This operation can be done using a file manager or a command-line tool and may require permission to access the source and destination directories.
- Copying a file: Copying a file creates a new one with the same contents as the original one. This operation can be done using a file manager or a command-line tool and may require permission to access the source and destination directories.
- Renaming a file: Renaming a file involves changing its name while keeping its contents and location on the file system. This operation can be done using a file manager or a command-line tool and may require permission to access the file and directory.
- Deleting a file: Deleting a file removes it from the file system. This operation can be done using a file manager or a command-line tool and may require permission to access the file and directory.
|








 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now










