What is a Security Question?A security question is a method of authentication used by online services and websites to verify the identity of a user during the account recovery process. When a user forgets their password or encounters difficulty accessing their account, they may be prompted to answer a security question to prove their identity. Typically, during the account creation or setup process, users are asked to choose a security question and provide an answer. Common security questions might inquire about personal information, such as the user's first pet's name, mother's maiden name, or the city where they were born. 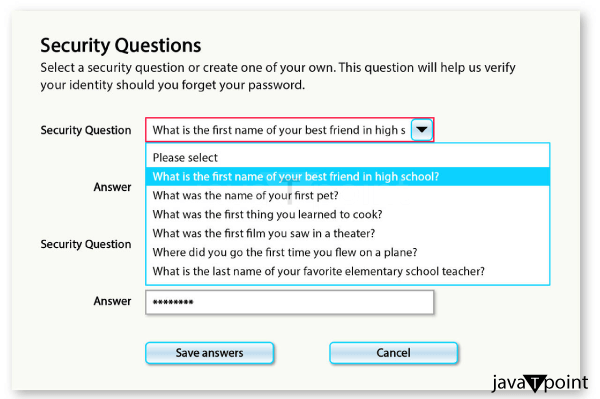
The idea is that the answers to these questions are known only to the legitimate account owner, adding layer of security when trying to regain access to an account. However, security questions have faced criticism for being vulnerable to social engineering attacks, as some information may be publicly available or easily guessed. As a result, some online services are moving towards more secure methods of account recovery, such as two-factor authentication or recovery codes. These questions typically ask for personal information that, ideally, only the account owner should know. However, as mentioned earlier, the use of security questions has been criticized for being potentially insecure, as some answers can be easily obtained or guessed. It's often recommended to use alternative methods of authentication, such as two-factor authentication, to enhance account security. Security questions are a form of authentication that has been commonly used by online services to verify the identity of users during account recovery processes. The primary purpose is to provide a secondary means of access in case a user forgets their password or encounters difficulties logging into their account. However, it's essential to note that the effectiveness of security questions has been debated, and some experts argue that they may introduce security vulnerabilities. Examples of Security Questions
Choosing Strong Security Questions
Purpose of Security QuestionsAccount Recovery: Security questions serve as a secondary authentication method primarily for account recovery purposes. When users forget their passwords or lose access to their accounts, correctly answering these questions can help them regain entry. Additional Layer of Security: Security questions are designed to add an extra layer of security beyond just a password. By requiring knowledge of specific personal information, they aim to ensure that the person attempting to recover the account is the legitimate owner. Protecting Against Unauthorized Access: Security questions are intended to thwart unauthorized access to user accounts by ensuring that only the legitimate account owner, who presumably knows the answers to the selected questions, can initiate the account recovery process. Enhancing Account Security: While not foolproof, security questions are designed to strengthen overall account security by introducing an extra step beyond password protection. This is especially important in cases where users may forget their passwords or encounter situations necessitating account recovery. User Verification: Security questions are a way for online services to verify the identity of users, particularly when the standard login credentials are unavailable or forgotten. This process helps prevent unauthorized individuals from posing as the account owner. Note: While security questions have been widely used, they are not without criticism. Issues such as predictability, guessability, and the potential availability of personal information have raised concerns about their effectiveness. As a result, some online services are exploring more advanced authentication methods, such as biometrics and two-factor authentication, to further enhance security. User Education regarding Security Questions:
Advantages of Security QuestionsWhile security questions have been a common method for account recovery and additional authentication, it's essential to note that they come with both advantages and disadvantages. Here are some advantages of using security questions:
While these advantages exist, it's essential to balance them with the potential drawbacks of security questions, such as the risk of predictability, the static nature of the information, and the increasing prevalence of more secure authentication methods like two-factor authentication. The effectiveness of security questions depends on the implementation and the specific security needs of the platform or service. Concerns and Criticisms of Security Questions
Alternatives and Evolving Practices
ConclusionIn conclusion, security questions have played a longstanding role in online authentication, primarily serving as a means for users to recover access to their accounts. Despite their advantages in user-friendliness, accessibility, and low implementation costs, security questions face significant criticisms and challenges. The static nature of personal information used in security questions poses a risk, as answers can be predictable, easily guessable, or even publicly available. This vulnerability undermines their effectiveness as a robust security measure. Furthermore, the evolving landscape of cybersecurity has prompted a shift toward more advanced and secure authentication methods, such as two-factor authentication and biometrics.
Next TopicWhat is YouTube
|
 For Videos Join Our Youtube Channel: Join Now
For Videos Join Our Youtube Channel: Join Now
Feedback
- Send your Feedback to [email protected]
Help Others, Please Share









